Security groups ordinarily have terrific visibility around most places, for case in point, the corporate network, endpoints, servers, and cloud infrastructure. They use this visibility to implement the essential security and compliance specifications. Even so, this is not the case when it comes to sensitive data sitting down in production or analytic databases, info warehouses or information lakes.
Security teams have to count on data teams to locate delicate info and enforce access controls and security policies. This is a enormous headache for equally the security and knowledge teams. It weakens the business’s security and compliance putting it at risk of exposing sensitive information, significant fines, reputational damages, and more. Also, in a lot of conditions, it slows down the business’s skill to scale up information operations.
This report examines how Satori, a data security platform, presents command of the delicate data in databases, facts warehouses and facts lakes to the security teams.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Satori’s automated facts security system delivers a uncomplicated and effortless way to fulfill security and compliance specifications whilst reducing risk exposure.
Why is Securing Info Shops Challenging?
Security teams you should not have great visibility and enforcement of guidelines concerning access to DBs, facts warehouses or data lakes. Take a search at an example.
Nick is a security engineering manager at ACME business. He is liable for retaining up with altering security and compliance rules these as HIPAA, SOC2, and ISO. This is a challenging job considering the fact that security and compliance laws are always changing and evolving. Nick is excellent at his career and can wade via the complexities of the different restrictions and ascertain the vital security actions to make sure that ACME continues to be in compliance. This is vital so that ACME isn’t going to fail an audit, expose sensitive data, obtain fines or worse.
Then, a person day, Nick is abruptly tasked with meeting security and compliance necessities throughout all of ACME’s analytic and generation details.
Nick faces a trouble. Though he has performed his work and established the required methods to be certain security and compliance it is incredibly difficult to in fact have out these steps and carry out the security guidelines. There are several reasons why Nick’s job is tough and aggravating that are explored in much more detail below.
Visibility About Delicate Info and Logs
Nick’s deficiency of visibility boundaries his means to apply and manage security procedures and compliance prerequisites. 3 main sources impede his visibility.
1 — Different logs from different resources are “buried.”
Considering the fact that ACME has sensitive info distribute throughout a number of databases, knowledge lakes and data warehouses there are a large wide range of audit logs from all of these various resources. Additionally, Nick has to correlate the log knowledge with recognized spots of sensitive facts (if he has them).
2 — Improvements to the configuration and processes to empower visibility.
It is important to be certain that all delicate knowledge access is accurately monitored. Nick may perhaps want to analyze why a consumer was accessing delicate facts in a location exterior their services area and avert this form of accessibility from taking place in the future. He wants to transform the configuration and make sure that the transform handle procedures are effective. Nonetheless, this is not as simple as it appears to be. The lack of visibility suggests that Nick can’t confirm that these alterations are created in actual-time.
3 — Figuring out the type and place of sensitive info.
Nick doesn’t have the skill to continually seek out out delicate information. His lack of visibility coupled with the reality that he is not the operator of these data outlets suggests that he is not ready to lookup the multiple facts shops for delicate knowledge. In its place, he has to depend on the engineering group.
The majority of businesses use guide processes to scan and find out sensitive facts. The manual scanning of details, when Nick can get the data engineers to stop their jobs and undertake this undertaking, is sluggish and error-vulnerable. This usually means that Nick is frequently anxious about getting the information engineers to repeatedly scan the info to come across sensitive information and facts and id information.
Enforcement of Security Policies
ACME has delicate facts that is distribute throughout a range of varied databases, data lakes and data warehouses. Nick is a very great security engineer but it is not likely that he has the understanding to have an understanding of SQL and the interior workings of the databases, knowledge warehouses and lakes that comprise the ACME info stack. Since he does not have the ability to really code the needed improvements to the security policies he has to count on the facts engineers to have out his tasks.
Even even though details engineers commonly like to get the job done on their very own jobs as a substitute of employing Nick’s security insurance policies, it is not likely that they would permit Nick to employ them himself, even if he understood how. The engineers who personal the info shops probably do not want Nick to meddle with issues like developing objects or altering configurations on their info outlets. So even if he desired to, and could, it is unlikely that Nick has the obtain to use and implement the needed security insurance policies, alternatively, he demands to rely on the info engineers to do this for him.
