On April 5, 2023, the FBI and Dutch National Law enforcement announced the takedown of Genesis Market, a person of the largest dark web marketplaces. The procedure, dubbed “Operation Cookie Monster,” resulted in the arrest of 119 folks and the seizure of more than $1M in cryptocurrency. You can read the FBI’s warrant in this article for facts distinct to this situation. In light of these situations, I would like to explore how OSINT can aid with dark web investigations.
The Dark Web’s anonymity draws in a wide variety of consumers, from whistleblowers and political activists to cybercriminals and terrorists. There are several procedures that can be made use of to try and determine the individuals at the rear of these websites and personas.
Specialized Vulnerabilities
When not thought of OSINT, there have been situations when complex vulnerabilities have existed in the technology utilised to host dark websites. These vulnerabilities might exist in the application itself or be due to misconfigurations, but they can sometimes reveal the site’s correct IP tackle. Usually these software program vulnerabilities involve pen-tests applications and tactics these types of as Burp Suite to induce mistake messages containing the site’s correct IP deal with. Vulnerabilities these as these are unusual and rarely used.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
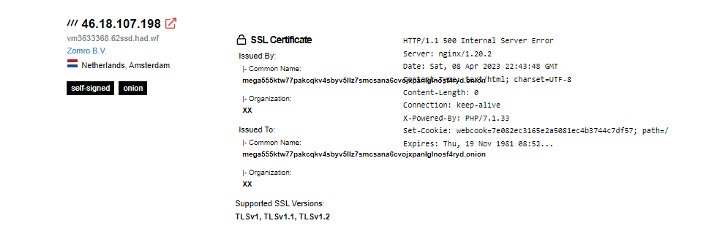
There have also been situations when dark site operators have employed SSL certs or SSH keys, which can be tied to their true IP address making use of services like Shodan or Censys.
Cryptocurrency Tracing
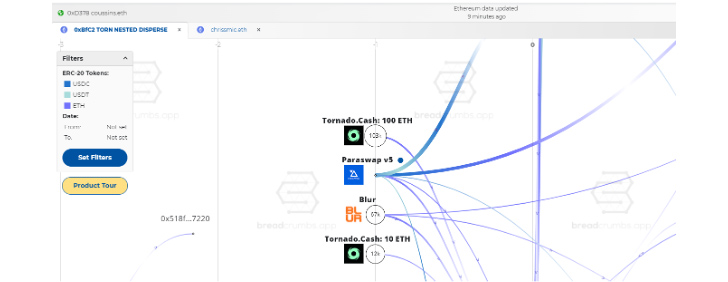
Transactions on the dark web frequently contain cryptocurrency in trade for illegal goods and expert services. This opens up the chance of identifying individuals with the aid of blockchain analysis instruments.
I are not able to go to a bank and open an account employing the name “anonymous” thanks to regulations made to avoid cash laundering. These needs are usually referred to as Anti-Dollars Laundering (AML) and Know Your Client (KYC) and have to have consumers present federal government-issued identification for proof of id. Many nations around the world have equivalent needs on cryptocurrency exchanges.
For a number of a long time, companies have presented blockchain evaluation applications that try to tie cryptocurrency addresses to specific exchanges, these as Coinbase or Binance. The moment a cryptocurrency address is tied to a unique exchange, regulation enforcement and/or economical investigators with legal authority can request that the trade give them with figuring out details for the proprietor of that account.
Traditionally, these blockchain evaluation products and services have been price tag-prohibitive for individuals to acquire, nevertheless, the blockchain analytics company Breadcrumbs a short while ago introduced an analytics system that provides substantially much more reasonably priced selling prices and a free plan.
Bringing Them Down to the Internet
We really don’t talk about the dark web until day five of my SANS SEC497 Useful OSINT study course, Why? It really is vital you very first understand about the options out there at the time a make contact with technique obtained on the dark web is introduced back again to the internet. Let me make clear.
Picture you run a food truck continuously forced to transform places thanks to a metropolis ordinance that you can under no circumstances be in the same place far more than two times a month. How would you try to make model loyalty and enable potential clients know in which you have been located each day?
You would probably try to get prospects to connect with you on social media or check out your web-site, and so on., so they can know exactly where to obtain you. Believe it or not, there is a quite equivalent dynamic on the dark web.
What the dark web gives in anonymity, and what it lacks is steadiness and security. Key marketplaces these kinds of as Silk Road, AlphaBay, Hansa, Wall Avenue, and now Genesis have all been taken down by law enforcement. Denial of Assistance attacks have grow to be a key problem on the Tor network, as evidenced by the well-known “Dread” discussion board a short while ago remaining down for quite a few months thanks to this kind of attacks. Can you picture hoping to run a small business and attain a secure money in that environment?
