The infamous North Korea-aligned point out-sponsored actor identified as the Lazarus Team has been attributed to a new marketing campaign aimed at Linux users.
The attacks are section of a persistent and prolonged-running exercise tracked under the name Procedure Desire Occupation, ESET mentioned in a new report released now.
The results are very important, not the very least since it marks the to start with publicly documented example of the adversary using Linux malware as section of this social engineering scheme.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Operation Dream Work, also acknowledged as DeathNote or NukeSped, refers to a number of attack waves whereby the group leverages fraudulent work features as a lure to trick unsuspecting targets into downloading malware. It also exhibits overlaps with two other Lazarus clusters recognised as Operation In(ter)ception and Operation North Star.
The attack chain identified by ESET is no unique in that it delivers a pretend HSBC occupation offer as a decoy inside a ZIP archive file that’s then utilized to start a Linux backdoor named SimplexTea distributed through an OpenDrive cloud storage account.
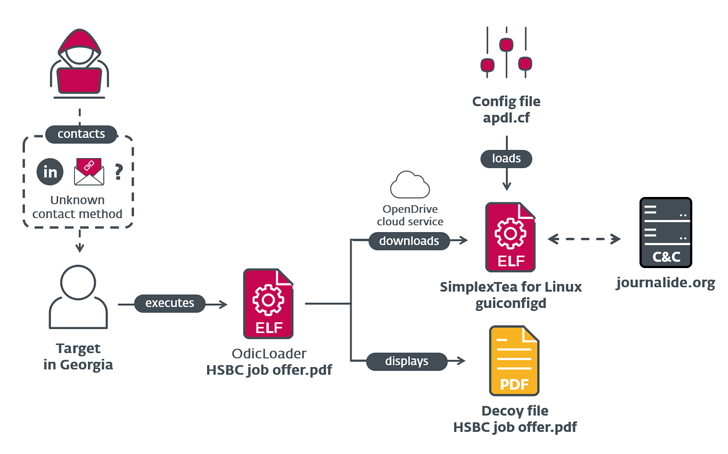
While the actual approach utilised to distribute the ZIP file is not recognised, it can be suspected to be both spear-phishing or immediate messages on LinkedIn. The backdoor, prepared in C++, bears similarities to BADCALL, a Windows trojan formerly attributed to the team.
Also, ESET stated it identified commonalities among artifacts utilised in the Aspiration Occupation campaign and those people unearthed as part of the supply chain attack on VoIP software program developer 3CX that arrived to light last thirty day period.
Forthcoming WEBINARDefend with Deception: Advancing Zero Trust Security
Uncover how Deception can detect state-of-the-art threats, cease lateral motion, and improve your Zero Rely on strategy. Join our insightful webinar!
Help you save My Seat!
This also involves the command-and-management (C2) domain “journalide[.]org,” which was detailed as 1 of the four C2 servers applied by malware family members detected in just the 3CX setting.
Indications are that preparations for the supply chain attack had been underway because December 2022, when some of the elements have been committed to the GitHub code-hosting platform.
The findings not only fortify the current hyperlink between Lazarus Group and the 3CX compromise, but also demonstrates the threat actor’s ongoing accomplishment with staging supply chain attacks since 2020.
Located this posting appealing? Comply with us on Twitter and LinkedIn to browse more exceptional content we publish.
Some elements of this post are sourced from:
thehackernews.com

 Fortra Sheds Light on GoAnywhere MFT Zero-Day Exploit Used in Ransomware Attacks
Fortra Sheds Light on GoAnywhere MFT Zero-Day Exploit Used in Ransomware Attacks