Applying a Data Security System
An overview of making use of Satori’s automated information security platform, to conquer these types of worries follows.
Total Visibility
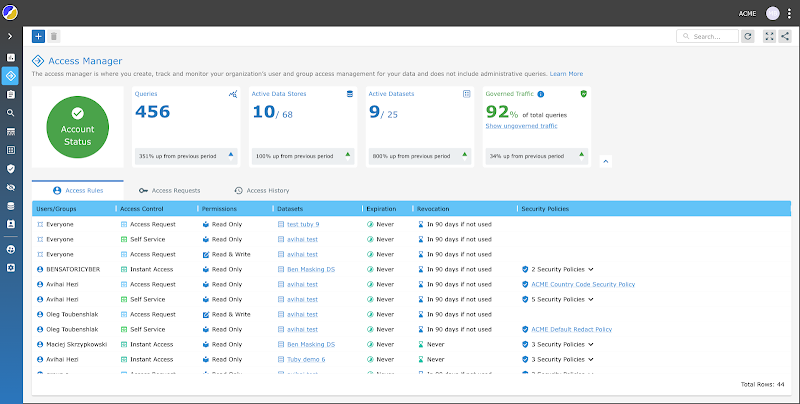
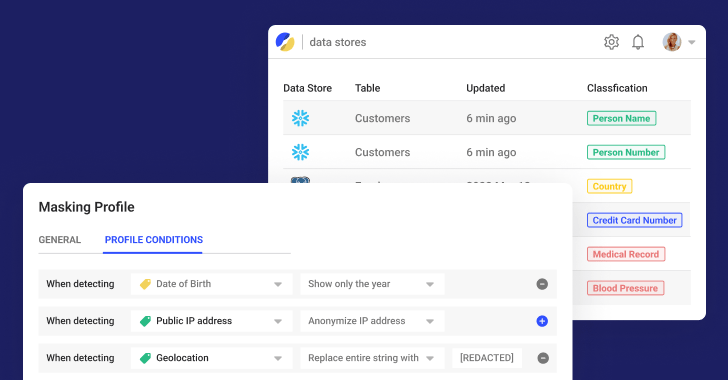
Nick can use Satori’s Access Supervisor and acquire full visibility above all of the implemented security policies and audit logs from analytics and manufacturing info.
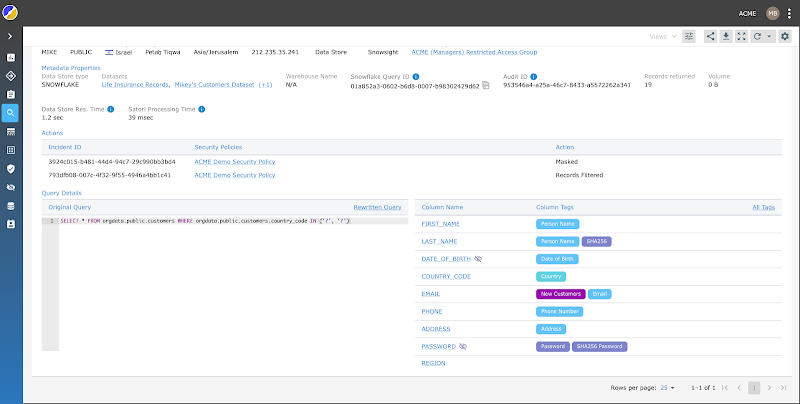
Now Nick can see who accessed which delicate data and when in a solitary frame. He can look at all details obtain and audit logs throughout all platforms, so delicate information entry is no lengthier “buried”. Nick can also see which security policies have been applied and quickly update the security procedures and obtain specifications.
Implementing Security and Compliance Policies
Satori is quickly carried out and can get Nick up and functioning across ACME’s databases, information warehouses and lakes in times or hours in its place of months.

This is for the reason that Satori does not adjust everything in ACME’s details stores, so there is no supplemental coding essential, or improvements to the data only the security policies and prerequisites need to have to be used.
Examine how uncomplicated it is to established and put into action security policies and compliance demands with Satori and take a examination generate.
