Cybersecurity scientists have uncovered a privilege escalation vulnerability in Google Cloud that could enable malicious actors tamper with application illustrations or photos and infect people, major to offer chain attacks.
The issue, dubbed Poor.Develop, is rooted in the Google Cloud Make services, according to cloud security firm Orca, which learned and reported the issue.
“By abusing the flaw and enabling an impersonation of the default Cloud Develop service, attackers can manipulate visuals in the Google Artifact Registry and inject malicious code,” the business mentioned in a statement shared with The Hacker Information.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Any programs constructed from the manipulated photographs are then impacted and, if the malformed applications are meant to be deployed on customer’s environments, the risk crosses from the giving organization’s surroundings to their customers’ environments, constituting a main supply chain risk.”
Adhering to liable disclosure, Google has issued a partial deal with that will not do away with the privilege escalation vector, describing it as a small-severity issue. No further more client motion is essential.
The style flaw stems from the actuality that Cloud Create quickly produces a default support account to execute builds for a undertaking on users’ behalf. Exclusively, the support account will come with too much permissions (“logging.privateLogEntries.checklist”), which will allow accessibility to audit logs made up of the total listing of all permissions on the job.
“What makes this facts so lucrative is that it tremendously facilitates lateral movement and privilege escalation in the atmosphere,” Orca researcher Roi Nisimi mentioned. “Understanding which GCP account can carry out which motion, is equal to solving a fantastic piece of the puzzle on how to launch an attack.”
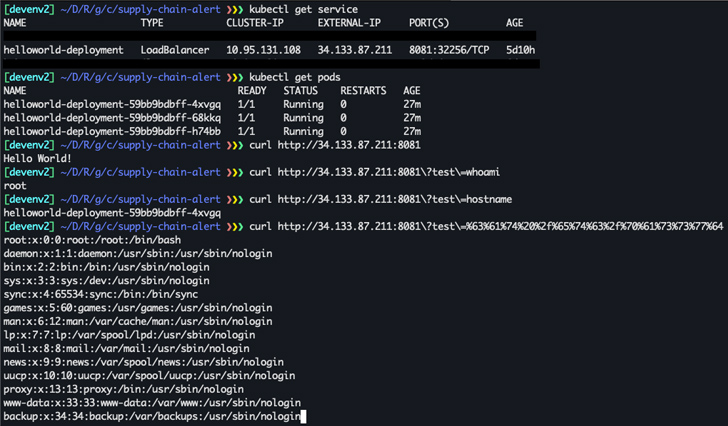
In carrying out so, a malicious actor could abuse the “cloudbuild.builds.produce” authorization by now attained by other means to impersonate the Google Cloud Develop services account and obtain elevated privileges, exfiltrate an graphic that is currently being made use of inside of Google Kubernetes Motor (GKE), and change it to include malware.
“At the time the destructive image is deployed, the attacker can exploit it and run code on the docker container as root,” Nisimi explained.
Future WEBINARShield Versus Insider Threats: Grasp SaaS Security Posture Management
Apprehensive about insider threats? We have acquired you lined! Join this webinar to discover realistic techniques and the techniques of proactive security with SaaS Security Posture Administration.
Join Today
The patch put in position by Google revokes the logging.privateLogEntries.checklist permission from the Cloud Develop service account, thereby blocking access to enumerate private logs by default.
This is not the 1st time privilege escalation flaws impacting the Google Cloud Platform have been claimed. In 2020, Gitlab, Rhino Security Labs, and Praetorian specific various methods that could be exploited to compromise cloud environments.
Prospects are suggested to monitor the behavior of the default Google Cloud Construct provider account to detect any doable destructive behavior as properly as apply the principle of minimum privilege (PoLP) to mitigate possible hazards.
Located this posting appealing? Observe us on Twitter and LinkedIn to examine extra exceptional articles we post.
Some parts of this article are sourced from:
thehackernews.com

 U.S. Government Blacklists Cytrox and Intellexa Spyware Vendors for Cyber Espionage
U.S. Government Blacklists Cytrox and Intellexa Spyware Vendors for Cyber Espionage