Threat actors are leveraging manipulated research effects and bogus Google adverts that trick consumers who are wanting to download authentic software package such as WinSCP into installing malware as a substitute.
Cybersecurity enterprise Securonix is tracking the ongoing action less than the identify Seo#LURKER.
“The malicious advertisement directs the person to a compromised WordPress web-site gameeweb[.]com, which redirects the person to an attacker-controlled phishing web page,” security scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov stated in a report shared with The Hacker News.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The risk actors are considered to leverage Google’s Dynamic Search Adverts (DSAs), which routinely generates adverts dependent on a site’s content material to provide the destructive adverts that consider the victims to the infected web page.

The final intention of the sophisticated multi-phase attack chain is to entice users into clicking on the fake, lookalike WinSCP site, winccp[.]net, and down load the malware.
“Targeted visitors from the gaweeweb[.]com web page to the bogus winsccp[.]net web-site relies on a suitable referrer header staying established correctly,” the researchers reported. “If the referrer is incorrect, the consumer is ‘Rickrolled’ and is despatched to the notorious Rick Astley YouTube movie.”
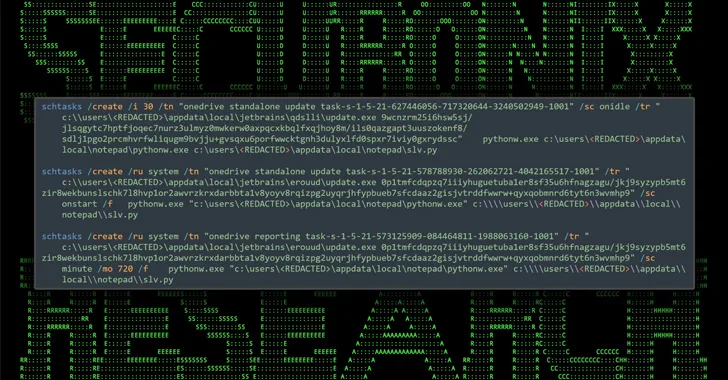
The remaining payload will take the variety of a ZIP file (“WinSCP_v.6.1.zip”) that comes with a set up executable, which, when released, employs DLL facet-loading to load and execute a DLL file named python311.dll that is present in the archive.

The DLL, for its component, downloads and executes a authentic WinSCP installer to keep up the ruse, although stealthily dropping Python scripts (“slv.py” and “wo15.py”) in the background to activate the malicious habits. It is also dependable for setting up persistence.
Each the Python scripts are developed to create make contact with with a distant actor-managed server to acquire even more guidelines that permit the attackers to operate enumeration instructions on the host.
“Specified the reality that the attackers have been leveraging Google Adverts to disperse malware, it can be considered that the targets are limited to everyone trying to get WinSCP software program,” the researchers explained.
“The geoblocking made use of on the website hosting the malware implies that people in the U.S. are victims of this attack.”

This is not the initial time Google’s Dynamic Lookup Adverts have been abused to distribute malware. Late past month, Malwarebytes lifted the lid on a marketing campaign that targets end users browsing for PyCharm with inbound links to a hacked website hosting a rogue installer that paves the way for the deployment of data-stealing malware.
Malvertising has grown in recognition among cybercriminals in the past number of years, with many malware strategies utilizing the tactic for attacks in current months.
Previously this 7 days, Malwarebytes disclosed an uptick in credit history card skimming campaigns in October 2023 that’s believed to have compromised hundreds of e-commerce internet websites with an purpose to steal money details by injecting convincing counterfeit payment web pages.
Identified this article interesting? Stick to us on Twitter and LinkedIn to study extra distinctive articles we post.
Some elements of this article are sourced from:
thehackernews.com

 FCC Enforces Stronger Rules to Protect Customers Against SIM Swapping Attacks
FCC Enforces Stronger Rules to Protect Customers Against SIM Swapping Attacks