Ransomware attacks are a main issue for companies in all places, and the severity of this trouble continues to intensify.
A short while ago, Microsoft’s Incident Response workforce investigated the BlackByte 2. ransomware attacks and exposed these cyber strikes’ terrifying velocity and harmful nature.
The conclusions show that hackers can complete the entire attack procedure, from getting original entry to triggering sizeable damage, in just five times. They waste no time infiltrating techniques, encrypting critical info, and demanding a ransom to launch it.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This shortened timeline poses a considerable problem for companies making an attempt to shield themselves from these destructive operations.
BlackByte ransomware is utilized in the remaining phase of the attack, using an 8-digit amount important to encrypt the details.
To carry out these attacks, hackers use a effective mixture of instruments and strategies. The investigation uncovered that they acquire gain of unpatched Microsoft Exchange Servers—an method that has proven highly profitable. By exploiting this vulnerability, they attain preliminary entry to the concentrate on networks and set the stage for their malicious things to do.
The ransomware even more employs approach hollowing and antivirus evasion approaches to assurance profitable encryption and circumvent detection.
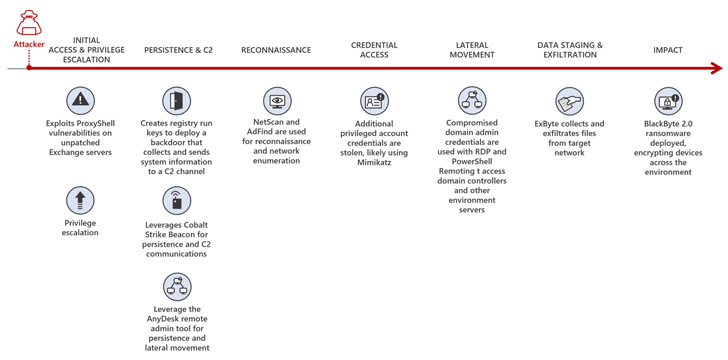
Additionally, web shells equip them with remote accessibility and regulate, enabling them to maintain a existence inside of the compromised techniques.
The report also highlighted the deployment of Cobalt Strike beacons, which aid command and regulate operations. These complex resources give attackers a vast variety of capabilities, generating it extra difficult for corporations to protect versus them.
Approaching WEBINAR🔐 Privileged Access Management: Study How to Conquer Crucial Worries
Find unique methods to conquer Privileged Account Management (PAM) challenges and stage up your privileged entry security method.
Reserve Your Place
Alongside these tactics, the investigation uncovered quite a few other troubling procedures cybercriminals use. They employ “living-off-the-land” tools to blend in with genuine processes and escape detection.
The ransomware modifies quantity shadow copies on infected machines to stop facts recovery by means of procedure restore points. The attackers also deploy specifically-crafted backdoors, ensuring continued obtain for the attackers even following the preliminary compromise.
The disturbing upsurge in ransomware attacks needs fast motion from organizations around the globe. In reaction to these conclusions, Microsoft has presented some useful suggestions.
Organizations are primarily urged to implement strong patch management procedures, making certain they well timed apply critical security updates. Enabling tamper security is one more important move, as it strengthens security methods from malicious tries to disable or bypass them.
Found this posting appealing? Abide by us on Twitter and LinkedIn to go through additional special written content we put up.
Some areas of this write-up are sourced from:
thehackernews.com


 Google Releases Android Patch Update for 3 Actively Exploited Vulnerabilities
Google Releases Android Patch Update for 3 Actively Exploited Vulnerabilities