A subtle phishing marketing campaign is making use of a Microsoft Word doc entice to distribute a trifecta of threats, namely Agent Tesla, OriginBotnet, and OriginBotnet, to assemble a large assortment of information and facts from compromised Windows equipment.
“A phishing email delivers the Word document as an attachment, presenting a deliberately blurred picture and a counterfeit reCAPTCHA to lure the recipient into clicking on it,” Fortinet FortiGuard Labs researcher Cara Lin stated.
Clicking on the picture prospects to the shipping of a loader from a distant server that, in convert, is designed to distribute OriginBotnet for keylogging and password restoration, RedLine Clipper for cryptocurrency theft, and Agent Tesla for harvesting sensitive info.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The loader, penned in .NET, employs a strategy termed binary padding by introducing null bytes to raise the file’s size to 400 MB in an attempt to evade detection by security application.

The activation of the loader triggers a multi-phase approach to create persistence on the host and extract a dynamic-connection library (DLL) that is responsible for unleashing the final payloads.
A person amongst them is RedLine Clipper, a .NET executable for stealing cryptocurrencies by tampering with the user’s method clipboard to substitute the place wallet tackle with an attacker-managed one.
“To have out this procedure, RedLine Clipper utilizes the ‘OnClipboardChangeEventHandler’ to regularly observe clipboard alterations and verify if the copied string conforms to the typical expression,” Lin reported.
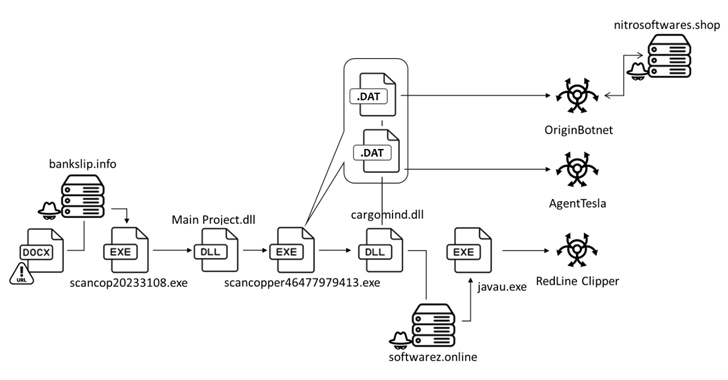
Agent Tesla, on the other hand, is a .NET-centered remote access trojan (RAT) and info stealer for getting first obtain and exfiltrating sensitive information these kinds of as keystrokes and login qualifications employed in web browsers to a command-and-management (C2) server above SMTP protocol.
Also sent is a new malware dubbed OriginBotnet, which packs in a vast range of functions to gather information, establish communications with its C2 server, and download supplementary plugins from the server to execute keylogging or password recovery features on compromised endpoints.
Impending WEBINARWay As well Susceptible: Uncovering the State of the Identity Attack Floor
Accomplished MFA? PAM? Support account security? Obtain out how well-equipped your firm definitely is in opposition to identity threats
Supercharge Your Skills
“The PasswordRecovery plugin retrieves and organizes the credentials of different browser and program accounts,” Lin claimed. “It documents these outcomes and stories them by way of HTTP Write-up requests.”
It really is really worth noting that Palo Alto Networks Unit 42, in September 2022, in depth an Agent Tesla successor named OriginLogger, which comes with very similar options as that of OriginBotnet, suggesting that they could be both equally the function of the exact menace actor.
“This cyberattack marketing campaign […] concerned a complicated chain of activities,” Fortinet said. “It began with a malicious Word document dispersed by way of phishing email messages, foremost victims to down load a loader that executed a series of malware payloads. The attack shown sophisticated approaches to evade detection and manage persistence on compromised devices.”
Found this report exciting? Observe us on Twitter and LinkedIn to go through extra distinctive material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Beware: MetaStealer Malware Targets Apple macOS in Recent Attacks
Beware: MetaStealer Malware Targets Apple macOS in Recent Attacks