2023 CL0P Development
Rising in early 2019, CL0P was 1st introduced as a a lot more superior edition of its predecessor the ‘CryptoMix’ ransomware, brought about by its operator CL0P ransomware, a cybercrime organisation. About the decades the team remained active with important strategies during 2020 to 2022. But in 2023 the CL0P ransomware gang took alone to new heights and became one of the most active and prosperous ransomware businesses in the globe.
Capitalizing on many vulnerabilities and exploits for some of the world’s largest companies. The presumed Russian gang took its name from the Russian term “klop,” which translates to “mattress bug” and is normally published as “CLOP” or “cl0p”. The moment their victims’ documents are encrypted, “.clop” extensions are extra to their documents.
CL0P’s Approaches & Methods
The CL0P ransomware gang (carefully affiliated with the TA505. FIN11, and UNC2546 cybercrime groups) was renowned for their particularly damaging and aggressive campaigns, which qualified substantial businesses about the environment throughout 2023. The “large sport hunter” ransomware gang utilized the “steal, encrypt and leak” strategy on quite a few large corporations with a specific desire for those in the Finance, Manufacturing and Healthcare industries.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
CL0P operates a Ransomware-as-a-Provider model (RaaS), which routinely employs the ‘steal, encrypt, and leak’ practices common globally between many ransomware affiliates. If its victims fall short to fulfill the needs, their info is printed by means of the gang’s Tor-hosted leak site recognized as ‘CL0P^_-LEAKS’. Just like lots of other Russian-talking cyber gangs, their ransomware was not able to work on units positioned in the CIS (Commonwealth of Independent States).
LockBit also operates as a Ransomware-as-a-services (RaaS) product.
‘In brief, this indicates that affiliate marketers make a deposit to use the software, then split the ransom payment with the LockBit group. It has been claimed that some affiliates are obtaining a share as substantial as 75%. LockBit’s operators have posted commercials for their affiliate system on Russian-language prison forums stating they will not function in Russia or any CIS international locations, nor will they do the job with English-speaking developers until a Russian-talking “guarantor” vouches for them.’ – ‘The Prolificacy of LockBit Ransomware’
SecurityHQ’s Global Danger Landscape2024 Forecast talked about CL0P’s resurgence in the ransomware landscape and just one to be on the lookout for in 2024.
3rd Most Prolific Group 2023
Following examining the facts from ‘CL0P^_-LEAKS’, the threat intelligence workforce at SecurityHQ was in a position to acquire knowledge on many cybercrime gangs all-around the earth and support visualize the extent of CL0P’s increase in action all over 2023. The gangs’ transition from remaining exterior the topmost energetic ransomware groups in 2022 to securing the third most prolific in 2023 is a little something that really should not be taken evenly.
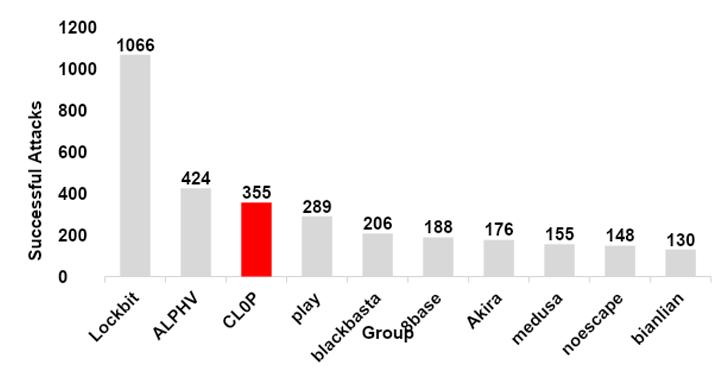 ©2024 SecurityHQ, SecurityHQ Knowledge on Threat Groups All through 2023
©2024 SecurityHQ, SecurityHQ Knowledge on Threat Groups All through 2023
Most up-to-date Things to do
Above a thirty day period-prolonged period of time in the course of March of 2023, the CL0P ransomware gang attempted to exploit ‘Fortra GoAnywhere MFT’ zero-working day vulnerability. Tracked as CVE-2023-0669, attackers were equipped to capitalize on unpatched versions of the software with internet entry to attain RCE. The vulnerability was patched the next day, but the team had already correctly targeted above 100 organisations.
