A beforehand undocumented China-aligned threat actor has been linked to a set of adversary-in-the-middle (AitM) attacks that hijack update requests from authentic application to produce a innovative implant named NSPX30.
Slovak cybersecurity company ESET is tracking the superior persistent danger (APT) team beneath the name Blackwood. It is really said to be energetic due to the fact at least 2018.
The NSPX30 implant has been observed deployed by means of the update mechanisms of regarded application these kinds of as Tencent QQ, WPS Workplace, and Sogou Pinyin, with the attacks concentrating on Chinese and Japanese manufacturing, trading, and engineering corporations as very well as persons located in China, Japan, and the U.K.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
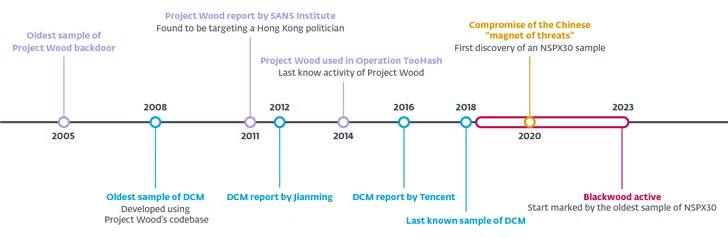
“NSPX30 is a multistage implant that contains a number of elements these types of as a dropper, an installer, loaders, an orchestrator, and a backdoor,” security researcher Facundo Muñoz stated. “Equally of the latter two have their possess sets of plugins.”
“The implant was developed about the attackers’ capacity to conduct packet interception, enabling NSPX30 operators to cover their infrastructure.”
The origins of the backdoor, which is also capable of bypassing several Chinese anti-malware options by allowlisting by itself, can be traced to yet another malware from January 2005 codenamed Venture Wood, which is designed to harvest system and network info, record keystrokes, and just take screenshots from sufferer systems.

Task Wood’s codebase has acted as the foundation for several implants, together with spawning variants like DCM (aka Dark Specter) in 2008, with the malware subsequently applied in attacks concentrating on folks of interest in Hong Kong and the Larger China space in 2012 and 2014.
NSPX30, the newest iteration of the implant, is shipped when attempts to obtain computer software updates from genuine servers making use of the (unencrypted) HTTP protocol results in a procedure compromise, paving the way for the deployment of a dropper DLL file.
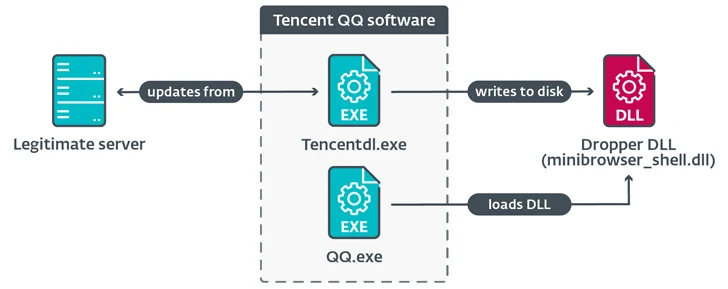
The malicious dropper deployed as aspect of the compromised update process makes several files on disk and executes “RsStub.exe,” a binary associated with the Growing Antivirus computer software so as to start “comx3.dll” by getting advantage of the reality the previous is prone to DLL side-loading.
“comx3.dll” capabilities as a loader to execute a 3rd file named “comx3.dll.txt,” which is an installer library responsible for activating the up coming-stage attack chain that culminates in the execution of the orchestrator part (“Earn.cfg”).
It is really at present not identified how the menace actors supply the dropper in the form of malicious updates, but Chinese threat actors like BlackTech, Evasive Panda, and Mustang Panda have leveraged compromised routers as a channel to distribute malware in the earlier.
ESET speculates that the attackers “are deploying a network implant in the networks of the victims, probably on vulnerable network appliances this kind of as routers or gateways.”
“The simple fact that we discovered no indications of targeted traffic redirection by using DNS could point out that when the hypothesized network implant intercepts unencrypted HTTP site visitors connected to updates, it replies with the NSPX30 implant’s dropper in the kind of a DLL, an executable file, or a ZIP archive containing the DLL.”

The orchestrator then proceeds to create two threads, 1 to receive the backdoor (“msfmtkl.dat”) and one more to load its plugins and insert exclusions to allowlist the loader DLLs to bypass Chinese anti-malware alternatives.
The backdoor is downloaded through an HTTP ask for to Baidu’s web page www.baidu[.]com, a legitimate Chinese research engine, with an uncommon Consumer-Agent string that masquerades the ask for as originating from the Internet Explorer browser on Windows 98.
The reaction from the server is then saved to a file from which the backdoor ingredient is extracted and loaded into memory.

NSPX30, as component of its initialization stage, also generates a passive UDP listening socket for acquiring instructions from the controller and exfiltrating data by very likely intercepting DNS query packets in get to anonymize its command-and-manage (C2) infrastructure.
The guidelines make it possible for the backdoor to make a reverse shell, gather file facts, terminate particular processes, capture screenshots, log keystrokes, and even uninstall by itself from the infected machine.
The disclosure arrives weeks following SecurityScorecard revealed new infrastructure connected to a different Beijing-nexus cyber espionage team recognised as Volt Hurricane (aka Bronze Silhouette) that leverages a botnet made by exploiting identified security flaws in end-of-lifestyle Cisco RV320/325 routers (CVE-2019-1652 and CVE-2019-1653) operating throughout Europe, North America, and Asia Pacific.
“Approximately 30% of them (325 of 1,116 units) communicated with two IP addresses beforehand named as proxy routers used for command-and-command (C2) communications, 174.138.56[.]21 and 159.203.113[.]25, in a 30-day interval,” the business explained.
“Volt Typhoon might purpose to use these compromised units to transfer stolen knowledge or hook up to focus on organizations’ networks.”
Discovered this report appealing? Follow us on Twitter and LinkedIn to go through additional distinctive articles we write-up.
Some components of this short article are sourced from:
thehackernews.com

 New CherryLoader Malware Mimics CherryTree to Deploy PrivEsc Exploits
New CherryLoader Malware Mimics CherryTree to Deploy PrivEsc Exploits