A single way that sellers try to reach balance and resiliency is to offer on many marketplaces and to provide strategies to contact them specifically. This try to deliver balance would make a lot of perception and is exceptionally useful for OSINT practitioners mainly because it presents get in touch with approaches, or “selectors,” which we can use to discover them on the internet and carry all our awareness, expertise, and methods to bear. Seem at the instance under in which we had been able to consider an email tackle from a dark web page and tie it to a website on the internet employing Google.
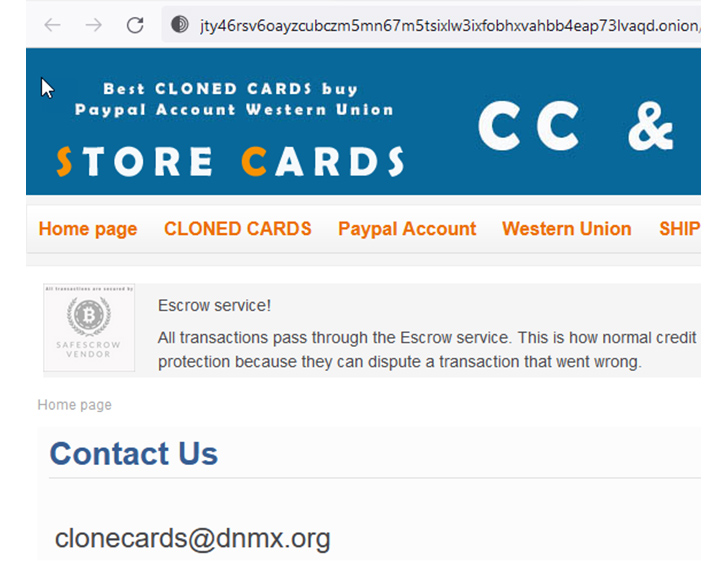
Once we tie the specific(s) to resources on the internet, we have several alternatives to deanonymize them. Some of my favored selections consist of:
Historic WHOIS Lookups
Domain registration data these kinds of as WHOIS documents can give helpful facts about the operator or operator of a site. In some situations, criminals might inadvertently expose their id or spot applying inaccurate or incomplete privacy security actions. Even if the WHOIS data for a internet site is at the moment anonymous, oftentimes, there was a issue in the past when it was not. I have found gaps as compact as 4 times in which a internet site privately registered right before and following gave away its owner’s true id.
OSINT on Boards
People on the dark web usually participate in community forums to connect, answer questions, and many others. They could inadvertently reveal information and facts that can enable OSINT practitioners study more about their true identities. The language they use and their exceptional sayings can be incredibly practical.
Breach Info
Even if an email is tied to an nameless support, the consumer may possibly have made use of it on other web sites, like boards and social media. If you are lawfully and morally able to use breach details in your investigations, you may possibly be capable to tie an on-line persona to a real title, bodily address, etc.
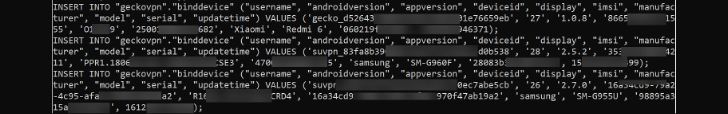
An example of a leak that has confirmed handy for some investigators was the 2021/2022 leak of 10GB of data from numerous VPN providers, including SuperVPN, GeckoVPN, and ChatVPN. This information contained whole names, billing particulars, and potentially distinctive identifiers about the units made use of, together with the global mobile subscriber identity (IMSI) of cellular products.
Future Developments and Trends
Foreseeable future dark web industry takedowns will use procedures talked about listed here and will no question include emerging technologies. The most evident development is making use of Artificial Intelligence (AI) and Device Studying (ML) in OSINT. For illustration, AI can aid construct web scraping resources that can promptly gather and examine info from various sources, even though ML algorithms can be properly trained to determine styles and relationships in the knowledge. These enhancements have the possible to help you save investigators major time and assets, allowing for them to concentrate on other elements of their investigations.
To learn additional about The SANS Institute, cybersecurity training, certifications, and Totally free methods, click here now!
Take note: This short article was expertly published and contributed by Matt Edmondson, SANS Principal Teacher.
Located this short article interesting? Follow us on Twitter and LinkedIn to read through far more exceptional information we publish.
Some sections of this posting are sourced from:
thehackernews.com


 Bad.Build Flaw in Google Cloud Build Raises Concerns of Privilege Escalation
Bad.Build Flaw in Google Cloud Build Raises Concerns of Privilege Escalation