The will need for vCISO expert services is increasing. SMBs and SMEs are working with far more third-party challenges, tightening regulatory calls for and stringent cyber insurance coverage specifications than ever prior to. Having said that, they usually deficiency the assets and expertise to seek the services of an in-house security govt workforce. By outsourcing security and compliance leadership to a vCISO, these companies can far more easily get hold of cybersecurity know-how specialised for their industry and reinforce their cybersecurity posture.
MSPs and MSSPs hunting to meet this escalating vCISO demand are typically faced with the very same challenge. The demand for cybersecurity expertise significantly exceeds the source. This has led to a aggressive market place in which the charges of selecting and retaining qualified specialists can be prohibitive for MSSPs/MSPs as perfectly. The need to keep expertise of each security and compliance more exacerbates this obstacle.
Cynomi, the initial AI-driven vCISO platform, can help.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Cynomi enables you – MSPs, MSSPs and consulting corporations – to deliver vCISO solutions at scale – with out straining your existing assets. Cynomi is modeled following the information of the world’s best CISOs, enabling you and your clientele to achieve access to qualified-degree security and compliance insights and instruments.
Cynomi provides the two principal vCISO pillars, security and compliance, in an automatic and actionable method. This includes security assessments, hole examination, compliance readiness, coverage generation, endeavor management and reporting. With Cynomi, you will profit from increased income, a escalating consumer foundation, reduction in risk evaluation time, a reduce in report generation time, perfectly-structured processed and shorter worker onboarding times.
Let us see how uncomplicated Cynomi is to operate on:
Location Up and Handling Multi-Tenant Accounts
Concentrating on partners, Cynomi was designed to assistance multi-tenancy. You can independently build and control a independent sub-account for each individual of your purchasers, permitting you to very easily deal with and observe each individual 1, as very well as offering them access to Cynomi.
 Determine 1: Cynomi account administration display screen
Determine 1: Cynomi account administration display screen
To assistance your scalability and development, you can delegate roles and ownership amongst your workforce for each and every customer account. You will nonetheless appreciate admin-amount cross-account visibility and privileges.
For centralized management of all your clients, Cynomi offers a unified account administration display wherever you can edit person facts, resend invitations, unlock blocked accounts and a lot more.
Where ever you are on the platform, you happen to be generally just a click away from the admin panel and all your user accounts.
Constructing a Cyber Profile with an Onboarding Questionnaire
Onboarding a new customer begins with accumulating superior-degree facts about them, enabling to construct a applicable remediation plan. This contains an onboarding questionnaire about their infrastructure. At the time done, Cynomi generates a personalized established of quick follow-up questionnaires for security posture evaluation.
 Determine 2: Cynomi onboarding questionnaire
Determine 2: Cynomi onboarding questionnaire
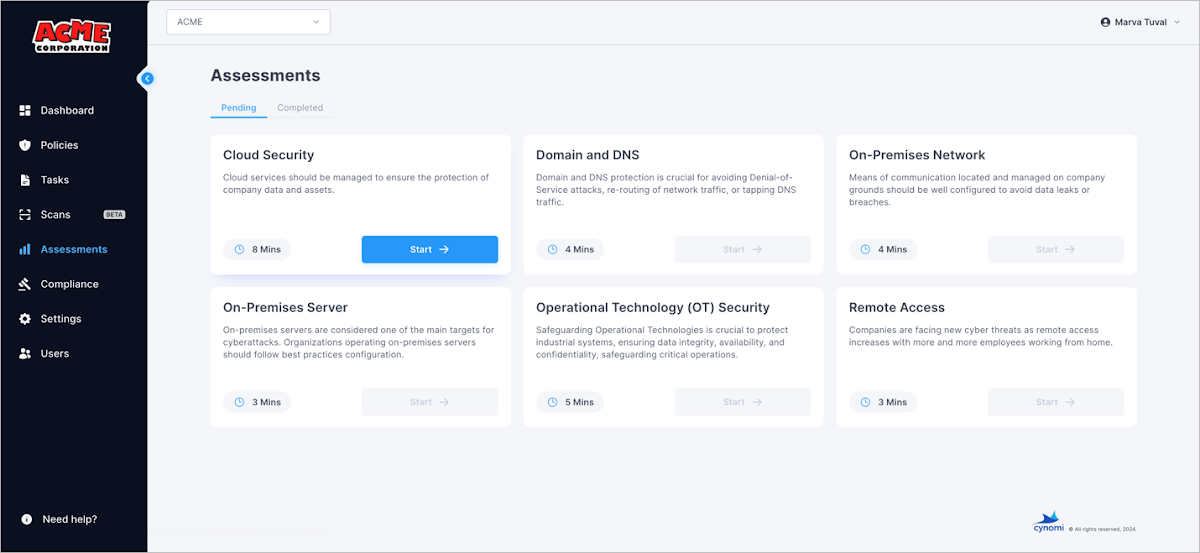 Figure 3: Cynomi customized-built adhere to-up questionnaires
Figure 3: Cynomi customized-built adhere to-up questionnaires
Completing all the questionnaires delivers a complete watch of customer security posture and gaps. Based mostly on the responses, Cynomi presents customized customized guidelines that address all actions required for remediating security gaps.
