A new details stealer malware identified as MetaStealer has set its sights on Apple macOS, earning the most current in a increasing listing of stealer households concentrated on the running program after Stealer, Pureland, Atomic Stealer, and Realst.
“Risk actors are proactively concentrating on macOS companies by posing as pretend clients in purchase to socially engineer victims into launching malicious payloads,” SentinelOne security researcher Phil Stokes mentioned in a Monday evaluation.
In these attacks, MetaStealer is dispersed in the kind of rogue software bundles in the disk graphic format (DMG), with targets approached via threat actors posing as potential design and style purchasers in order to share a password-safeguarded ZIP archive made up of the DMG file.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Other occasions have included the malware masquerading as Adobe data files or installers for Adobe Photoshop. Proof collected so significantly demonstrates that MetaStealer artifacts started appearing in the wild in March 2023. The most current sample was uploaded to VirusTotal on August 27, 2023.
“This particular concentrating on of business enterprise customers is relatively abnormal for macOS malware, which is a lot more normally found staying dispersed by way of torrent web-sites or suspicious third-party program distributors as cracked variations of business enterprise, productiveness or other preferred program,” Stokes said.
The principal component of the payload is an obfuscated Go-primarily based executable that comes with attributes to harvest info from iCloud Keychain, saved passwords, and data files from the compromised host.
Decide on variations of the malware have been observed that contains capabilities that most likely target Telegram and Meta solutions.
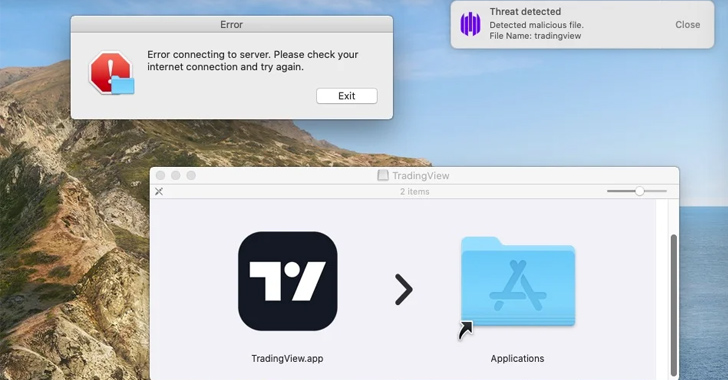
SentinelOne explained it observed some MetaStealer variants impersonating TradingView, the identical tactic that has been adopted by Atomic Stealer in new months.
Future WEBINARWay Also Susceptible: Uncovering the Condition of the Identity Attack Surface
Reached MFA? PAM? Company account protection? Obtain out how effectively-geared up your organization actually is from identity threats
Supercharge Your Expertise
This raises two prospects: Possibly the exact malware authors could be behind each the stealer family members and have been adopted by distinctive risk actors owing to discrepancies in the shipping mechanism, or they are the handiwork of disparate sets of actors.
“The visual appearance of nevertheless one more macOS infostealer this calendar year demonstrates the development toward concentrating on Mac customers for their information continues to rise in level of popularity among threat actors,” Stokes stated.
“What tends to make MetaStealer notable amid this crop of modern malware is the very clear concentrating on of company buyers and the objective of exfiltrating beneficial keychain and other info from these targets. These significant-benefit info can be made use of to go after further more cybercriminal exercise or obtain a foothold in a more substantial enterprise network.”
Located this report intriguing? Follow us on Twitter and LinkedIn to read a lot more special information we submit.
Some sections of this report are sourced from:
thehackernews.com

 Google Rushes to Patch Critical Chrome Vulnerability Exploited in the Wild – Update Now
Google Rushes to Patch Critical Chrome Vulnerability Exploited in the Wild – Update Now