Additional facts have emerged about a botnet termed AVRecon, which has been noticed earning use of compromised compact business office/house place of work (SOHO) routers as portion of a multi-year campaign lively due to the fact at the very least Might 2021.
AVRecon was initial disclosed by Lumen Black Lotus Labs before this thirty day period as malware capable of executing extra commands and stealing victim’s bandwidth for what seems to be an unlawful proxy assistance manufactured accessible for other actors. It has also surpassed QakBot in terms of scale, acquiring infiltrated around 41,000 nodes found throughout 20 international locations throughout the world.
“The malware has been utilized to generate residential proxy expert services to shroud destructive action this kind of as password spraying, web-visitors proxying, and ad fraud,” the scientists mentioned in the report.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This has been corroborated by new results from KrebsOnSecurity and Spur.us, which final 7 days disclosed that “AVrecon is the malware engine driving a 12-12 months-previous services termed SocksEscort, which rents hacked residential and modest small business units to cybercriminals hunting to disguise their genuine locale on the web.”
The basis for the link stems from immediate correlations in between SocksEscort and AVRecon’s command-and-management (C2) servers. SocksEscort is also explained to share overlaps with a Moldovan business named Server Administration LLC that presents a cell VPN option on the Apple Retail store named HideIPVPN.
Black Lotus Labs explained to The Hacker News that the new infrastructure it recognized in relationship with the malware exhibited the exact same characteristics as the outdated AVrecon C2s.
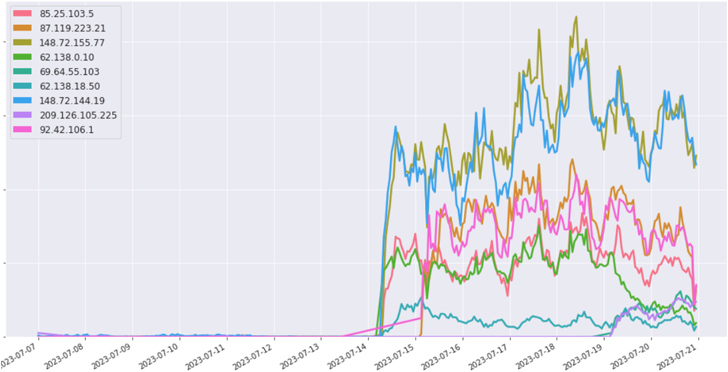
“We assess that the menace actors were being reacting to our publication and null-routing of their infrastructure, and trying to preserve command in excess of the botnet,” the corporation mentioned. “This indicates the actors wish to even more monetize the botnet by preserving some entry and proceed enrolling buyers in the SocksEscort ‘proxy as a company.'”
Routers and other edge appliances have develop into beneficial attack vectors in modern several years owing to the truth that these types of equipment are occasionally patched versus security issues, could not aid endpoint detection and response (EDR) alternatives, and are made to handle greater bandwidths.
Upcoming WEBINARShield Versus Insider Threats: Learn SaaS Security Posture Management
Fearful about insider threats? We’ve got you lined! Be a part of this webinar to investigate sensible procedures and the secrets of proactive security with SaaS Security Posture Management.
Sign up for These days
AVRecon also poses a heightened danger for its ability to spawn a shell on a compromised equipment, probably enabling risk actors to obfuscate their individual destructive website traffic or retrieve further more malware for write-up-exploitation.
“Though these bots are generally being added to the SocksEscort proxy provider, there was embedded operation within just the file to spawn a remote shell,” the researchers stated.
“This could make it possible for the threat actor the means to deploy added modules, so we suggest that managed security providers endeavor to investigate these devices in their networks, even though house users really should power-cycle their gadgets.”
Identified this posting interesting? Observe us on Twitter and LinkedIn to browse far more distinctive material we article.
Some parts of this posting are sourced from:
thehackernews.com


 Fruity Trojan Uses Deceptive Software Installers to Spread Remcos RAT
Fruity Trojan Uses Deceptive Software Installers to Spread Remcos RAT