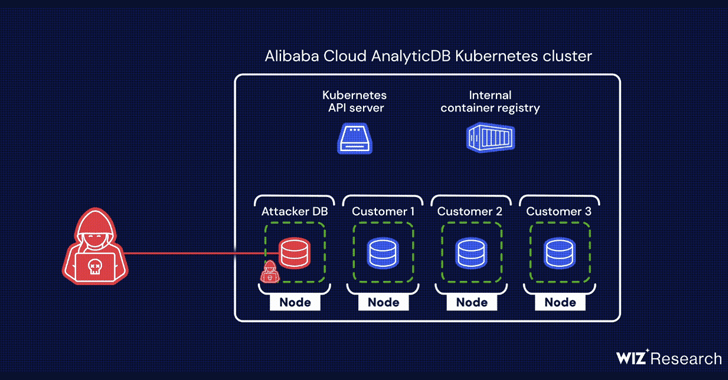
A chain of two critical flaws has been disclosed in Alibaba Cloud’s ApsaraDB RDS for PostgreSQL and AnalyticDB for PostgreSQL that could be exploited to breach tenant isolation protections and access delicate data belonging to other prospects.
“The vulnerabilities potentially allowed unauthorized accessibility to Alibaba Cloud customers’ PostgreSQL databases and the potential to execute a offer chain attack on both equally Alibaba database services, leading to an RCE on Alibaba databases expert services,” cloud security firm Wiz said in a new report shared with The Hacker Information.
The issues, dubbed BrokenSesame, were being documented to Alibaba Cloud in December 2022, subsequent mitigations ended up deployed by the firm on April 12, 2023. There is no proof to suggest that the weaknesses were exploited in the wild.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
In a nutshell, the vulnerabilities – a privilege escalation flaw in AnalyticDB and a distant code execution bug in ApsaraDB RDS – created it possible to elevate privileges to root in just the container, escape to the fundamental Kubernetes node, and eventually receive unauthorized entry to the API server.
Armed with this functionality, an attacker could retrieve qualifications related with the container registry from the API server and press a malicious picture to attain manage of shopper databases belonging to other tenants on the shared node.
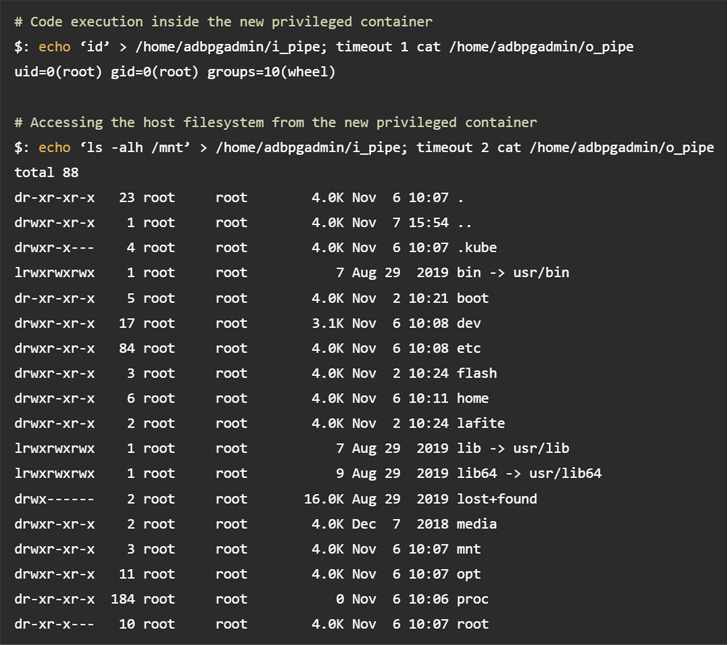
“The credentials utilised to pull photographs were being not scoped the right way and authorized push permissions, laying the foundation for a provide-chain attack,” Wiz researchers Ronen Shustin and Shir Tamari said.
This is not the initial time PostgreSQL vulnerabilities have been recognized in cloud services. Past calendar year, Wiz uncovered very similar issues in Azure Databases for PostgreSQL Flexible Server (ExtraReplica) and IBM Cloud Databases for PostgreSQL (Hell’s Keychain).
Forthcoming WEBINARDefend with Deception: Advancing Zero Belief Security
Learn how Deception can detect superior threats, prevent lateral movement, and enhance your Zero Rely on tactic. Be part of our insightful webinar!
Help you save My Seat!
The findings appear as Palo Alto Networks Device 42, in its Cloud Risk Report, uncovered that “risk actors have become adept at exploiting prevalent, daily issues in the cloud,” like misconfigurations, weak credentials, lack of authentication, unpatched vulnerabilities and destructive open supply program (OSS) packages.
“76% of companies never enforce MFA [multi-factor authentication] for console buyers, even though 58% of businesses you should not enforce MFA for root/admin users,” the cybersecurity business stated.
Observed this posting appealing? Observe us on Twitter and LinkedIn to browse far more special material we submit.
Some pieces of this posting are sourced from:
thehackernews.com

 Lazarus Group Adds Linux Malware to Arsenal in Operation Dream Job
Lazarus Group Adds Linux Malware to Arsenal in Operation Dream Job