Questionnaires can be revised at any time if a client’s setting alterations. Guidelines will be immediately updated appropriately.
Inner and Exterior Scans
To increase and finish your being familiar with of your client’s cyber profiles, Cynomi enables you to scan and evaluate their exterior and internal belongings.
Exterior Scanning:
For assessing the security of externally uncovered assets, Cynomi scans IPs and URLs and discovers vulnerabilities as properly as secured configurations. This contains scanning risky ports, examining protocols and encryption, verifying email configuration parameters, technology updates of web purposes and much more.
 Determine 4: Cynomi scan success screen
Determine 4: Cynomi scan success screen
Customers can drill down into each scan obtaining to see an in-depth description and remediation possibilities. Any detected vulnerabilities are instantly extra to the account’s task record, in accordance to their severity.
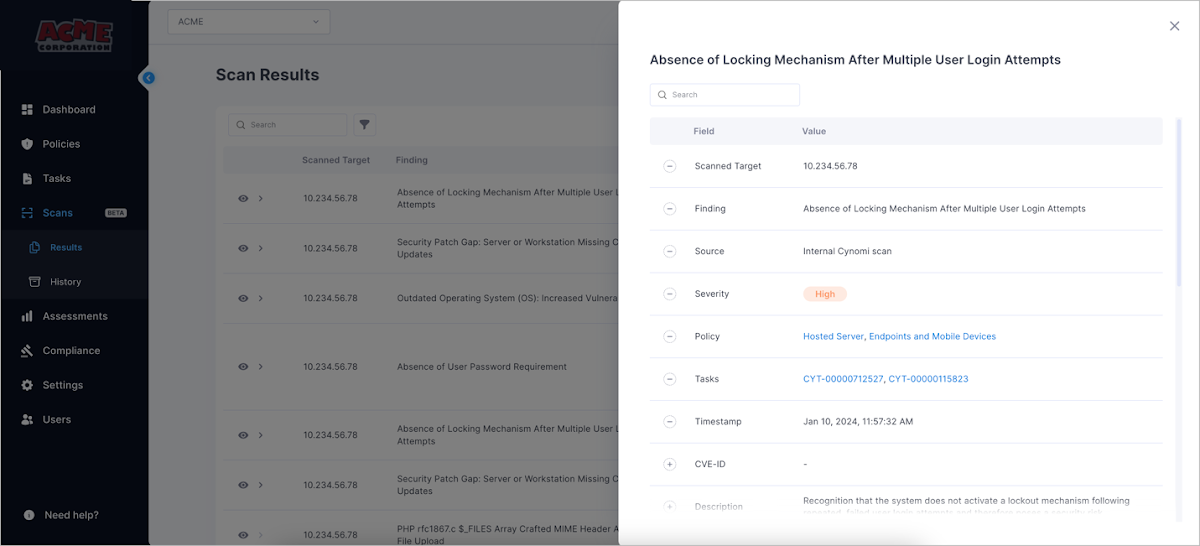 Figure 5: Drill-down to a specific obtaining
Figure 5: Drill-down to a specific obtaining
Scan effects are accessible in just a number of minutes.
Internal Scanning:
For getting vulnerabilities in the client’s internal networks. Scans deal with client assets like energetic listing and endpoints and evaluate its security cleanliness and configuration.
You can also add your NESSUS external scan, Qualys external scan or Microsoft Secure Score CSV data files.
Scan conclusions are aggregated in an aggregated table and joined to the related responsibilities and policies they are associated to.
Security Assessment
Cynomi repeatedly parses each and every client’s cyber profile against marketplace-specific security specifications, regulatory frameworks and marketplace-precise risk intelligence. These are coupled with the facts from the security questionnaires and the scans.
