A new assessment of the sophisticated industrial spy ware referred to as Predator has revealed that its ability to persist in between reboots is made available as an “increase-on feature” and that it is dependent on the licensing options opted by a buyer.
“In 2021, Predator spy ware could not survive a reboot on the contaminated Android procedure (it experienced it on iOS),” Cisco Talos scientists Mike Gentile, Asheer Malhotra, and Vitor Ventura claimed in a report shared with The Hacker Information. “Nonetheless, by April 2022, that ability was getting presented to their clients.”
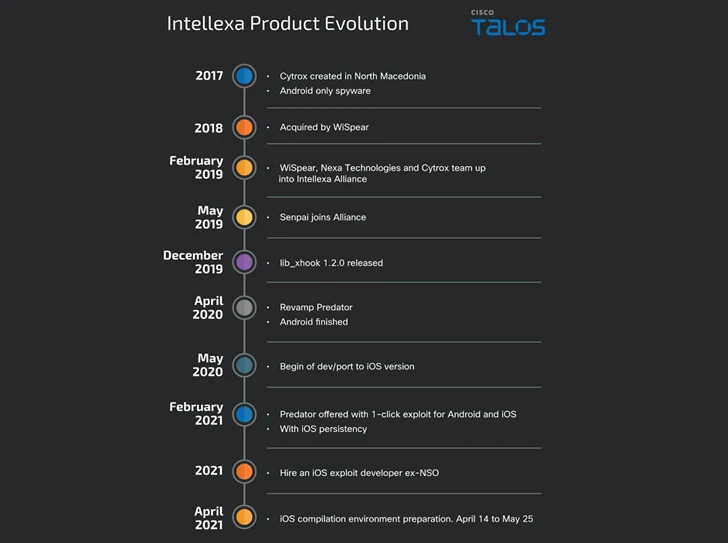
Predator is the merchandise of a consortium called the Intellexa Alliance, which includes Cytrox (subsequently acquired by WiSpear), Nexa Technologies, and Senpai Systems. Equally Cytrox and Intellexa have been extra to the Entity List by the U.S. in July 2023 for “trafficking in cyber exploits applied to get entry to facts systems.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The hottest conclusions arrive additional than 6 months following the cybersecurity vendor comprehensive the interior workings of Predator and its harmonious equation with a further loader ingredient identified as Alien.
“Alien is critical to Predator’s productive operating, including the further components loaded by Predator on demand from customers,” Malhotra advised The Hacker News at the time. “The partnership amongst Alien and Predator is extremely symbiotic, demanding them to continually perform in tandem to spy on victims.”
Approaching WEBINAR Beat AI-Powered Threats with Zero Belief – Webinar for Security Gurus
Conventional security measures will never slice it in present-day earth. It is time for Zero Trust Security. Protected your details like by no means prior to.
Be part of Now
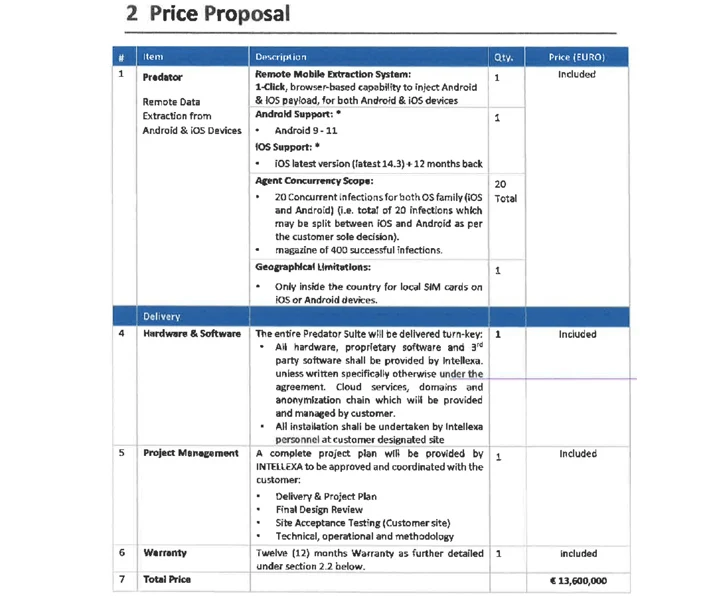
Predator, which can focus on both equally Android and iOS, has been explained as a “distant mobile extraction method” that’s sold on a licensing model that run into tens of millions of bucks based mostly on the exploit applied for first accessibility and the variety of concurrent infections, putting them out of attain of script kiddies and amateur criminals.
Spyware such as Predator and Pegasus, which is created by NSO Group, generally depend on zero-day exploit chains in Android, iOS, and web browsers as covert intrusion vectors. As Apple and Google continue to plug the security gaps, these exploit chains may possibly be rendered ineffective, forcing them to go again to the drawing board.
Nonetheless, it can be worthy of noting that the organizations at the rear of mercenary surveillance resources can also procure possibly whole or partial exploit chains from exploit brokers and manner them into an operational exploit that can be employed to effectively breach target gadgets.
Yet another crucial factor of Intellexa’s business model is that offloads the perform of environment up the attack infrastructure to the prospects them selves, leaving it with area for plausible deniability need to the strategies occur to mild (as it inevitably does).
“The shipping and delivery of Intellexa’s supporting hardware is done at a terminal or airport,” the researchers reported.
“This shipping and delivery method is acknowledged as Cost Insurance and Freight (CIF), which is component of the transport industry’s jargon (‘Incoterms’). This mechanism will allow Intellexa to declare that they have no visibility of exactly where the methods are deployed and at some point located.”

On prime of that, Intellexa possesses “1st-hand expertise” of regardless of whether their consumers are undertaking surveillance operations outside the house their personal borders owing to the point that the functions are intrinsically linked to the license, which, by default, is restricted to a one phone country code prefix.
This geographic limitation, even so, can be loosened for an more cost.
Cisco Talos mentioned that while general public publicity of private-sector offensive actors and their campaigns have been profitable at attribution endeavours, it has experienced minimal effect on their potential to carry out and increase their business across the entire world, even if it could affect their prospects, these as governments.
“It may perhaps boost the expenditures by creating them purchase or develop new exploit chains but these sellers surface to have seamlessly acquired new exploit chains, enabling them to stay in organization by leaping from one established of exploits to one more as a means of first obtain,” the scientists mentioned.
“What is needed is the general public disclosure of complex analyses of the cell adware and tangible samples enabling community scrutiny of the malware. These types of public disclosures will not only permit greater analyses and travel detection endeavours but also impose development fees on suppliers to constantly evolve their implants.”
Uncovered this write-up interesting? Stick to us on Twitter and LinkedIn to study a lot more exceptional material we put up.
Some pieces of this article are sourced from:
thehackernews.com


 Chameleon Android Banking Trojan Variant Bypasses Biometric Authentication
Chameleon Android Banking Trojan Variant Bypasses Biometric Authentication