Shutterstock
AWS customers have been specific in a malvertising marketing campaign which sought to steal user cloud credentials, prompting warnings from security gurus.
Exploration from security firm SentinelOne uncovered faux AWS adverts distributed on Google to dupe unknowing people into disclosing login qualifications.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The destructive advertisements had been rated second at the rear of the formal AWS website, researchers uncovered, and directed customers to a phishing internet site which mimicked the official page.
In an try to evade Google’s advertisement-fraud detection applications, threat actors have been also identified to have tailored their campaign by introducing extra redirects to further deceive customers.
“The ad by itself goes to a hop area, which is an actor-controlled blogger web-site,” reported Tom Hegel, senior risk researcher at SentinelOne. “This initial hop then redirects to the precise credentials phishing page hosted on a second domain.
“After the victim submits their qualifications, a last redirect sends the target to the reputable AWS login website page,” he additional. “The redirect represents an exertion to evade detection by careful users, but much more importantly to evade automated detection of the phishing internet websites and destructive advertisement displays.”
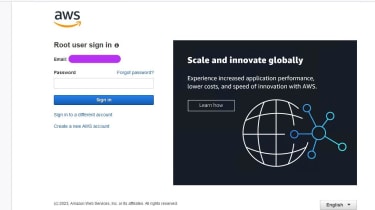
A faux AWS login website page
SentinelOne
Hegel pointed out that the different hops and written content bundled in the webpages of every domain additional to the complexity of automatic detection in attacks this kind of as these.
SentinelOne claimed it claimed the malvertising campaign to Cloudflare, which hosted the phishing web pages. The organization subsequently shut down accounts belonging to the menace actors.
Recurring threats
SentinelOne believes that this malvertising campaign can be attributed to an attacker responsible for former makes an attempt to trick AWS consumers.
Permiso’s P0 Labs done a current overview of AWS phishing web sites, and scientists observed a variety of notable similarities.
“Several properties unique to the phishing web pages are noteworthy, including the layout, structure, and efforts to hinder assessment as properly as the developers’ spoken language,” Hegel reported.
The phishing internet websites utilized in this marketing campaign integrated a unique JavaScript function to stop suitable clicks, middle mouse buttons, and keyboard shortcuts, SentinelOne discovered.
The function of this code is “likely to protect against consumers from copying content from the webpage,” researchers said.
Malvertising on the rise
This incident marks the latest in a expanding quantity of malvertising strategies as attackers search for new methods to concentrate on end users.
Last month, Bitwarden prospects elevated considerations that malicious Google adverts were being getting employed to direct buyers to malware-ridden web pages.
Just times prior, end users of streaming system OBS were being targeted in a campaign which observed a cryptocurrency influencer reduce access to their NFT wallet and Substack account.
This prompted criticism of Google’s recent system with regard to tackling malicious ads circulating in its research engine.
Security researcher Will Dormann questioned why VirusTotal, a Google-owned risk assessment tool, has not been leveraged by the tech large to automatically vet sponsored back links for malware.
IT Pro has approached Google for remark on its advert fraud detection procedures.
Investigation from the HP Wolf Security Danger Investigate division has noticed a marked increase in this attack process in new months, and issued a warning to people over the surge in attacks.
“In the last two months, we’ve viewed a considerable improve in malware dispersed by malvertising, with several risk actors at present applying this strategy,” scientists claimed in a January blog site article.
SentinelOne said the proliferation of malicious Google ads now signifies a “serious risk not just to common people, but network and cloud administrators”.
“The relieve with which these attacks can be launched, mixed with the substantial and varied viewers that Google advertisements can access, helps make them a notably strong risk,” the agency said.
Some elements of this short article are sourced from:
www.itpro.co.uk


 North Korean Hackers Targeting Healthcare with Ransomware to Fund its Operations
North Korean Hackers Targeting Healthcare with Ransomware to Fund its Operations