Cybersecurity researchers have uncovered formerly undocumented payloads related with a Romanian danger actor named Diicot, revealing its potential for launching distributed denial-of-company (DDoS) attacks.
“The Diicot identify is major, as it truly is also the name of the Romanian organized crime and anti-terrorism policing device,” Cado Security claimed in a specialized report. “In addition, artifacts from the group’s strategies have messaging and imagery linked to this corporation.”
Diicot (née Mexals) was initial documented by Bitdefender in July 2021, uncovering the actor’s use of a Go-primarily based SSH brute-forcer instrument known as Diicot Brute to breach Linux hosts as part of a cryptojacking marketing campaign.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Then previously this April, Akamai disclosed what it described as a “resurgence” of the 2021 action which is believed to have started all-around Oct 2022, netting the actor about $10,000 in illicit gains.

“The attackers use a lengthy chain of payloads before ultimately dropping a Monero cryptominer,” Akamai researcher Stiv Kupchik explained at the time. “New abilities involve use of a Secure Shell Protocol (SSH) worm module, improved reporting, much better payload obfuscation, and a new LAN spreader module.”
The most recent examination from Cado Security displays that the group is also deploying an off-the-shelf botnet referred to as Cayosin, a malware loved ones that shares traits with Qbot and Mirai.
The development is a sign that the threat actor now possesses the capacity to mount DDoS attacks. Other things to do carried out by the team contain doxxing of rival hacking groups and its reliance on Discord for command-and-manage and info exfiltration.
“Deployment of this agent was specific at routers jogging the Linux-based mostly embedded gadgets operating procedure, OpenWrt,” the cybersecurity firm claimed. “The use of Cayosin demonstrates Diicot’s willingness to conduct a assortment of attacks (not just cryptojacking) relying on the variety of targets they experience.”
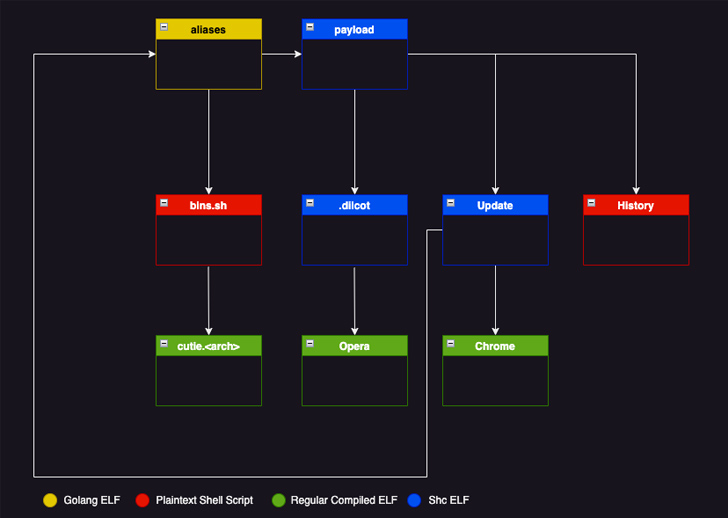
Diicot’s compromise chains have remained mostly regular, leveraging the tailor made SSH brute-forcing utility to attain a foothold and fall additional malware this kind of as the Mirai variant and the crypto miner.
Some of the other resources applied by the actor are as follows –
- Chrome – An internet scanner primarily based on Zmap that can generate the effects of the operation to a textual content file (“bios.txt”).
- Update – An executable that fetches and executes the SSH brute-forcer and Chrome if they don’t exist in the method.
- Heritage – A shell script which is designed to operate Update
The SSH brute-forcer instrument (aka aliases), for its section, parses the text file output of Chrome to crack into every single of the determined IP addresses, and if effective, establishes remote link to the IP deal with.
Approaching WEBINAR🔐 Mastering API Security: Understanding Your Real Attack Area
Learn the untapped vulnerabilities in your API ecosystem and consider proactive techniques towards ironclad security. Be part of our insightful webinar!
Join the Session.wn-button,.wn-label,.wn-label:immediately aftershow:inline-block.test_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px strong #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimension:13pxmargin:20px 0font-pounds:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-top rated:2px stable #d9deffmargin: 8px.wn-titlefont-sizing:21pxpadding:10px 0font-body weight:900textual content-align:leftline-top:33px.wn-descriptiontext-align:leftfont-measurement:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-color:#4469f5font-dimensions:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
This is then followed by managing a collection of commands to profile the infected host and applying it to either deploy a cryptominer or make it act as a spreader if the machine’s CPU has less than 4 cores.
To mitigate this kind of attacks, organizations are proposed to apply SSH hardening and firewall policies to limit SSH accessibility to precise IP addresses.
“This marketing campaign exclusively targets SSH servers uncovered to the internet with password authentication enabled,” Cado Security explained. “The username/password checklist they use is rather confined and includes default and simply-guessed credential pairs.”
Uncovered this short article intriguing? Observe us on Twitter and LinkedIn to read more distinctive material we post.
Some areas of this article are sourced from:
thehackernews.com

 ChamelDoH: New Linux Backdoor Utilizing DNS-over-HTTPS Tunneling for Covert CnC
ChamelDoH: New Linux Backdoor Utilizing DNS-over-HTTPS Tunneling for Covert CnC