As the enterprise atmosphere will become significantly connected, organizations’ attack surfaces keep on to grow, generating it hard to map and protected each acknowledged and unidentified assets. In certain, unfamiliar property current security difficulties similar to shadow IT, misconfigurations, ineffective scan coverage, amid other folks.
Supplied attack surface area sprawl and evolving threats, numerous companies are embracing attack surface area administration (ASM) applications to learn and address critical exposures.
Asset discovery is an essential ability to have, and 1 that is supporting to drive the adoption of attack area administration applications and companies. That mentioned, asset discovery is only one particular part of productive attack surface area management. Building the attack surface area as impenetrable as attainable takes offensive security that goes far over and above the discovery section.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Why Asset Discovery Just isn’t Sufficient
Provided the complexity and at any time-expanding scale of the digital infrastructure at most companies, cataloging all the recognized gadgets and assets is laborious, and discovering all the unknown ones will take deep sleuthing. Building a complete inventory guarantees that all equipment and assets are topic to the same security actions and that no vulnerabilities are lurking in the shadows. It can be an important and intricate move.
On the other hand, asset discovery alone is not a alternative.
.xm_container display screen: flex align-objects: heart margin: 20px 10px 30px history: #f9fbff shade: #160755 padding: 5% border: 2px stable #d9deff border-radius: 10px textual content-align: remaining box-shadow:6px 6px #e2ebff -webkit-border-top rated-still left-radius: 25px -moz-border-radius-topleft: 25px -webkit-border-base-proper-radius: 25px -moz-border-radius-bottomright: 25px .e-book-impression flex: 200px margin-proper: 20px padding: 20px .e-book-details flex: 1 .book-particulars ul margin: 15px .ebook-particulars ul li margin-base: 5px @media (max-width: 600px) .xm_container flex-path: column .e-book-picture margin-proper: margin-bottom: 20pxpadding: 20px

Explore, prioritize, and effectively remediate vulnerabilities with info-driven Offensive Security Vision Report 2023. Get actionable insights dependent on 300,000+ findings from pentest engagements. Prioritize your protection approach.
Asset discovery helps security teams attain a detailed watch of the total attack surface, usually referred to as attack surface area mapping. What it does not do is aid security teams recognize weaknesses and vulnerabilities in the attack surface area. Most importantly, asset discovery does not aid remediation of any of individuals issues, which indicates the attack area stays at risk of being compromised by subtle risk actors.
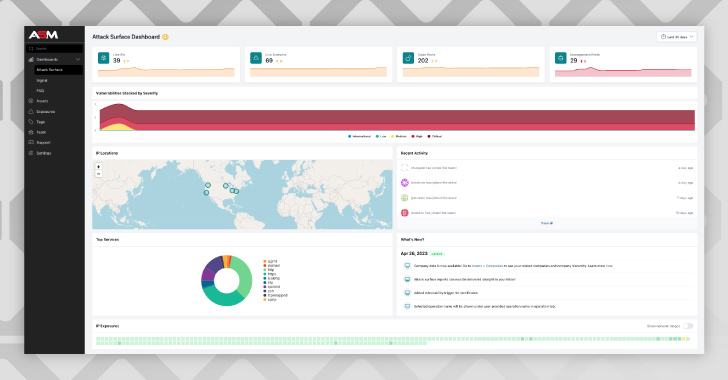 Supply: NetSPI Attack Surface area Management Platform Residence Screen
Supply: NetSPI Attack Surface area Management Platform Residence Screen
Asset discovery improves visibility. For attack surface area administration to effectively enhance an organization’s offensive security software, it need to incorporate vulnerability prioritization and remediation as well.
There are a lot of distinct approaches to vulnerability remediation, with some currently being additional productive than some others.
How to Prioritize Vulnerability Remediation
Vulnerability remediation requires various phases. The very first period requires finding each individual weakness in the attack surface – including pinpointing both identified and unidentified property and linked vulnerabilities. Up coming a vulnerability record is made and rated by severity so security teams can remediate the most urgent challenges 1st.
 Source: NetSPI 2023 Offensive Security Vision Report
Source: NetSPI 2023 Offensive Security Vision Report
Most modern attack surface area management resources choose this tactic to some extent. They call awareness to the riskiest vulnerabilities and generally define remediation methods as very well. Nevertheless, the performance of this system depends on the intelligence that informs it. And if the intelligence isn’t really innovative or backed with human assessment, this suggests vulnerabilities may perhaps get ignored or less than-prioritized. As a outcome, cyber criminals will have an less complicated path to breach the attack surface area.
What differentiates high-quality intelligence from the relaxation? Context, primarily. Vulnerability and risk are intricate determinations. And even though automation can scan high volumes of details at the moment, technology by yourself normally struggles or fails to see purple flags.
Relying on a blend of technology, a detailed methodology, and a human offensive security group with deep practical experience and cross-area experience provides the context that automated vulnerability administration instruments frequently absence. The outcome is far better insight into the most critical vulnerabilities, along with smarter strategies to remediate vulnerabilities as swiftly, effortlessly, and wholly as probable.
Automation is a very important ability, equally for asset discovery and vulnerability remediation. But the greatest results and the strongest possible attack surface area come about when pro human teams are also included.
Choose Attack Surface Administration Tools Strategically
Getting the entire positive aspects of attack floor management – these types of as more powerful however a lot more streamlined security – calls for considerate thought to pick out the correct applications and vendors.
Search initial for a resolution that goes beyond asset discovery to help and increase upon vulnerability remediation. Then prioritize companions that operate this system with a human operations group to uncover a staff with tenure.
International providers trust NetSPI’s knowledgeable workforce, technology, and extensive methodology to find and address risky exposures ahead of adversaries do. Study a lot more about NetSPI’s attack surface management abilities by connecting with the team currently.
Notice: This expertly contributed article is penned by Brianna McGovern. Brianna is NetSPI’s Merchandise Manager of ASM and retains a diploma in Industrial Engineering from Penn Condition College.
NetSPI is the world-wide chief in offensive security, providing the most thorough suite of penetration tests, attack floor management, and breach and attack simulation solutions. As a result of a mixture of technology innovation and human ingenuity NetSPI allows corporations find, prioritize, and remediate security vulnerabilities. Its international cybersecurity experts are fully commited to securing the world’s most popular corporations, like nine of the prime 10 U.S. financial institutions, 4 of the top rated 5 main international cloud suppliers, 4 of the five premier healthcare providers, three FAANG businesses, seven of the best 10 U.S. retailers & e-commerce firms, and a lot of of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
Observed this article interesting? Abide by us on Twitter and LinkedIn to read through more special material we put up.
Some elements of this posting are sourced from:
thehackernews.com


 EncroChat Bust Leads to 6,558 Criminals’ Arrests and €900 Million Seizure
EncroChat Bust Leads to 6,558 Criminals’ Arrests and €900 Million Seizure