Then, in April, Microsoft was able to establish the involvement of two ransomware gangs (CL0P and LockBit) who had been exploiting the tracked CVE-2023-27350 and CVE-2023-27351. Contained inside of the print administration software program recognized as PaperCut, which is a typical tool made use of amongst all the huge printing corporations worldwide. The teams ended up able to exploit this vulnerability, successfully deploying the infamous TrueBot malware that had been applied a lot of months prior. A great concentrate on for the likes of CL0P, whose strategies have shifted from not just encrypting the data files anymore but additional toward stealing the data to additional extort the organisations. This labored correctly as Papercut capabilities a “Print Archiving” device that will save any work/document that is despatched via their server.
The group’s big event came in Could the commonly used MOVEit Transfer (CVE-2023-24362) and MOVEit Cloud Program (CVE-2023-35036) ended up actively exploited by using an unknown SQL injection vulnerability. CL0P was in a position to capitalize on susceptible networks and programs extremely promptly, extracting sensitive knowledge from some of the world’s major organizations (BBC, Ernst Younger, PwC, Gen Electronic, British Airways, TFL, Siemens, and a lot of extra). The team stated they had deleted all details relating to governments, army, and hospitals, but with various US government organizations getting affected by the MOVEit breach, a bounty of $10 million was set in spot that could help backlink them to a international agent.
Long lasting Influence of Quadruple Extortion
The team has not only played a big position on the influx in ransomware activity all through 2023 but was virtually solitary handedly dependable for the drastic raise in the regular ransomware payments.
CL0P’s operators are renowned for heading to severe lengths to get their message throughout. After publicly displaying the evidence of the organisations breach, publishing knowledge on their leak site and their messages staying ignored, they will go straight to stakeholders and executives to be certain their calls for are achieved. This is identified as quadruple extortion.
From one to double, double to triple and now the development to quadruple extortion, it is reasonable to say ransomware groups usually are not halting until eventually they get what they came for. Just like the double or triple extortion, quadruple extortion adds a new layer which arrives in the kind of two principal avenues.
Most effective Defense In opposition to CL0P Group Defending Against CL0P
To protect against CLOP all over 2024, it is advisable by SecurityHQ to
- Pay back awareness to your landscape and your ecosystem. Know what is regular for your setting and what is not so you can act rapidly.
- Acquire and overview your Incident Reaction Plan, with very clear methods shown so that actions are established in the party of a worst-situation state of affairs.
- Make sure that Danger Monitoring is in place to establish threats rapidly.
- Evaluate present cyber security procedures to make positive that the greatest procedures are being employed.
- All those at higher risk, for occasion, these in industries precisely focused by CLOP (Finance, Manufacturing, Healthcare), or individuals that hold delicate knowledge, really should work with an MSSP to make certain that the best security tactics are in place.
Risk Intelligence for the Long run
SecurityHQ’s Risk Intelligence group is a cohesive global device focused to Cyber Threat Intelligence. Their group is focused on studying rising threats and monitoring activities of threat actors, ransomware teams, and campaigns to make certain that they continue to be ahead of likely risks. Over and above their investigative do the job, the Intelligence crew offers actionable danger intelligence and investigate, enriching the understanding of SecurityHQ’s clients around the globe. United by a frequent dedication, the SecurityHQ Threat Intelligence workforce delivers the insights necessary to navigate the intricacies of the cyber security danger landscape confidently.
For extra details on these threats, converse to an pro below. Or if you suspect a security incident, you can report an incident here.
Notice: This expertly contributed report is penned by Patrick McAteer, Cyber Risk Intelligence Analyst at SecurityHQ Dubai, excels in examining evolving cyber threats, identifying challenges, and crafting actionable intelligence stories to empower proactive defense.
Identified this posting intriguing? This write-up is a contributed piece from a single of our valued partners. Comply with us on Twitter and LinkedIn to examine much more exceptional content material we put up.
Some elements of this report are sourced from:
thehackernews.com


 Attackers Using Obfuscation Tools to Deliver Multi-Stage Malware via Invoice Phishing
Attackers Using Obfuscation Tools to Deliver Multi-Stage Malware via Invoice Phishing