Threat actors are generating pretend web-sites hosting trojanized computer software installers to trick unsuspecting end users into downloading a downloader malware termed Fruity with the goal of putting in distant trojans instruments like Remcos RAT.
“Among the the application in problem are various instruments for wonderful-tuning CPUs, graphic playing cards, and BIOS Personal computer hardware-checking resources and some other apps,” cybersecurity seller Doctor Web stated in an assessment.
“This kind of installers are applied as a decoy and include not only the software possible victims are intrigued in, but also the trojan itself with all its elements.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The precise preliminary obtain vector applied in the campaign is unclear but it could possibly assortment from phishing to drive-by downloads to destructive ads. End users who land on the pretend web-site are prompted to download a ZIP installer deal.
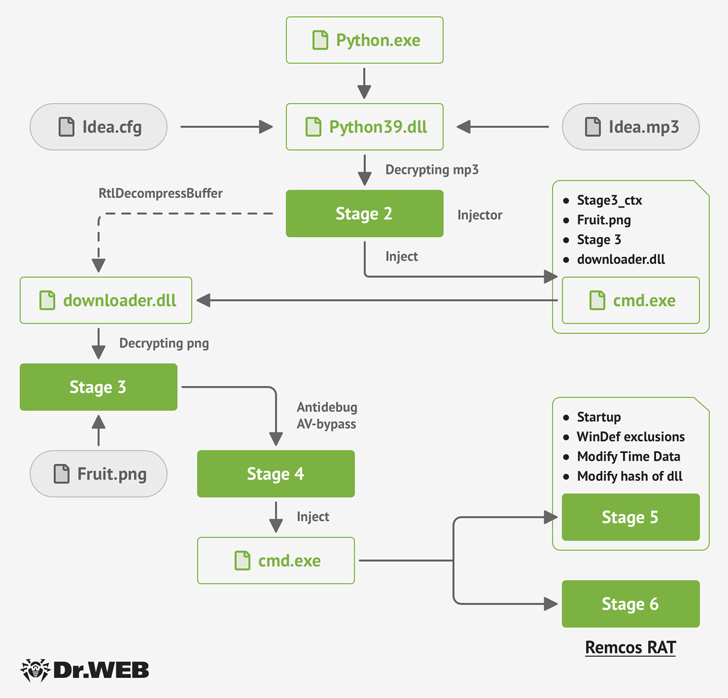
The installer, aside from activating the common installation system, stealthily drops the Fruity trojan, a Python-primarily based malware that unpacks an MP3 file (“Plan.mp3”) to load an image file (“Fruit.png”) to activate the multi-phase an infection.
“This impression file takes advantage of the steganography method to disguise two executables (.dll libraries) and the shellcode for the subsequent-phase initialization within it,” Health care provider Web reported.
Fruity is also created to bypass antivirus detection on the compromised host and ultimately start the Remcos RAT payload using a strategy named system doppelgänging.
That stated, the attack sequence could be exploited to distribute all forms of malware, which helps make it very important that buyers stick to downloading software program only from dependable sources.
The enhancement arrives as Bitdfender disclosed particulars of a malspam campaign delivering the Agent Tesla malware to harvest sensitive information from compromised endpoints.
It also follows a surge in malvertising functions that have specific consumers and organizations with tainted software boosted by means of adverts on search engines.
Forthcoming WEBINARShield Against Insider Threats: Learn SaaS Security Posture Administration
Concerned about insider threats? We have acquired you protected! Be a part of this webinar to explore practical techniques and the tricks of proactive security with SaaS Security Posture Administration.
Sign up for Right now
This features a new wave of attacks dubbed Nitrogen in which fraudulent ISO archives are dispersed employing bogus ads that impersonate obtain pages for applications these as AnyDesk, WinSCP, Cisco AnyConnect, Slack, and TreeSize.
“This malvertising campaign sales opportunities to the propagation of the infection following first exposure,” Bitdefender scientists Victor Vrabie and Alexandru Maximciuc stated.
“For as long as they dwell in the victim’s network, the attackers’ most important purpose is to get hold of qualifications, set up persistence on vital methods and exfiltrate knowledge, with extortion as the conclude target.”
Observed this posting attention-grabbing? Abide by us on Twitter and LinkedIn to examine a lot more special content we publish.
Some parts of this post are sourced from:
thehackernews.com


 Multiple Flaws Found in Ninja Forms Plugin Leave 800,000 Sites Vulnerable
Multiple Flaws Found in Ninja Forms Plugin Leave 800,000 Sites Vulnerable