Totally Automated
Satori automates the process of obtaining and classifying delicate facts, applying the relevant security insurance policies, and then granting and revoking access controls. The ability to immediately uncover sensitive knowledge is invaluable to Nick because he is not the real proprietor of the databases, information warehouses or lakes exactly where the info is saved.
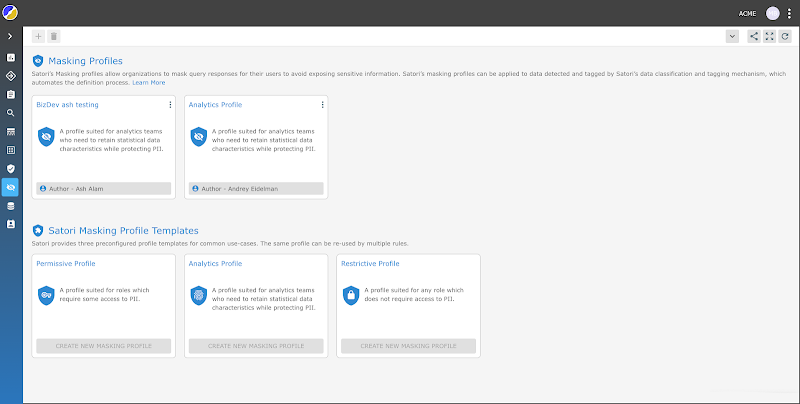
Nick now can handle the implementation of security policies, when regulations are updated, and we all know this takes place. He can speedily and simply employ the up to date demands and reduce the probability of failing an audit or even worse.
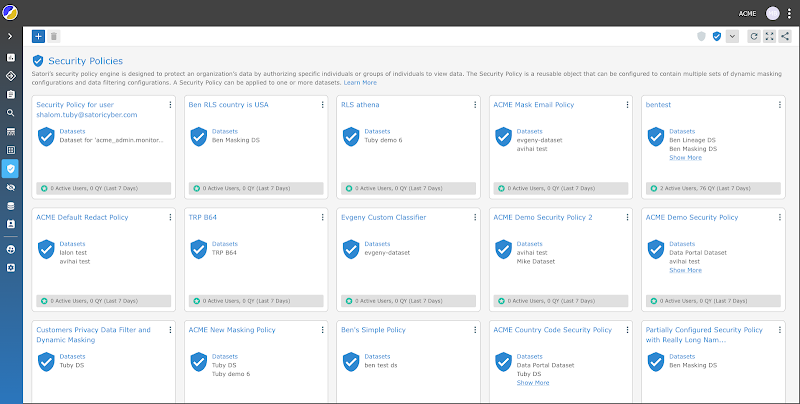
Nick is delighted because he can quickly implement the important prerequisites. The facts consumers are satisfied mainly because making use of Satori boosts the degree of security, but would not adjust or delay their consumer working experience. As a bonus, the information engineers are also content simply because they don’t have to fear about Nick’s nagging to constantly update and put into practice security procedures.
Is a Info Security Platform a Great Match?
Not absolutely everyone involves a information security platform, in some scenarios, it is more simple and a lot easier to carry on with small business as standard. However, if a business enterprise has any of the subsequent conditions, then a data security platform is necessary to protected details.
- Sensitive details
- Various knowledge consumers
- Several databases, data warehouses or knowledge lakes
Satori’s Information Security Platform
Satori’s automatic information security platform aided Nick attain possession about the information he is accountable for. This enabled him to concentrate on the security and compliance pieces of his job. Nick can automate all procedures from seeking out sensitive info to making use of and imposing security policies. He often has entire visibility of knowledge accessibility and can overview the audit and security logs speedily and effortlessly.
To test Satori for you, take a take a look at drive or e-book a demo conference with Satori.
Uncovered this short article interesting? Adhere to us on Twitter and LinkedIn to go through much more exclusive information we write-up.
Some elements of this short article are sourced from:
thehackernews.com

 New Threat Actor WIP26 Targeting Telecom Service Providers in the Middle East
New Threat Actor WIP26 Targeting Telecom Service Providers in the Middle East