Cybersecurity scientists have learned an intricate multi-phase attack that leverages bill-themed phishing decoys to provide a vast assortment of malware these as Venom RAT, Remcos RAT, XWorm, NanoCore RAT, and a stealer that targets crypto wallets.
The email messages come with Scalable Vector Graphics (SVG) file attachments that, when clicked, activate the infection sequence, Fortinet FortiGuard Labs reported in a technological report.
The modus operandi is notable for the use of the BatCloak malware obfuscation motor and ScrubCrypt to provide the malware in the sort of obfuscated batch scripts.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
BatCloak, provided for sale to other threat actors given that late 2022, has its foundations in a different software known as Jlaive. Its primary attribute is to load a following-phase payload in a way that circumvents standard detection mechanisms.

ScrubCrypt, a crypter that was to start with documented by Fortinet in March 2023 in link with a cryptojacking campaign orchestrated by the 8220 Gang, is assessed to be a single of the iterations of BatCloak, in accordance to study from Pattern Micro previous year.
In the newest campaign analyzed by the cybersecurity company, the SVG file serves as a conduit to fall a ZIP archive that consists of a batch script most likely designed applying BatCloak, which then unpacks the ScrubCrypt batch file to ultimately execute Venom RAT, but not before environment up persistence on the host and using techniques to bypass AMSI and ETW protections.
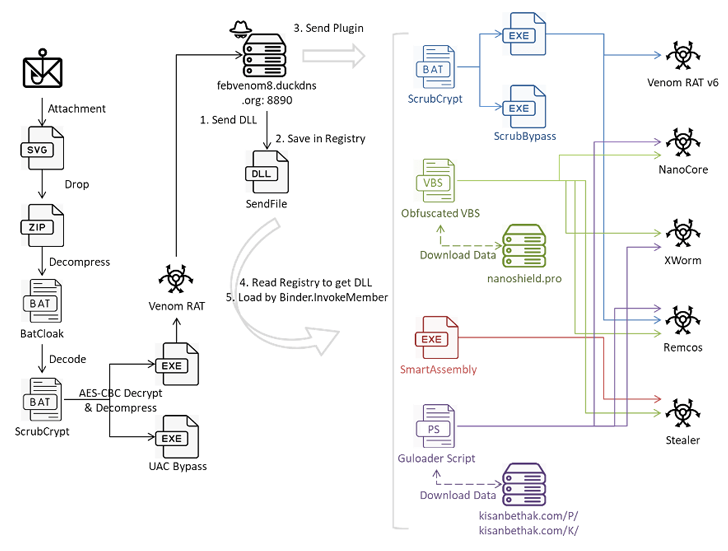
A fork of Quasar RAT, Venom RAT will allow attackers to seize command of the compromised units, get sensitive details, and execute instructions been given from a command-and-handle (C2) server.
“Although Venom RAT’s principal system could show up easy, it maintains interaction channels with the C2 server to purchase added plugins for various pursuits,” security researcher Cara Lin reported. This contains Venom RAT v6..3 with keylogger capabilities, NanoCore RAT, XWorm, and Remcos RAT.
“This [Remcos RAT] plugin was dispersed from VenomRAT’s C2 employing three strategies: an obfuscated VBS script named ‘remcos.vbs,’ ScrubCrypt, and Guloader PowerShell,” Lin extra.

Also delivered working with the plugin system is a stealer that gathers information about the program and exfiltrates details from folders connected with wallets and applications like Atomic Wallet, Electrum, Ethereum, Exodus, Jaxx Liberty (retired as of March 2023), Zcash, Foxmail, and Telegram to a distant server.
“This investigation reveals a advanced attack leveraging many levels of obfuscation and evasion procedures to distribute and execute VenomRAT by way of ScrubCrypt,” Lin mentioned.
“The attackers use a variety of techniques, which include phishing email messages with destructive attachments, obfuscated script information, and Guloader PowerShell, to infiltrate and compromise victim programs. Additionally, deploying plugins via diverse payloads highlights the flexibility and adaptability of the attack campaign.”
Observed this write-up fascinating? Adhere to us on Twitter and LinkedIn to examine more exceptional content we article.
Some components of this post are sourced from:
thehackernews.com


 Critical Flaws Leave 92,000 D-Link NAS Devices Vulnerable to Malware Attacks
Critical Flaws Leave 92,000 D-Link NAS Devices Vulnerable to Malware Attacks