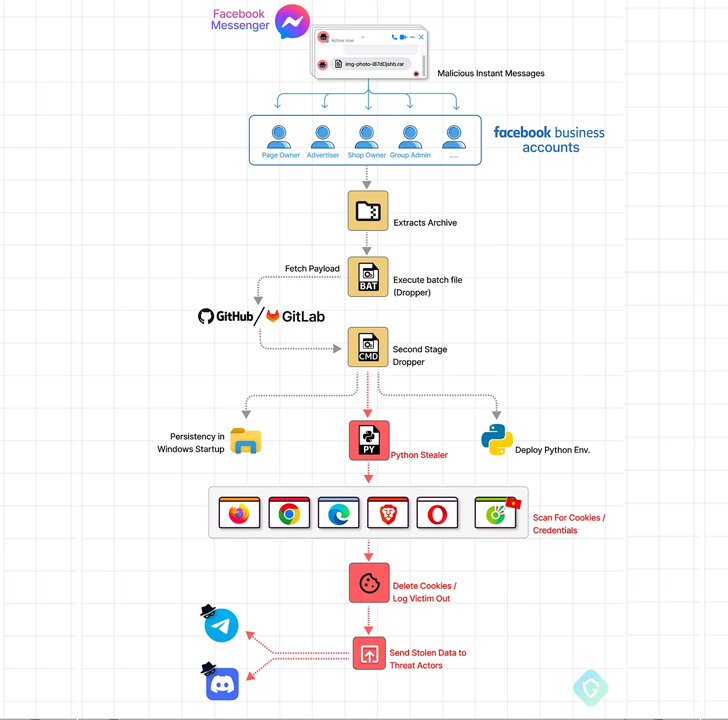
A new phishing attack is leveraging Facebook Messenger to propagate messages with destructive attachments from a “swarm of phony and hijacked personalized accounts” with the greatest objective of using about the targets’ accounts.
“Originating yet all over again from a Vietnamese-centered team, this marketing campaign employs a little compressed file attachment that packs a potent Python-based stealer dropped in a multi-phase process complete of very simple nevertheless productive obfuscation approaches,” Guardio Labs researcher Oleg Zaytsev mentioned in an analysis released more than the weekend.
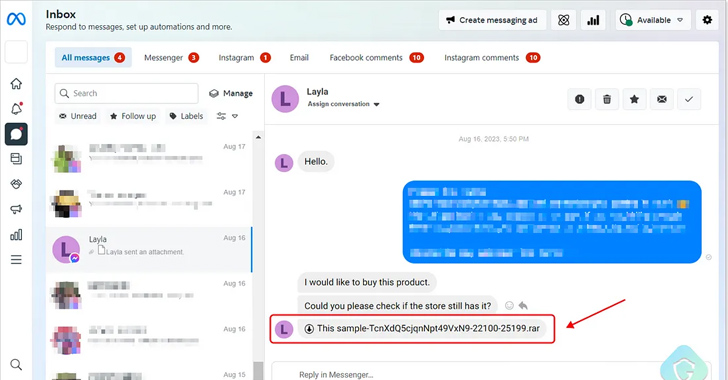
In these attacks, dubbed MrTonyScam, potential victims are despatched messages that entice them into clicking on the RAR and ZIP archive attachments, leading to the deployment of a dropper that fetches the upcoming-stage from a GitHub or GitLab repository.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This payload is yet another archive file that includes a CMD file, which, in transform, harbors an obfuscated Python-dependent stealer to exfiltrate all cookies and login credentials from distinct web browsers to an actor-managed Telegram or Discord API endpoint.

A clever tactic adopted by the adversary will involve deletes all cookies right after thieving them, properly logging victims out of their possess accounts, at which position the scammers hijack their periods applying the stolen cookies to adjust their passwords and seize command of them.
The threat actor’s hyperlinks to Vietnam comes from the existence of Vietnamese language references in the resource code of the Python stealer and the inclusion of Cốc Cốc, a Chromium-centered browser well-known in the region.
Regardless of the actuality that triggering the an infection demands user conversation to obtain a file, unzip, and execute the attachment, Guardio Labs identified that the campaign has witnessed a significant results charge wherever 1 out of 250 victims are approximated to have been infected above the very last 30 days on your own.
A greater part of the compromises have been claimed in the U.S., Australia, Canada, France, Germany, Indonesia, Japan, Nepal, Spain, the Philippines, and Vietnam, among others.
“Fb Accounts with status, seller rating, and higher variety of followers can be quickly monetized on dark markets,” Zaytsev said. “People are used to attain a wide audience to spread ads as perfectly as extra scams.”
Approaching WEBINARWay Also Vulnerable: Uncovering the Point out of the Identity Attack Area
Reached MFA? PAM? Service account safety? Come across out how properly-outfitted your firm genuinely is towards identity threats
Supercharge Your Techniques
The disclosure arrives days just after WithSecure and Zscaler ThreatLabz detailed new Ducktail and Duckport strategies that target Meta Business and Fb accounts using malverposting ways.
“The Vietnamese-centric factor of these threats and large diploma of overlaps in conditions of abilities, infrastructure, and victimology suggests lively functioning associations among different danger actors, shared tooling and TTPs across these menace teams, or a fractured and services-oriented Vietnamese cybercriminal ecosystem (akin to ransomware-as-a-services design) centered about social media platforms this sort of as Fb,” WithSecure pointed out.
Identified this article exciting? Adhere to us on Twitter and LinkedIn to read additional exclusive content material we put up.
Some pieces of this write-up are sourced from:
thehackernews.com

 Charming Kiten’s New Backdoor ‘Sponsor’ Targets Brazil, Israel, and U.A.E.
Charming Kiten’s New Backdoor ‘Sponsor’ Targets Brazil, Israel, and U.A.E.