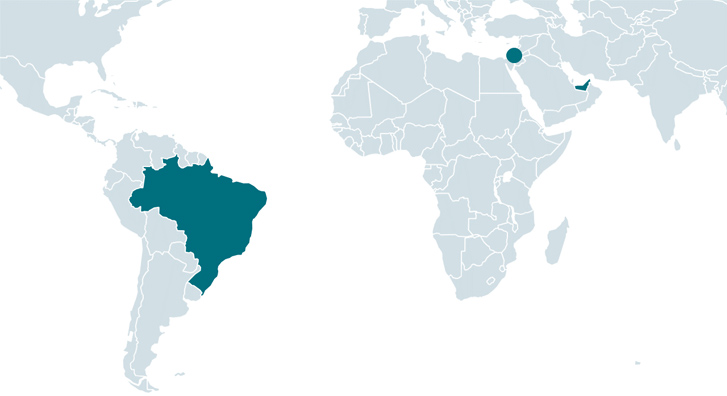
The Iranian menace actor regarded as Charming Kiten has been joined to a new wave of attacks focusing on various entities in Brazil, Israel, and the U.A.E. using a formerly undocumented backdoor named Sponsor.
Slovak cybersecurity company is tracking the cluster under the name Ballistic Bobcat. Victimology styles advise that the group largely singles out instruction, federal government, and healthcare corporations, as nicely as human legal rights activists and journalists.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
At minimum 34 victims of Sponsor have been detected to day, with the earliest cases of deployment courting back to September 2021.
“The Sponsor backdoor uses configuration data files stored on disk,” ESET researcher Adam Burgher stated in a new report released today. “These documents are discreetly deployed by batch data files and deliberately made to appear innocuous, therefore trying to evade detection by scanning engines.”
Upcoming WEBINARWay Too Susceptible: Uncovering the Condition of the Identity Attack Surface area
Attained MFA? PAM? Support account defense? Obtain out how properly-equipped your corporation actually is towards id threats
Supercharge Your Expertise
The marketing campaign, dubbed Sponsoring Access, includes getting initial access by opportunistically exploiting regarded vulnerabilities in internet-uncovered Microsoft Trade servers to perform post-compromise actions, echoing an advisory issued by Australia, the U.K., and the U.S. in November 2021.
In a person incident specific by ESET, an unidentified Israeli corporation working an insurance policies marketplace is claimed to have been infiltrated by the adversary in August 2021 to supply following-phase payloads this kind of as PowerLess, Plink, and a Go-based open up-resource put up-exploitation toolkit termed Merlin above the subsequent couple of months.
“The Merlin agent executed a Meterpreter reverse shell that termed back to a new [command-and-control] server,” Burgher mentioned. “On December 12th, 2021, the reverse shell dropped a batch file, set up.bat, and inside of minutes of executing the batch file, Ballistic Bobcat operators pushed their latest backdoor, Sponsor.”
Written in C++, Sponsor is designed to get host details and procedure guidelines received from a distant server, the effects of which are sent again to the server. This incorporates command and file execution, file obtain, and update the listing of attacker-controlled servers.
“Ballistic Bobcat proceeds to function on a scan-and-exploit model, wanting for targets of prospect with unpatched vulnerabilities in internet-uncovered Microsoft Trade servers,” Burgher explained. “The team carries on to use a assorted open-resource toolset supplemented with several tailor made applications, which include its Sponsor backdoor.”
Discovered this posting exciting? Comply with us on Twitter and LinkedIn to read through extra special articles we submit.
Some parts of this short article are sourced from:
thehackernews.com


 How to Prevent API Breaches: A Guide to Robust Security
How to Prevent API Breaches: A Guide to Robust Security