A new Go-based malware loader known as CherryLoader has been learned by threat hunters in the wild to produce extra payloads on to compromised hosts for adhere to-on exploitation.
Arctic Wolf Labs, which uncovered the new attack device in two the latest intrusions, stated the loader’s icon and name masquerades as the genuine CherryTree take note-getting application to dupe potential victims into setting up it.
“CherryLoader was employed to drop 1 of two privilege escalation instruments, PrintSpoofer or JuicyPotatoNG, which would then operate a batch file to establish persistence on the victim machine,” scientists Hady Azzam, Christopher Prest, and Steven Campbell mentioned.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In an additional novel twist, CherryLoader also packs modularized characteristics that make it possible for the menace actor to swap exploits without recompiling code.

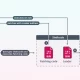
It’s currently not recognised how the loader is distributed, but the attack chains examined by the cybersecurity business display that CherryLoader (“cherrytree.exe”) and its associated documents (“NuxtSharp.Facts,”https://thehackernews.com/2024/01/”Spof.Facts,” and “Juicy.Info”) are contained in a RAR archive file (“Packed.rar”) hosted on the IP tackle 141.11.187[.]70.
Downloaded alongside with the RAR file is an executable (“key.exe”) which is utilised to unpack and launch the Golang binary, which only proceeds if the initial argument passed to it matches a really hard-coded MD5 password hash.
The loader subsequently decrypts “NuxtSharp.Info” and writes its contents to a file named “File.log” on disk that, in convert, is designed to decode and run “Spof.Information” as “12.log” employing a fileless method recognized as process ghosting that initially arrived to light-weight in June 2021.
“This system is modular in layout and will allow the menace actor to leverage other exploit code in spot of Spof.Knowledge,” the researchers reported. “In this situation, Juicy.Knowledge which consists of a diverse exploit, can be swapped in position with no recompiling File.log.”

The system connected with “12.log” is linked to an open up-source privilege escalation tool named PrintSpoofer, even though “Juicy.Information” is a further privilege escalation tool named JuicyPotatoNG.
A thriving privilege escalation is followed by the execution of a batch file script identified as “user.bat” to set up persistence on the host and disarm Microsoft Defender.
“CherryLoader is [a] newly determined multi-phase downloader that leverages distinct encryption procedures and other anti-analysis methods in an try to detonate alternative, publicly obtainable privilege escalation exploits devoid of getting to recompile any code,” the scientists concluded.
Found this write-up appealing? Adhere to us on Twitter and LinkedIn to go through extra exceptional written content we post.
Some parts of this article are sourced from:
thehackernews.com


 Tech Giant HP Enterprise Hacked by Russian Hackers Linked to DNC Breach
Tech Giant HP Enterprise Hacked by Russian Hackers Linked to DNC Breach