Based on the enterprise-precise profile, the pertinent cyber domains are dynamically picked with the optimized requirements. Each individual necessity is assigned a criticality degree, representing the worth of this necessity for the organization’s security posture. Threats these as ransomware and information leak are calculated as properly, primarily based on the organization’s sensitivity to all those attacks.
The outcome is a one pane of glass perspective of every single client’s total security posture and its progress more than time.
The dashboard contains:
- General security posture rating
- Vulnerability and exploit hole evaluation
- Risk rating for a certain danger vector
- Remediation plan with actionable prioritized tasks
- Standing towards numerous compliance frameworks necessities
 Determine 6: Cynomi principal dashboard
Determine 6: Cynomi principal dashboard
Comprehensive, Ongoing Compliance Assessment
For meeting compliance needs, Cynomi provides the shopper status versus different compliance and security frameworks (list continuously current):
- CIS v8
- ISO 27001
- NIST CSF 1.1
- NIST CSF2.
- NIST-171
- NIST-SSDF
- SOC 2
- CMMC L1, CMMC L2
- GDPR
- NIS2
- PCI-DSS
- HIPAA security
- Cyber Essentials
- FTC Safeguard Rule
- SEC compliance
- ICS Cyber Security
- CCPA
- FFIEC
The compliance module is actionable and makes it possible for observing the facts of each individual control in each and every framework and how just about every process maps into every framework.
The compliance position against frameworks is up-to-date continuously so you are constantly aware of your client’s readiness level.
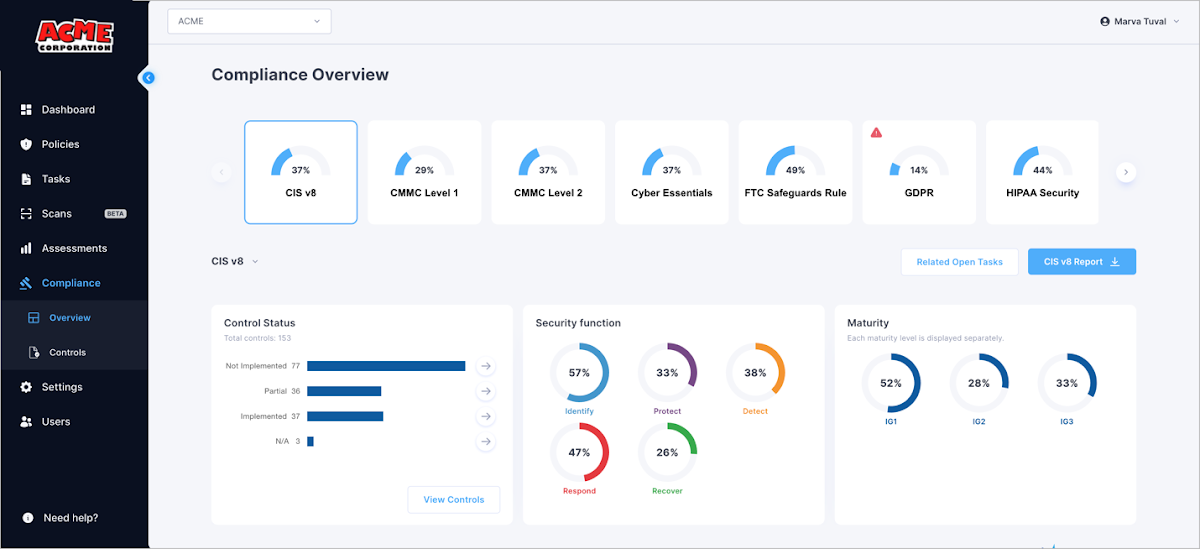 Figure 7: Cynomi compliance dashboard
Figure 7: Cynomi compliance dashboard
You can also download a dedicated compliance standing report per consumer. The report incorporates:
- Over-all compliance position
- A checklist of controls
- Maturity stage
- Manage status
- Manage mapping to framework
- Implementation status
- A backlink to the applicable Cynomi tasks
With this facts, you can easily comprehend wherever your clients stand and what gaps will need to be closed in purchase to comply with different frameworks. You can then establish a remediation plan for every single framework you chosen with just a number of clicks.
Tailor-designed Security Insurance policies
It is time to get down to business. Cynomi immediately generates a established of guidelines for just about every consumer. They are custom-produced leveraging decades of built-in CISO experience and crafted to be straightforward to stick to and actionable.
On the guidelines check out, you are going to obtain:
- The corporation score for all created policies
- The solution to drill down into the facts of every single plan, like function, scope and security requirements
- Information on the responsibilities and development that want to be completed for securing the policy’s domain
For case in point, this plan display screen displays the client’s score for each plan and will allow you to drill down to see a breakdown of the policies requirements.
