The risk actor acknowledged as ChamelGang has been observed using a previously undocumented implant to backdoor Linux units, marking a new enlargement of the threat actor’s capabilities.
The malware, dubbed ChamelDoH by Stairwell, is a C++-based software for speaking via DNS-over-HTTPS (DoH) tunneling.
ChamelGang was first outed by Russian cybersecurity organization Positive Systems in September 2021, detailing its attacks on gas, energy, and aviation manufacturing industries in Russia, the U.S., India, Nepal, Taiwan, and Japan.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Attack chains mounted by the actor have leveraged vulnerabilities in Microsoft Exchange servers and Crimson Hat JBoss Enterprise Software to acquire initial obtain and have out info theft attacks working with a passive backdoor identified as DoorMe.

“This is a native IIS module that is registered as a filter by means of which HTTP requests and responses are processed,” Favourable Systems explained at the time. “Its principle of operation is strange: the backdoor processes only all those requests in which the appropriate cookie parameter is set.”
The Linux backdoor learned by Stairwell, for its component, is created to capture process information and is able of remote accessibility functions such as file upload, download, deletion, and shell command execution.
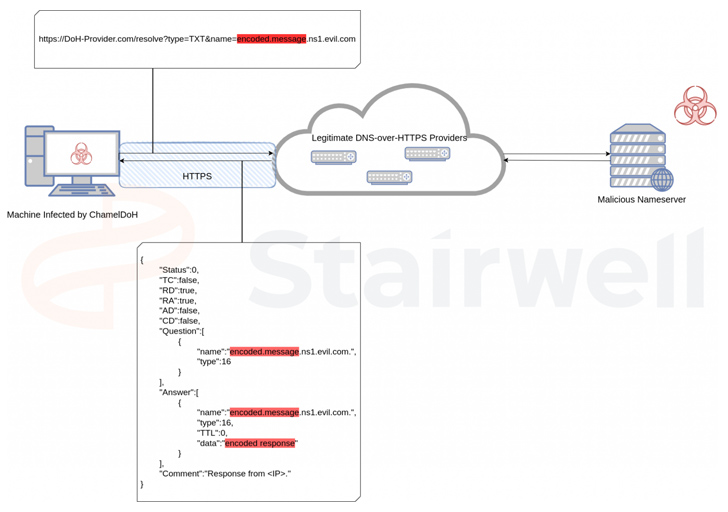
What would make ChamelDoH exclusive is its novel communication process of employing DoH, which is used to complete Area Name Procedure (DNS) resolution by means of the HTTPS protocol, to send DNS TXT requests to a rogue nameserver.
“Because of to these DoH companies becoming usually used DNS servers [i.e., Cloudflare and Google] for genuine site visitors, they simply cannot very easily be blocked enterprise-vast,” Stairwell researcher Daniel Mayer mentioned.
The use of DoH for command-and-handle (C2) also presents extra added benefits for the menace actor in that the requests are not able to be intercepted by usually means of an adversary-in-the-middle (AitM) attack owing to the use of the HTTPS protocol.
Impending WEBINAR🔐 Mastering API Security: Understanding Your Genuine Attack Area
Find the untapped vulnerabilities in your API ecosystem and consider proactive measures towards ironclad security. Join our insightful webinar!
Sign up for the Session.wn-button,.wn-label,.wn-label:just afterexhibit:inline-block.verify_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-size:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.wn-label:soon afterwidth:50pxheight:6pxcontent:”border-top rated:2px reliable #d9deffmargin: 8px.wn-titlefont-dimension:21pxpadding:10px 0font-excess weight:900textual content-align:leftline-height:33px.wn-descriptiontextual content-align:leftfont-dimension:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-colour:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-body weight:500letter-spacing:.2px
This also indicates that security alternatives can’t identify and prohibit destructive DoH requests and sever the communications, thereby turning it to an encrypted channel among a compromised host and the C2 server.
“The consequence of this tactic is akin to C2 by using domain fronting, wherever visitors is sent to a respectable company hosted on a CDN, but redirected to a C2 server by using the request’s Host header – equally detection and prevention are difficult,” Mayer stated.
The California-dependent cybersecurity firm mentioned it detected a whole of 10 ChamelDoH samples on VirusTotal, 1 of which was uploaded back again on December 14, 2022.
The most recent conclusions clearly show that the “group has also devoted sizeable time and effort and hard work to investigating and establishing an equally sturdy toolset for Linux intrusions,” Mayer mentioned.
Uncovered this posting exciting? Observe us on Twitter and LinkedIn to read a lot more unique information we publish.
Some pieces of this write-up are sourced from:
thehackernews.com


 Activities in the Cybercrime Underground Require a New Approach to Cybersecurity
Activities in the Cybercrime Underground Require a New Approach to Cybersecurity