Why SaaS Security Is a Obstacle
In present-day digital landscape, corporations are significantly relying on Application-as-a-Company (SaaS) programs to travel their operations. On the other hand, this prevalent adoption has also opened the doorways to new security pitfalls and vulnerabilities.
The SaaS security attack surface carries on to widen. It commenced with controlling misconfigurations and now involves a holistic tactic to handling the entire SaaS ecosystem. This involves the continuous monitoring and management of consumer accessibility, roles and permissions, 3rd party apps mounted by customers, dangers deriving from SaaS consumer units and Identification Danger Detection & Response (ITDR).
There are a assortment of reasons that SaaS security is so elaborate today. To begin with, there are a diverse array of programs, each individual possessing its very own UI and terminology. And these environments are dynamic, from SaaS sellers being familiar with the worth of security and constantly boosting their apps with modern security measures to the at any time-evolving user governance expected such as onboarding, deprovisioning, changes in consumer obtain. These controls are efficient only when continuously governed, for just about every application and each and every person. If that’s not ample, these applications are managed by dispersed organization departments, earning it almost difficult for the security staff to carry out their security policies.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
ITDR Spelled out
To tackle the Id Threat Detection & Response challenge in the SaaS ecosystem, SaaS security options need to have a powerful alternative that detects and responds to identity-related security threats dependent on key Indicators of Compromise (IOCs) and User and Entity Conduct Analytics (UEBA). These indicators provide forensic signs of a prospective breach, this kind of as malware, facts breaches, abnormal behavior, and other suspicious functions.
ITDR is made to tackle different SaaS-associated threats, which include password-primarily based attacks, IP habits anomalies, account-centered detection, OAuth-centered attacks, unauthorized doc entry, uncommon person agent functions, and additional. By offering a extensive suite of protecting steps, companies have to proactively protect their SaaS stack and be certain the integrity of their delicate facts.
When it arrives to dealing with SaaS threats, existing menace detection and identity management methods don’t go considerably more than enough. Modern SaaS environments are elaborate and ITDR abilities within these landscapes need deep awareness and verified experience.
Maor Bin, Co-Founder and CEO at Adaptive Shield had this to say about the new iteration of SaaS-ITDR, “Present ITDR alternatives target on Endpoint and Lively Listing safety and do not layer the sophisticated SaaS atmosphere. On-prem Energetic Listing will before long become a legacy technology and as on-prem is shifting to SaaS, this will recreate a gap in identity security posture management in SaaS applications.”
This hole that Bin mentions is critical for SaaS security options to close and that is why Adaptive Shield has taken strides and brought out abilities to do just that.
Discover far more about ITDR and other core use scenarios to reinforce your SaaS security
Critical ITDR Abilities for SaaS Ecosystems
Your ITDR must be crafted on the foundation of a deep understanding of SaaS properties and Identification Governance inside of this landscape. Make positive you find a solution that is based mostly on a quite wide coverage of SaaS apps, who deeply understands the SaaS entire world and provides precise threat detection by means of contextualization of a selection of resources and gatherings.
As a signifies of avoidance and to start with layer of protection, the SSPM operates as the security layer in the Identification Material to establish robust consumer governance. This involves too much permissions, accessibility entitlement, person deprovisioning, and additional, across the whole SaaS stack. Corporations should really get deep and consolidated visibility and management of person accounts, roles, permissions, privileged buyers, and actions.
As a next layer of threat defense, your SaaS security solution, like Adaptive Shield, ITDR capabilities offer extensive protection in detecting anomalies and Ways, Approaches, and Treatments (TTPs). By concentrating on context and building person and company profiles, it improves the precision of these detection alerts. Additionally, being familiar with predicted habits designs and looking at elements these as user accessibility, permissions, and equipment, enables the answer to superior recognize and prioritize alerts.
 Screenshot 1: Watch exhibiting threats by time with MITRE ATT&CK mapping
Screenshot 1: Watch exhibiting threats by time with MITRE ATT&CK mapping
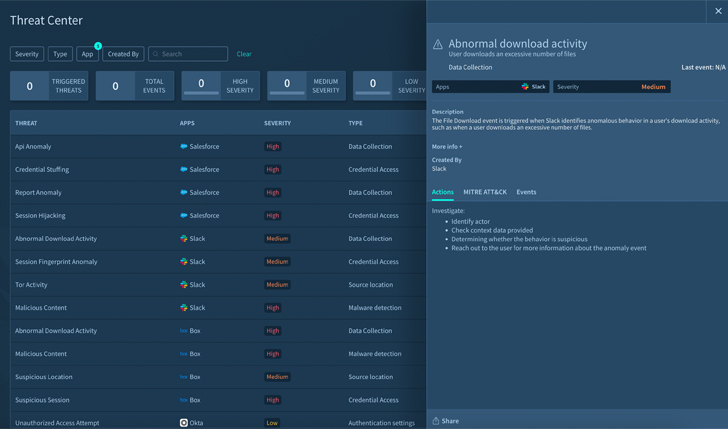 Screenshot 2: Danger centre exhibiting all monitored function
Screenshot 2: Danger centre exhibiting all monitored function
Important Capabilities Contain:
- Indicator of Compromise (IOC) Detection: Collection of proof indicating that the organization’s SaaS applications are beneath attack or have been compromised. IOCs can involve information from IP addresses, domain names, URLs and a lot more.
- Consumer and Entity Conduct Analytics (UEBA): Detection of behavioral anomalies, Adaptive Shield’s ITDR can discover risk actors as they navigate by way of the organization’s purposes, presenting proactive risk detection.
Comprehensive Security Management
When securing your SaaS environments, ensure your security platform goes over and above identification danger detection and response. Your remedy really should consist of a range of abilities that bolster your overall security administration and offer you a holistic prevention design for securing the SaaS Identification Fabric:
- Misconfiguration Administration: Detect security drifts across all security controls and get detailed remediation plans to guarantee proper configuration and prevent log-associated threats.
- Identification and Obtain Governance: Consolidate visibility of user accounts, permissions, and pursuits throughout all SaaS applications, enabling efficient risk management and making sure correct access concentrations. Detect and mitigate the risks involved with disabled or dormant accounts.
- SaaS-to-SaaS Access and Discovery: Obtain visibility into linked applications, authentic or malicious, and assess the amount of risk they pose to your SaaS environment.
- System-to-SaaS Risk Administration: Acquire context and visibility to efficiently control threats originating from SaaS end users and their related gadgets.
With unparalleled insights and an array of attributes, Adaptive Protect empowers companies to secure their SaaS stack, avert details breaches, and safeguard their SaaS facts from emerging threats.
Get a 15-minute demo to see how you can safe your complete SaaS stack
Discovered this report interesting? Stick to us on Twitter and LinkedIn to examine much more unique content material we article.
Some parts of this short article are sourced from:
thehackernews.com


 Charming Kitten Targets Iranian Dissidents with Advanced Cyber Attacks
Charming Kitten Targets Iranian Dissidents with Advanced Cyber Attacks