Cybersecurity scientists have identified an up-to-date variation of an Android banking malware identified as Chameleon that has expanded its targeting to include things like customers in the U.K. and Italy.
“Symbolizing a restructured and increased iteration of its predecessor, this progressed Chameleon variant excels in executing Machine Takeover (DTO) utilizing the accessibility services, all although expanding its focused area,” Dutch mobile security agency ThreatFabric explained in a report shared with The Hacker Information.
Chameleon was formerly documented by Cyble in April 2023, noting that it had been applied to solitary out end users in Australia and Poland since at least January. Like other banking malware, it’s regarded to abuse its permissions to Android’s accessibility support to harvest sensitive facts and carry out overlay attacks.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The rogue apps containing the previously variation were hosted on phishing web pages and located to impersonate genuine institutions in the countries, these kinds of as the Australian Taxation Business office (ATO) and a cryptocurrency buying and selling platform identified as CoinSpot, in an try to lend them a veil of believability.
The newest findings from ThreatFabric display that the banking trojan is now getting delivered through Zombinder, an off-the-shelf dropper-as-a-support (DaaS) that is bought to other risk actors and which can be utilized to “bind” malicious payloads to reputable apps.
Upcoming WEBINAR Beat AI-Run Threats with Zero Have confidence in – Webinar for Security Industry experts
Standard security steps will not slash it in today’s environment. It is really time for Zero Have faith in Security. Safe your information like in no way just before.
Be a part of Now
Even though the providing was suspected to have been shut down previously this calendar year, it resurfaced past month, advertising abilities to bypass the ‘Restricted Settings’ element in Android to install malware on equipment and receive obtain to the accessibility services.
Each the destructive artifacts distributing Chameleon masquerade as the Google Chrome web browser. Their package deal names are outlined under –
- Z72645c414ce232f45.Z35aad4dde2ff09b48
- com.fast paced.lady
A noteworthy aspect of the improved variant is its capability to carry out Product Takeover (DTO) fraud, which leverages the accessibility company to perform unauthorized actions on the victim’s behalf.

But in order to trick consumers into enabling the location, the malware checks the Android variation on the set up unit and if it truly is observed to be Android 13 or later on, prompts the user to convert it on.
“On getting confirmation of Android 13 Limited Settings getting present on the contaminated device, the banking trojan initiates the loading of an HTML webpage,” ThreatFabric discussed. “The web site is guiding end users through a guide phase-by-action system to enable the accessibility assistance on Android 13 and bigger.”
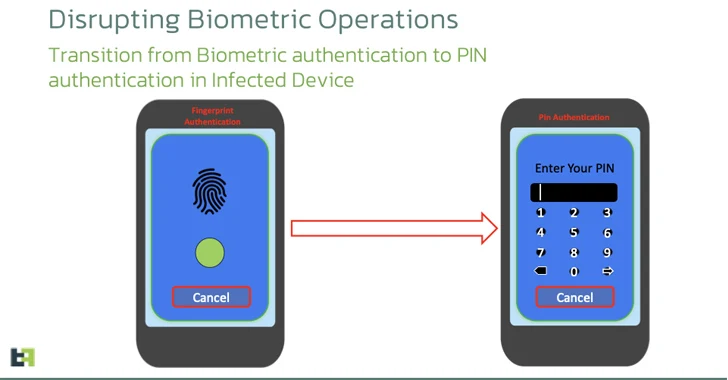
A further new addition is the use of Android APIs to disrupt the biometric functions of the qualified product by covertly transitioning the lock monitor authentication mechanism to a PIN so as to make it possible for the malware to “unlock the machine at will” working with the accessibility provider.

“The emergence of the new Chameleon banking trojan is an additional example of the innovative and adaptive threat landscape in the Android ecosystem,” the organization explained. “Evolving from its before iteration, this variant demonstrates improved resilience and highly developed new functions.”
The advancement comes as Zimperium revealed that 29 malware households – 10 of them new – specific 1,800 banking applications across 61 nations over the earlier year. The new active people incorporate Nexus, Godfather, PixPirate, Saderat, Hook, PixBankBot, Xenomorph v3, Vultur, BrasDex, and GoatRAT.
The U.S. best nations around the world targeted comprise the U.S. (109 financial institution apps), the U.K. (48), Italy (44), Australia (34), Turkey (32), France (30), Spain (29), Portugal (27), Germany (23), Canada (17), and Brazil (11). The most specific fiscal expert services apps are PhonePe (India), WeChat, Financial institution of America, Nicely Fargo, (U.S.), Binance (Malta), Barclays (U.K.), QNB Finansbank (Turkey), and CaixaBank (Spain).
“Regular banking apps keep on being the primary focus on, with a staggering 1103 apps – accounting for 61% of the targets – when the rising FinTech and Trading apps are now in the crosshairs, making up the remaining 39%,” the business stated.
Discovered this short article appealing? Observe us on Twitter and LinkedIn to browse additional exceptional articles we write-up.
Some components of this post are sourced from:
thehackernews.com

 New JavaScript Malware Targeted 50,000+ Users at Dozens of Banks Worldwide
New JavaScript Malware Targeted 50,000+ Users at Dozens of Banks Worldwide