 Determine 8: Cynomi insurance policies screen
Determine 8: Cynomi insurance policies screen
Guidelines are editable and customizable.
Actionable, Prioritized Remediation Tasks
Modeled following the expertise of the world’s very best CISOs, each and every coverage prerequisite is also translated into an actionable undertaking for remediation. Tasks are easy and intuitive to comprehend and adhere to and are exhibited in an AI-created prioritized record that contains its severity and status.
Task styles consist of:
- Technical controls
- Administrative methods
- Security parts configurations
- And far more
 Figure 9: Cynomi tasks monitor
Figure 9: Cynomi tasks monitor
The checklist and tasks can be edited. This overall flexibility makes it possible for the functioning vCISO to postpone or defer selected duties without affecting coverage standing or severity.
To keep track of and regulate jobs, consumers can implement filters, soar back to duties that are previously in development, or aim on significant severity tasks only. All development is tracked, and responsibilities concluded are quickly reflected in the client’s over-all security posture score.
To execute and understand jobs, every single undertaking can be drilled into for move-by-phase advice on putting a control in area or mitigating the risk. Responsibilities are also customizable, allowing for you to add greatest observe assistance, as well as proof that supports the process.
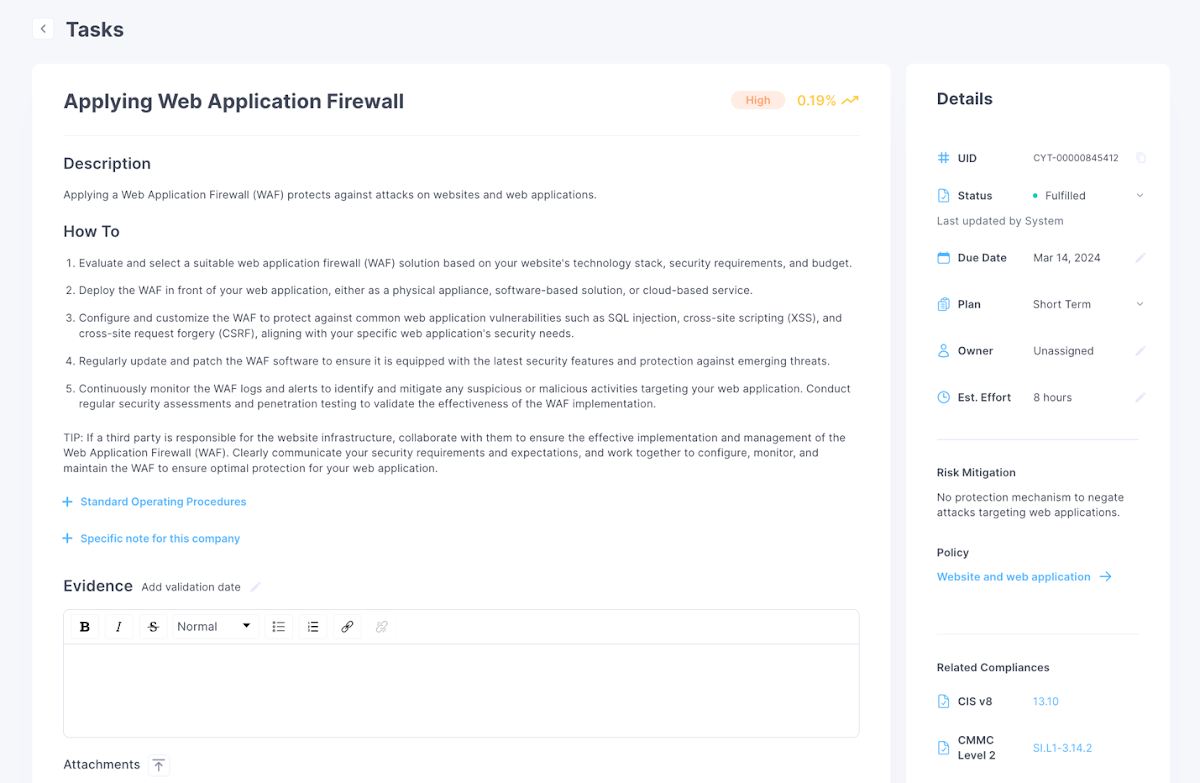 Figure 10: Drill-down to a certain task
Figure 10: Drill-down to a certain task
Plan and Roadmap
Cynomi leverages AI and automations to generate a prompt plan. Then, the Cynomi system presents the consumer with a wealth of instruments and capabilities for arranging, ongoing job administration optimization and progress tracking:
- Assigning responsibilities to short-, medium- and extended-phrase plans
- Allocating tasks to plans
- Adding due dates
- Filtering in accordance to framework, due date, position, and a lot more
- Enhancing responsibilities for each changing needs
- Incorporating information and facts and evidence to every undertaking, for each account or throughout the board, with specification, information and recommendations
- Adding item and service recommendations to jobs for upselling new products and services
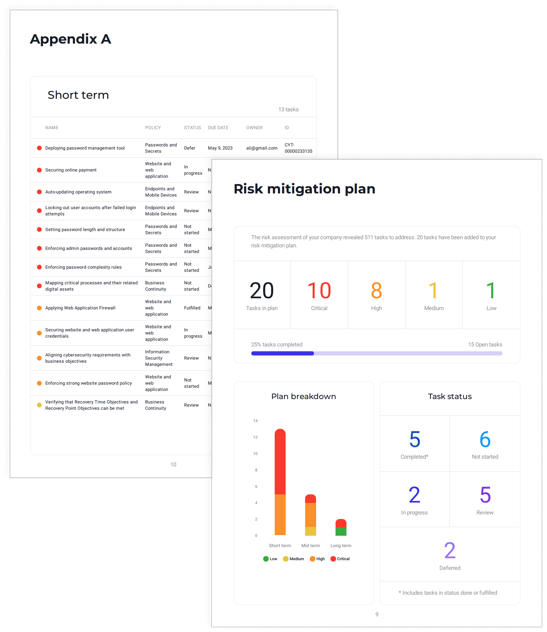 Determine 11: Cynomi automated risk mitigation plan
Determine 11: Cynomi automated risk mitigation plan
Purchaser-struggling with Reports
Cynomi includes created-in shopper-facing reporting for each and every consumer. You can create experiences at the simply click of a button with your have branding exhibiting the client’s security level, enhancement, traits, compliance gaps and comparisons with sector benchmarks. Reports involve:
