The North Korea-linked threat actor recognized as Lazarus Group utilized its time-tested fabricated job lures to produce a new remote entry trojan called Kaolin RAT.
The malware could, “apart from conventional RAT functionality, transform the final generate timestamp of a selected file and load any been given DLL binary from [command-and-control] server,” Avast security researcher Luigino Camastra said in a report posted final week.
The RAT acts as a pathway to supply the FudModule rootkit, which has been not too long ago observed leveraging a now-patched admin-to-kernel exploit in the appid.sys driver (CVE-2024-21338, CVSS rating: 7.8) to obtain a kernel study/generate primitive and finally disable security mechanisms.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The Lazarus Group’s use of career offer lures to infiltrate targets is not new. Dubbed Operation Aspiration Position, the extensive-working marketing campaign has a track report of utilizing different social media and quick messaging platforms to supply malware.

These original accessibility vectors trick targets into launching a malicious optical disc graphic (ISO) file bearing three information, one particular of which masquerades as an Amazon VNC customer (“AmazonVNC.exe”) that, in fact, is a renamed edition of a legitimate Windows application identified as “choice.exe.”
The two other documents are named “version.dll” and “aws.cfg.” The executable “AmazonVNC.exe” is made use of to facet-load “model.dll,” which, in convert, spawns an IExpress.exe procedure and injects into it a payload residing within just “aws.cfg.”
The payload is intended to obtain shellcode from a command-and-management (C2) area (“henraux[.]com”), which is suspected to be an genuine-but-hacked web-site belonging to an Italian corporation that specializes in excavating and processing marble and granite.
Whilst the actual character of the shellcode is unclear, it can be reported to be employed to start RollFling, a DLL-based mostly loader that serves to retrieve and start the next-stage malware named RollSling, which was disclosed by Microsoft very last calendar year in link with a Lazarus Group marketing campaign exploiting a critical JetBrains TeamCity flaw (CVE-2023-42793, CVSS rating: 9.8).
RollSling, executed right in memory in a likely attempt to evade detection by the security software, represents the up coming stage of the infection course of action. Its major perform is to cause the execution of a third loader dubbed RollMid that is also operate in the system’s memory.
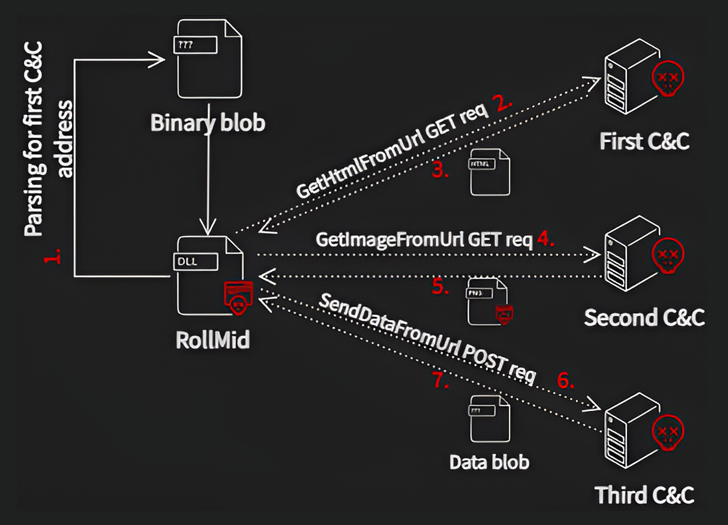
RollMid will come equipped with abilities to set the phase for the attack and set up contact with a C2 server, which involves a three-phase method of its individual as follows –
- Converse with the very first C2 server to fetch a HTML that contains the deal with of the second C2 server
- Communicate with the second C2 server to fetch a PNG impression that embeds a destructive ingredient using a approach called steganography
- Transmit data to the third C2 server using the tackle specified in the concealed facts inside of the image
- Retrieve an supplemental Foundation64-encoded information blob from the 3rd C2 server, which is the Kaolin RAT
The technological sophistication behind the multi-stage sequence, while no question complicated and intricate, borders on overkill, Avast opined, with the Kaolin RAT paving the way for the deployment of the FudModule rootkit soon after location up communications with the RAT’s C2 server.

On top rated of that, the malware is geared up to enumerate documents carry out file operations upload information to the C2 server change a file’s last modified timestamp enumerate, build, and terminate procedures execute instructions utilizing cmd.exe down load DLL documents from the C2 server and join to an arbitrary host.
“The Lazarus team specific people via fabricated work delivers and employed a advanced toolset to reach better persistence though bypassing security goods,” Camastra said.
“It is apparent that they invested substantial assets in creating these a advanced attack chain. What is particular is that Lazarus experienced to innovate constantly and allocate massive assets to study numerous areas of Windows mitigations and security goods. Their ability to adapt and evolve poses a considerable challenge to cybersecurity attempts.”
Identified this posting fascinating? Observe us on Twitter and LinkedIn to read far more distinctive content we write-up.
Some sections of this report are sourced from:
thehackernews.com


 Network Threats: A Step-by-Step Attack Demonstration
Network Threats: A Step-by-Step Attack Demonstration