A acquiring piece of ransomware referred to as Significant Head is being dispersed as component of a malvertising marketing campaign that takes the kind of bogus Microsoft Windows updates and Term installers.
Major Head was to start with documented by Fortinet FortiGuard Labs previous month, when it discovered a number of variants of the ransomware that are built to encrypt documents on victims’ equipment in exchange for a cryptocurrency payment.
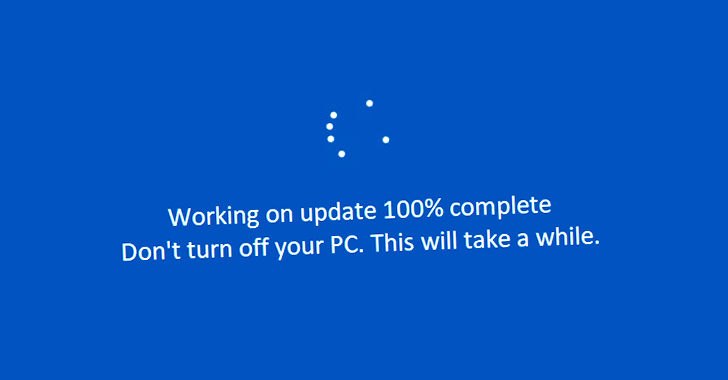
“1 Significant Head ransomware variant displays a pretend Windows Update, likely indicating that the ransomware was also distributed as a bogus Windows Update,” Fortinet researchers mentioned at the time. “A person of the variants has a Microsoft Term icon and was possible distributed as counterfeit software.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A vast majority of the Significant Head samples have been submitted so significantly from the U.S., Spain, France, and Turkey.
In a new assessment of the .NET-based ransomware, Pattern Micro specific its internal workings, calling out its means to deploy three encrypted binaries: 1.exe to propagate the malware, archive.exe to facilitate communications above Telegram, and Xarch.exe to encrypt the information and” display a bogus Windows update.
“The malware shows a faux Windows Update UI to deceive the target into thinking that the malicious exercise is a legit software program update process, with the proportion of progress in increments of 100 seconds,” the cybersecurity corporation explained.
Large Head is no distinctive from other ransomware family members in that it deletes backups, terminates various processes, and performs checks to determine if it is really operating in just a virtualized atmosphere in advance of continuing to encrypt the data files.
In addition, the malware disables the Undertaking Supervisor to prevent customers from terminating or investigating its procedure and aborts alone if the machine’s language matches that of Russian, Belarusian, Ukrainian, Kazakh, Kyrgyz, Armenian, Georgian, Tatar, and Uzbek. It also incorporates a self-delete perform to erase its presence.
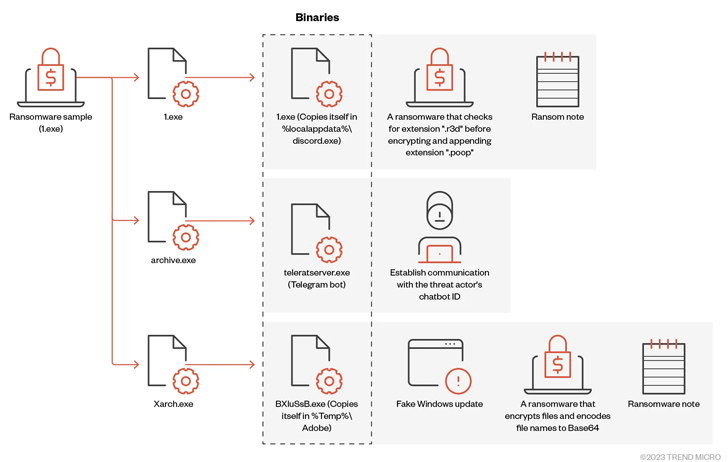
Craze Micro explained it detected a second Large Head artifact with each ransomware and stealer behaviors, the latter of which leverages the open-resource WorldWind Stealer to harvest web browser background, directory lists, functioning processes, product key, and networks.
Impending WEBINAR🔐 PAM Security – Specialist Solutions to Protected Your Delicate Accounts
This specialist-led webinar will equip you with the understanding and tactics you need to have to completely transform your privileged accessibility security strategy.
Reserve Your Spot
Also identified is a third variant of Large Head that incorporates a file infector known as Neshta, which is made use of to insert destructive code into executables on the infected host.
“Incorporating Neshta into the ransomware deployment can also provide as a camouflage technique for the closing Major Head ransomware payload,” Trend Micro researchers claimed.
“This procedure can make the piece of malware look as a distinct form of risk, this kind of as a virus, which can divert the prioritization of security solutions that mostly concentrate on detecting ransomware.”
The identification of the danger actor powering Massive Head is at the moment not recognized, but Pattern Micro reported it recognized a YouTube channel with the name “aplikasi premium cuma cuma,” suggesting an adversary probable of Indonesian origin.
“Security teams should really keep on being organized offered the malware’s various functionalities,” the scientists concluded. “This multifaceted character gives the malware the likely to result in sizeable hurt when thoroughly operational, producing it additional difficult to protect methods towards, as every single attack vector demands individual notice.”
Located this write-up attention-grabbing? Adhere to us on Twitter and LinkedIn to study extra special information we submit.
Some sections of this posting are sourced from:
thehackernews.com

 Apple Issues Urgent Patch for Zero-Day Flaw Targeting iOS, iPadOS, macOS, and Safari
Apple Issues Urgent Patch for Zero-Day Flaw Targeting iOS, iPadOS, macOS, and Safari