A forensic evaluation of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters affiliated with illicit exercise and funds laundering, which include detecting prison proceeds sent to a crypto exchange and formerly mysterious wallets belonging to a Russian darknet sector.
The results appear from Elliptic in collaboration with researchers from the MIT-IBM Watson AI Lab.
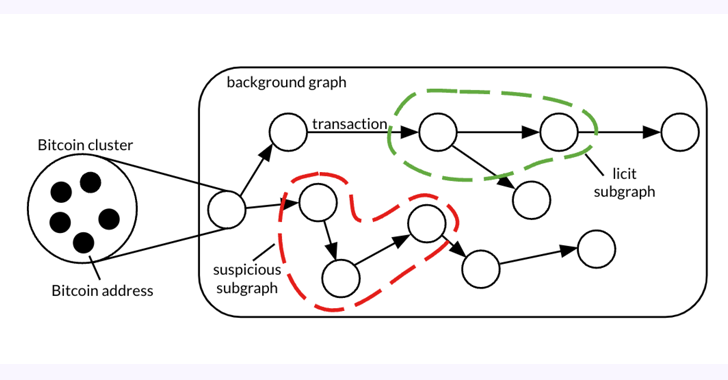
The 26 GB dataset, dubbed Elliptic2, is a “massive graph dataset containing 122K labeled subgraphs of Bitcoin clusters in a history graph consisting of 49M node clusters and 196M edge transactions,” the co-authors explained in a paper shared with The Hacker News.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Elliptic2 builds on the Elliptic Data Established (aka Elliptic1), a transaction graph that was manufactured public in July 2019 with the objective of combating economical crime making use of graph convolutional neural networks (GCNs).

The notion, in a nutshell, is to uncover illicit activity and dollars laundering styles by having benefit of blockchain’s pseudonymity and combining it with understanding about the presence of licit (e.g., exchange, wallet supplier, miner, and many others.) and illicit expert services (e.g., darknet marketplace, malware, terrorist companies, Ponzi plan, and so forth.) on the network.
“Working with machine studying at the subgraph degree – i.e., the teams of transactions that make up circumstances of cash laundering – can be helpful at predicting whether or not crypto transactions represent proceeds of crime,” Tom Robinson, main scientist and co-founder of Elliptic, instructed The Hacker News.
“This is various to traditional crypto AML alternatives, which count on tracing resources from recognized illicit wallets, or sample-matching with regarded money laundering procedures.”
The study, which experimented with 3 distinct subgraph classification strategies on Elliptic2, these types of as GNN-Seg, Sub2Vec, and GLASS, identified subgraphs that represented crypto trade accounts most likely engaged in illegitimate exercise.
Also, it has manufactured it feasible to trace back the resource of money involved with suspicious subgraphs to a variety of entities, like a cryptocurrency mixer, a Panama-centered Ponzi plan, and an invite-only Russian dark web forum.
Robinson explained just taking into consideration the “shape” – the community constructions in just a elaborate network – of the funds laundering subgraphs proved to be an now successful way to flag legal exercise.

More assessment of the subgraphs predicted working with the educated GLASS model has also discovered identified cryptocurrency laundering patterns, these kinds of as the existence of peeling chains and nested companies.
“A peeling chain is exactly where a modest total of cryptocurrency is ‘peeled’ to a spot address, though the remainder is sent to yet another address less than the user’s manage,” Robinson discussed. “This happens regularly to form a peeling chain. The pattern can have legit economic privacy uses, but it can also be indicative of cash laundering, especially where the ‘peeled’ cryptocurrency is frequently despatched to an exchange support.”
“This is a identified crypto laundering procedure and has an analogy in ‘smurfing’ within just classic finance – so the point that our machine finding out manner independently identified it is encouraging.”
As for the following ways, the research is envisioned to focus on rising the precision and precision of these approaches, as perfectly as extending the get the job done to even more blockchains, Robinson additional.
Discovered this post interesting? Abide by us on Twitter and LinkedIn to study far more exceptional content material we article.
Some pieces of this write-up are sourced from:
thehackernews.com

 Android Malware Wpeeper Uses Compromised WordPress Sites to Hide C2 Servers
Android Malware Wpeeper Uses Compromised WordPress Sites to Hide C2 Servers