Germany’s Federal Business office for the Defense of the Structure (BfV) has warned of cyber attacks focusing on Iranian individuals and organizations in the region due to the fact the conclude of 2022.
“The cyber attacks had been largely directed versus dissident organizations and men and women – this sort of as lawyers, journalists, or human legal rights activists – inside and exterior Iran,” the company mentioned in an advisory.
The intrusions have been attributed to a menace actor named Charming Kitten, which is also tracked beneath the names APT35, Mint Sandstorm, TA453 and Yellow Garuda.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Even though Iranian nation-condition actors lag behind their Russian and Chinese counterparts in sophistication, they have shown a continued progression of instruments and techniques, including an arsenal of custom malware to facilitate facts accumulating and quickly exploiting n-working day security flaws to get hold of preliminary entry.

Charming Kitten, in specific, has a extended, storied historical past of leveraging elaborate social engineering and fictitious on the net identities that are tailor-manufactured to concentrate on victims. It also impersonates true journalists and NGO staff members in a bid to make rapport and increase the chance of achievement of the attacks.
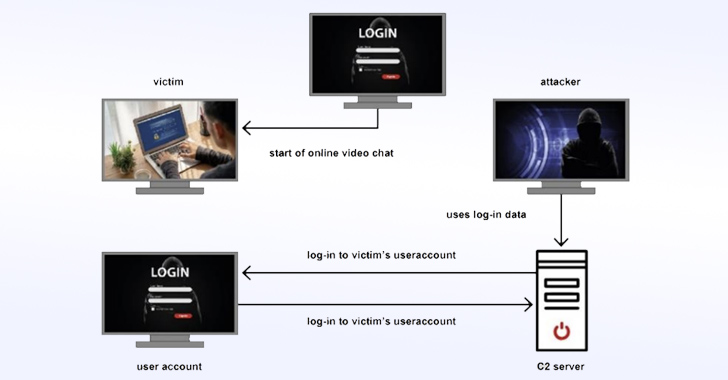
After a effective call is designed, the hacking crew has been observed sending links to an online video clip chat that, when clicked, urge victims to enter their login details on a phishing web page, proficiently ensuing in credential theft. The phishing internet site impersonates a legit on line service company these kinds of as Google or Microsoft.
“If an on the internet video clip chat takes place, it serves to conceal the attack,” BfV mentioned. “Soon after logging in to the victim’s consumer account from a C2 server6, the attacker is equipped to obtain the full user facts, e.g. by usually means of Google Takeout.”
It is well worth noting that the Google Danger Analysis Team (TAG), in August 2022, specific a malware termed HYPERSCRAPE utilized by the risk actor to retrieve person information from Gmail, Yahoo!, and Microsoft Outlook accounts.

The attacks also mirror prior findings from Certfa Lab and Human Legal rights Look at (HRW), which disclosed a credential phishing campaign aimed at human legal rights activists, journalists, scientists, teachers, diplomats, and politicians doing work in the Middle East around the similar time.
The development comes as Sophos discovered a cell malware marketing campaign focusing on customers of 4 Iranian banking institutions, Financial institution Mellat, Financial institution Saderat, Resalat Lender, and Central Lender of Iran, with as quite a few as 40 bogus Android applications developed to steal sensitive info.
“All the apps, which were offered for download between December 2022 and May well 2023, gather internet banking login qualifications and credit card facts, and have many other capabilities,” security researcher Pankaj Kohli said in a report posted late very last month.
This contains “hiding their icons to retain stealth and intercepting incoming SMS messages which some banking institutions use as component of multi-factor authentication schemes.” Also present is a attribute to research the contaminated gadget for a number of other apps relating to banking, payment, or cryptocurrency.
Discovered this report attention-grabbing? Comply with us on Twitter and LinkedIn to study more exclusive information we post.
Some elements of this short article are sourced from:
thehackernews.com

 New Financial Malware ‘JanelaRAT’ Targets Latin American Users
New Financial Malware ‘JanelaRAT’ Targets Latin American Users