Danger actors are now using gain of GitHub’s look for functionality to trick unsuspecting consumers searching for preferred repositories into downloading spurious counterparts that serve malware.
The most up-to-date assault on the open up-resource software offer chain entails concealing malicious code inside Microsoft Visual Code venture information which is built to download subsequent-stage payloads from a distant URL, Checkmarx reported in a report shared with The Hacker News.
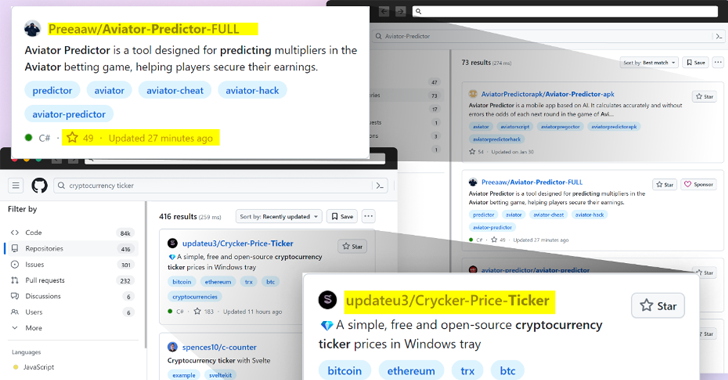
“Attackers build destructive repositories with well-known names and topics, utilizing procedures like automated updates and phony stars to boost look for rankings and deceive end users,” security researcher Yehuda Gelb claimed.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The notion is to manipulate the lookup rankings in GitHub to bring danger actor-controlled repositories to the major when buyers filter and form their effects based on the most modern updates and raise the level of popularity by way of bogus stars additional through phony accounts.

In doing so, the attack lends a veneer of legitimacy and believe in to the fraudulent repositories, efficiently deceiving developers into downloading them.
“In distinction to earlier incidents in which attackers have been identified to incorporate hundreds or thousands of stars to their repos, it seems that in these scenarios, the attackers opted for a more modest number of stars, almost certainly to stay clear of raising suspicion with an exaggerated number,” Gelb said.
It truly is really worth pointing out that prior investigate from Checkmarx has uncovered a black market comprising on-line shops and chat groups that are marketing GitHub stars to artificially increase a repository’s acceptance, a approach referred to as star inflation.
What’s much more, a majority of these repositories are disguised as authentic initiatives relevant to well known online games, cheats, and equipment, introducing yet another layer of sophistication to make it more difficult to distinguish them from benign code.
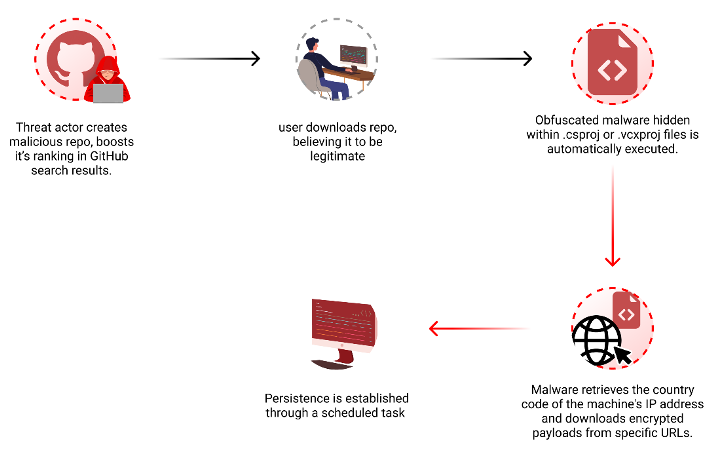
Some repositories have been observed downloading an encrypted .7z file containing an executable named “feedbackAPI.exe” that has been inflated to 750 MB in a probably attempt to evade antivirus scanning and in the end start malware that shares similarities with Keyzetsu clipper.
The Windows malware, which arrived to gentle early previous 12 months, is usually distributed by way of pirated program this kind of as Evernote. It really is able of diverting cryptocurrency transactions to attacker-owned wallets by substituting the wallet handle copied in the clipboard.
The conclusions underscore the owing diligence that builders have to follow when downloading supply code from open-source repositories, not to point out the hazards of only relying on popularity as a metric to assess trustworthiness.
“The use of destructive GitHub repositories to distribute malware is an ongoing development that poses a sizeable menace to the open up-supply ecosystem,” Gelb mentioned.

“By exploiting GitHub’s research features and manipulating repository attributes, attackers can lure unsuspecting consumers into downloading and executing malicious code.”
The development arrives as Phylum mentioned it identified an uptick in the variety of spam (i.e., non-malicious) offers currently being published to the npm registry by a person named ylmin to orchestrate a “enormous automated crypto farming marketing campaign” that abuses the Tea protocol.
“The Tea protocol is a web3 system whose mentioned purpose is compensating open resource package deal maintainers, but rather of money rewards, they are rewarded with TEA tokens, a cryptocurrency,” the firm’s exploration group reported.
“The Tea protocol is not even are living however. These people are farming details from the ‘Incentivized Testnet,’ seemingly with the expectation that owning far more factors in the Testnet will raise their odds of getting a later airdrop.”
Located this report exciting? Follow us on Twitter and LinkedIn to read a lot more exceptional content we write-up.
Some pieces of this write-up are sourced from:
thehackernews.com

 Hands-on Review: Cynomi AI-powered vCISO Platform
Hands-on Review: Cynomi AI-powered vCISO Platform