Employee offboarding is no one’s most loved endeavor, nonetheless it is a critical IT course of action that wants to be executed diligently and successfully. That’s simpler mentioned than performed, especially thinking about that IT corporations have considerably less visibility and management above employees’ IT use than at any time. Today, personnel can quickly adopt new cloud and SaaS programs every time and where ever they want, and the aged IT offboarding playbook of “disable Advertisement account, forward email, recover and wipe machine, and connect with it a working day” is no longer enough.
Here, we are going to go over five of the most frequent pitfalls of IT offboarding in a SaaS-initial globe, together with suggestions on how to navigate around them.
Pitfall #1: Suspending or deleting the email account ahead of completing other critical steps
It may well look sensible to suspend or delete the employees’ Google Workspace or Microsoft 365 account as the initially move in the offboarding procedure. Nonetheless, this will make the account inaccessible to every person, even admins, which could interfere with your capacity to total other offboarding duties like transferring information and facts.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
As an alternative of suspending or deleting the account, you’ll want to revoke the previous employee’s access to their email account by resetting their passwords and turning off any restoration solutions the staff had established up, these kinds of as a secondary private email tackle or cell variety.
Analyzing when to suspend or delete the employees’ email account will count on internal protocol, and really should be thoroughly completed only right after confirming that entry to all other critical means, techniques and facts have been revoked or transferred to other staff members. Normally, this will be the remaining move in the IT offboarding approach.
Pitfall #2: Looking at only what is actually in IdP or SSO
1 of the most common offboarding pitfalls is limiting the scope to only the sanctioned cloud and SaaS purposes that are managed inside of your identity company (IdP) or company solitary indicator-on method (SSO.) Even though it seems logical to design and style an offboarding process with a solitary identification kill-change, the reality we all are living with is that not all the things is at the rear of SSO, and by narrowing your scope, you risk overlooking all of the unsanctioned or “shadow” SaaS assets an employee introduced all through their tenure. Such unsanctioned SaaS accounts are usually produced with a username and password, which can simply stroll out the door on a Put up-it take note or be left deserted and later compromised by a menace actor. To avoid this pitfall, start off by opening the aperture of your IT offboarding to encompass all managed and unmanaged cloud and SaaS accessibility.
So, how do you build a list of the unmanaged cloud and SaaS accounts for a departing staff? This can flip into the world’s worst scavenger hunt, with you having to cross-reference information and facts from finance devices, your support desk ticketing system, inquiries to software proprietors exterior of IT, teammates of the departing employee, and additional.
But really don’t embark on that hunt yet, new answers for SaaS administration are emerging to make this approach a whole ton easier.
Pitfall #3: Overlooking company-critical cloud and SaaS sources
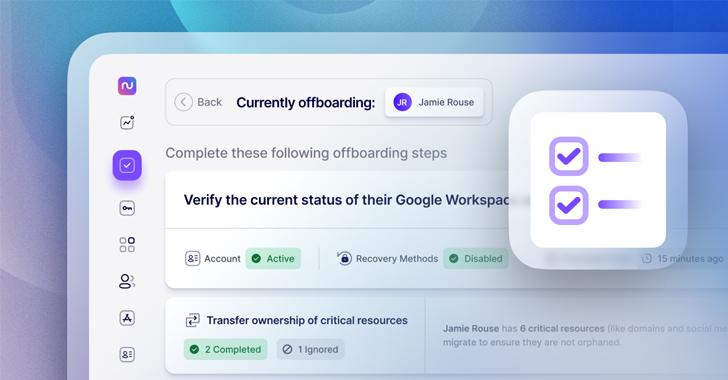
It is easy to overlook to transfer the ownership of critical means like company social media accounts, root account possession, and registered domains. This slip-up can lead to business enterprise disruption or go away accounts orphaned and inaccessible. To ensure this does not transpire, IT companies really should be sure to discover and transfer ownership of any organization-critical means, automations, or integrations as an early stage of the offboarding procedure.
Pitfall #4: Not involving the company entrepreneurs of each and every SaaS application
The fast rise of company-led IT suggests that much more IT administration is taking place outdoors of central IT. This implies more people today to interact in the offboarding method, which include application enterprise house owners and business technologists who take care of the budgets and licenses for their SaaS programs.
There are two key measures to simplifying this course of action: first, you have to know who the suitable people are to engage, which necessitates a robust SaaS management system. Second, you need a way to streamline and even automate engagement with all stakeholders in purchase to effectively orchestrate the multitude of offboarding jobs that non-IT directors need to full.
For case in point, just before the departing employee’s account in a distinct application is shut down, the application business enterprise proprietor may well will need to transfer possession of info, integrations, or workflows to stay clear of disrupting the business enterprise. Additionally, the app proprietor may well need to transfer any elevated permissions to a new person.
Pitfall #5: Overlooking app-to-application OAuth integrations
In most corporations right now,a web of app-to-application OAuth integrations exists in purchase to automate info updates and responsibilities throughout apps. When staff members leave the organization, revoking grants without very careful evaluation could lead to organization disruption, and not revoking grants could guide to amplified risk.
As a final result, it can be critical to assessment OAuth grants, do the job with application entrepreneurs to identify any that will need to be reinstated by using a diverse account, and then revoke the grants issued by the departing employee’s accounts.
Automate SaaS offboarding with Nudge Security
IT offboarding is tiresome, time-consuming and normally incomplete. But, Nudge Security can make this approach a lot much easier.
Nudge Security continually discovers and inventories all the SaaS and cloud purposes your workers are using, together with shadow IT, offering you a one supply of fact for a departing users’ accounts, OAuth grants, and other critical means. And, the developed-in offboarding playbook automates up to 90% of manual duties like resetting passwords, revoking OAuth grants, messaging software house owners to transfer details and permissions, and a lot more.
See how you can automate IT offboarding with Nudge Security.
Found this article intriguing? Stick to us on Twitter and LinkedIn to go through additional exclusive content material we put up.
Some parts of this write-up are sourced from:
thehackernews.com

 N-Able’s Take Control Agent Vulnerability Exposes Windows Systems
N-Able’s Take Control Agent Vulnerability Exposes Windows Systems