A new process injection strategy dubbed Mockingjay could be exploited by risk actors to bypass security remedies to execute destructive code on compromised programs.
“The injection is executed without the need of place allocation, location permissions or even beginning a thread,” Security Joes scientists Thiago Peixoto, Felipe Duarte, and
Ido Naor claimed in a report shared with The Hacker Information. “The uniqueness of this method is that it requires a vulnerable DLL and copying code to the correct portion.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Course of action injection is an attack system that permits adversaries to inject code into processes in get to evade system-dependent defenses and elevate privileges. In accomplishing so, it could allow for for the execution of arbitrary code in the memory house of a separate stay method.

Some of the nicely-regarded system injection methods consist of dynamic website link library (DLL) injection, moveable executable injection, thread execution hijacking, procedure hollowing, and process doppelgänging, among some others.
It really is truly worth pointing out that each of these procedures necessitates a blend of particular method phone calls and Windows APIs to carry out the injection, thereby permitting defenders to craft acceptable detection and mitigation strategies.
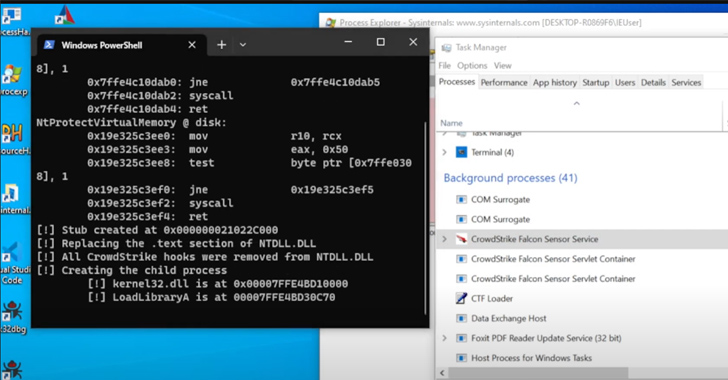
What helps make Mockingjay stands apart is that it subverts these security levels by removing the have to have to execute Windows APIs ordinarily monitored by security remedies by leveraging pre-existing Windows moveable executable information that presently arrive with a memory block shielded with Browse-Compose-Execute (RWX) permissions.
This, in change, is attained making use of msys-2..dll, which comes with a “generous 16 KB of out there RWX area,” making it an great applicant to load destructive code and fly under the radar. Even so, it truly is well worth noting that there could be other these types of susceptible DLLs with comparable qualities.
The Israeli corporation said it explored two distinctive techniques — self injection and distant process injection — to achieve code injection in a manner that not only enhances the attack efficiency, but also circumvents detection.
In the 1st method, a custom software is used to right load the susceptible DLL into its handle room and ultimately execute the desired code working with the RWX portion. Remote course of action injection, on the other hand, entails using the RWX part in the vulnerable DLL to execute process injection in a remote method these kinds of as ssh.exe.

“The uniqueness of this strategy lies in the point that there is no have to have to allocate memory, established permissions or generate a new thread inside of the focus on procedure to initiate the execution of our injected code,” the scientists reported.
“This differentiation sets this approach apart from other existing procedures and can make it hard for Endpoint Detection and Reaction (EDR) devices to detect this system.”
The findings occur months right after cybersecurity company SpecterOps thorough a new method that exploits a respectable Visual Studio deployment technology referred to as ClickOnce to attain arbitrary code execution and receive first access.
Located this article attention-grabbing? Abide by us on Twitter and LinkedIn to go through a lot more distinctive material we submit.
Some components of this write-up are sourced from:
thehackernews.com

 New Ongoing Campaign Targets npm Ecosystem with Unique Execution Chain
New Ongoing Campaign Targets npm Ecosystem with Unique Execution Chain