- Comprehensive Report – Your client’s cybersecurity posture. Use the report to present your clients’ position to them and your suggested remediation plan. Around time, updating the report will clearly show the security enhancements you assisted them make.
- Risk Findings Report – Your clients’ risk publicity centered on the system scans.
- Compliance Report – Your clients’ compliance readiness and standing.
 Figure 12: Cynomi studies
Figure 12: Cynomi studies
These reports can aid you to conveniently present your shoppers their recent cyber posture position, the development you served them make and the influence of your work. Use these reports to open up conversations with management, IT and other stakeholders. Display them the security hazards, aid them understand demands and exhibit progress as just about every endeavor is completed.
Continual Optimization
Not like a person-time assessment resources, Cynomi constantly updates your client’s risk rating, compliance readiness insurance policies and tasks and shows development more than time. These are based mostly on modifications in your customer atmosphere, regulatory specifications and sector-precise danger intelligence. With this information and facts, you can relaxation confident that you will generally keep on top of your clients’ compliance and cybersecurity posture and display the value of your strategic cybersecurity provider to them.
The Bottom Line
Cynomi’s AI-powered vCISO platform is designed to aid MSPs and MSSPs increase their organization and income by vCISO expert services. Cynomi allows support providers provide complete vCISO providers to SMBs and SMEs, from risk assessments to security procedures to plans and reporting, throughout both equally vCISO pillars: security and compliance. By knowing the influence of every single undertaking and motion on both security and compliance, MSPs/MSSPs can make the most professional choices for their customers. This makes it possible for MSPs and MSSPs to expand their shopper base and secure recurring earnings with existing buyers.
Cynomi also minimizes vCISO tasks’ time by above 40% and can help onboard new staff members quickly, so duties can be delegated to them, irrespective of seniority. By simplifying and standardizing procedures, MSPs/MSSPs can onboard personnel and consumers immediately and slash time-to-benefit by fifty percent.
Ultimately, Cynomi’s experiences allow for MSPs and MSSPs to leverage stories and reveal tangible impact. This opens up conversations with management and boosts upsell of solutions and goods.
Pay a visit to Cynomi web-site to examination it oneself.
Discovered this report attention-grabbing? This short article is a contributed piece from one of our valued associates. Abide by us on Twitter and LinkedIn to browse much more exclusive articles we write-up.
Some components of this post are sourced from:
thehackernews.com

 Researchers Uncover First Native Spectre v2 Exploit Against Linux Kernel
Researchers Uncover First Native Spectre v2 Exploit Against Linux Kernel