Cybersecurity scientists have found out a new ongoing marketing campaign aimed at the npm ecosystem that leverages a one of a kind execution chain to provide an mysterious payload to qualified techniques.
“The packages in question appear to be released in pairs, each pair doing work in unison to fetch additional resources which are subsequently decoded and/or executed,” program source chain security agency Phylum reported in a report launched last week.
To that conclude, the get in which the pair of deals are mounted is paramount to pulling off a prosperous attack, as the initial of the two modules are created to store locally a token retrieved from a remote server. The campaign was 1st identified on June 11, 2023.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
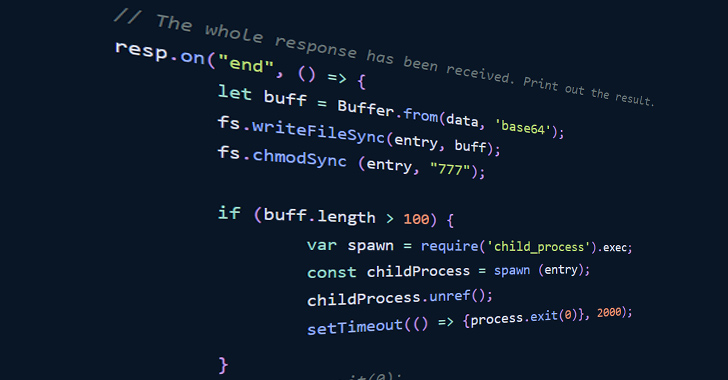
The second offer subsequently passes this token as a parameter alongside the running process form to an HTTP GET request to receive a 2nd script from the remote server. A successful execution returns a Foundation64-encoded string that is straight away executed but only if that string is lengthier than 100 people.

Phylum uncovered that the endpoint has so significantly returned the string “bm8gaGlzdG9yeSBhdmFpbGFibGU=,” which decodes to “no record readily available,” possibly implying that the attack is however a function in development or it can be engineered to return a payload only at distinct occasions.
A further speculation for this habits could be that it is really dependent on the IP address (and by extension, the location) from which the request originating from the first package is despatched when generating the token.
The identification of the danger actor guiding the operation is at the moment not known, while it has all the hallmarks of a “moderately” sophisticated source chain menace given the lengths the adversary has absent to execute the attack, whilst also using actions to dynamically produce the up coming-stage payload to evade detection.
“It really is essential that just about every deal in a pair is executed sequentially, in the right buy, and on the similar machine to guarantee thriving procedure,” Phylum observed. “This cautiously orchestrated attack serves as a stark reminder of the at any time-evolving complexity of modern day risk actors in the open up-supply ecosystem.”
The disclosure comes as Sonatype uncovered a set of 6 malicious packages on the Python Package Index (PyPI) repository – broke-rcl, brokescolors, brokescolors2, brokescolors3, brokesrcl, and trexcolors – that had been uploaded by a solitary account named broke.

“These packages goal the Windows working program and are identical with regards to their versioning,” security researcher and journalist Ax Sharma said. “Upon set up, these deals basically download and run a trojan hosted on Discord’s servers.”
Also discovered by Sonatype is a package deal referred to as libiobe that’s capable of focusing on both equally Windows and Linux functioning devices. On devices functioning Windows, the package deal provides an information stealer, whereas on Linux, it truly is configured to profile the procedure and exfiltrate that information back again to a Telegram endpoint.
“It is hard to confirm who would finally run offers with this kind of names or who they are precisely targeting,” Sharma observed. “Whilst these packages may possibly not be utilizing any novel payload or practices, or have apparent targets, they are a testament to the ongoing destructive attacks that are targeting open up resource software program registries like PyPI and npm.”
Located this article interesting? Follow us on Twitter and LinkedIn to read through much more exclusive material we publish.
Some pieces of this short article are sourced from:
thehackernews.com

 Beyond Asset Discovery: How Attack Surface Management Prioritizes Vulnerability Remediation
Beyond Asset Discovery: How Attack Surface Management Prioritizes Vulnerability Remediation