Why is Visibility into OT Environments Critical?
The importance of Operational Technology (OT) for companies is simple as the OT sector thrives along with the currently flourishing IT sector. OT incorporates industrial regulate units, production equipment, and products that oversee and control industrial environments and critical infrastructures. In recent decades, adversaries have recognized the lack of detection and security in quite a few industrial methods and are actively exploiting these vulnerabilities. In response, IT security leaders have turn out to be far more mindful of the require to shield their OT environments with security checking and response abilities. This development was accelerated by intense earlier cyber incidents focusing on critical OT environments and even leading to physical problems to infrastructures. Supplied the pivotal position these units participate in in company functions and contemporary society, making sure their security is of utmost importance.
The underlying trend is clear: OT and IoT networks are progressively integrated with common IT networks for administration and access purposes, main to increased communication between these equipment both internally and externally. This not only affects the networks alone but also carries significant ramifications for the security teams responsible for safeguarding the ecosystem. Although this convergence of OT and IT presents numerous added benefits, these as improved performance and reduced operational costs, it also offers rise to new security dangers and worries, rendering OT environments much more susceptible to cyber threats. As evidenced by past attacks, these threats usually go undetected due to insufficient security checking, enabling risk actors to continue being undetected for prolonged durations. As a result, attaining holistic visibility and powerful anomaly detection in OT environments is pivotal for retaining steadfast security and control.
What Issues Arise in Monitoring OT Environments?
First and foremost, being familiar with the exclusive menace landscape of OT environments is important. Traditional IT security detection approaches tumble quick in this context, as they demand unique sensitivity thresholds and a lot more refined checking for network segments or unit teams, as well as OT-certain detection mechanisms. In contrast to IT attacks that concentration on info theft, OT attacks generally goal for bodily impression. Moreover, as new examples demonstrate, ransomware in the context of OT is on the increase and instantly has an effect on the availability of regulate systems and protection.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Next, monitoring OT environments necessitates the thing to consider of several facets, such as provider access management, machine management, and network communications. Controlling and overseeing supplier access to OT and IoT networks is difficult, as connections in between exterior and internal networks can happen by means of several suggests like VPNs, immediate mobile connections, and bounce hosts. A different hurdle is unit management, which encompasses update mechanisms and defense versus unauthorized obtain or manipulation. Employing frequent updating routines and deploying Endpoint Detection & Reaction (EDR) on OT and IoT devices is often limited or infeasible. The assortment of units, their lifetime spans, and gadget-particular functioning programs make deploying security software program to monitor OT gadgets tricky and cumbersome.
3rd, traditional IT network detection procedures have to have in-depth protocol knowledge, which, in the OT context, includes a huge array of distinctive protocols and attack eventualities absent in traditional rule sets. OT network gadgets hook up IoT sensors and devices applying communication protocols unheard of in common IT networks. In conditions of much more intrusive security solutions, active vulnerability scanning solutions can also be problematic in OT environments, as they might induce disruptions or even outages. The very same applies to Intrusion Avoidance Units (IPS) for the reason that they could block network packets, impacting balance and small business continuity in OT environments. As a outcome, passive network detection techniques like Network Detection & Response (NDR) options are far better suited for this intent.
How Can I Proficiently Watch and Protected My OT Environment?
While safe access management and machine lifecycle management are vital, their seamless implementation can be exceptionally challenging. In this context, Network Detection and Reaction (NDR) solutions offer you a non-intrusive and effective solution to monitoring OT environments. By focusing on interaction designs for OT devices, the intersection among IT and OT, and third-party entry to OT networks, NDR devices present comprehensive visibility and detection capabilities without having disrupting industrial functions and enterprise procedures.
In certain, NDR remedies with highly developed baselining abilities excel at figuring out new and unconventional communication patterns that could point out malicious things to do in OT networks. Making use of movement data for baselining, these NDR devices provide protocol and product-impartial anomaly detection by understanding who communicates with whom and at what frequency. Rather of manually configuring these parameters, the NDR learns the baseline and alerts the security teams on strange requests or modifications in the frequency. In addition, a flexible use circumstance framework allows setting great-tuned thresholds for OT-specific checking, including the ability to established load monitoring with network zone-unique granularity. Also, the use of Device Finding out algorithms permits for much more correct detection of anomalies and possible threats in comparison to common rule-dependent devices.
As a consequence, the passive checking abilities of NDR remedies are important for OT and IoT environments, exactly where choice checking procedures may be difficult to put into action or bring about disruptions. ExeonTrace, a significantly strong and effortless-to-carry out ML-driven NDR program for OT environments, analyzes log facts from regular IT environments, OT networks, and bounce host gateways, to supply a detailed and holistic check out of network exercise. Therein, the overall flexibility of integrating several third-party log resources, these as OT-distinct logs, is important. Additionally, ExeonTrace’s potential to combine with other OT-particular detection platforms enhances its capabilities and guarantees extensive security protection.
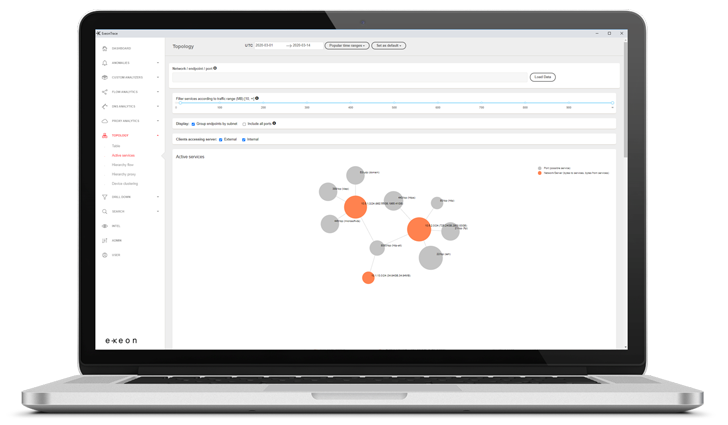 ExeonTrace Platform: OT Network Visibility
ExeonTrace Platform: OT Network Visibility
In summary, NDR alternatives like ExeonTrace successfully handle the distinctive difficulties of OT checking, developing the Swiss NDR program as the favored detection technique for safeguarding OT environments. By utilizing ML-driven NDR techniques like ExeonTrace, companies can reliably keep an eye on and secure their industrial operations, making certain business enterprise continuity by way of an automated, economical, and hardware-absolutely free method. Uncover out if ExeonTrace is the best alternative for your company and ask for a demo nowadays.
Found this write-up appealing? Stick to us on Twitter and LinkedIn to go through extra distinctive content material we write-up.
Some components of this report are sourced from:
thehackernews.com

 Fortra Sheds Light on GoAnywhere MFT Zero-Day Exploit Used in Ransomware Attacks
Fortra Sheds Light on GoAnywhere MFT Zero-Day Exploit Used in Ransomware Attacks