Cybersecurity scientists have uncovered destructive Android apps for Signal and Telegram distributed via the Google Play Retailer and Samsung Galaxy Store that are engineered to produce the BadBazaar spyware on contaminated units.
Slovakian organization ESET attributed the marketing campaign to a China-linked actor referred to as GREF.
“Most very likely energetic due to the fact July 2020 and considering that July 2022, respectively, the campaigns have distributed the Android BadBazaar espionage code by means of the Google Enjoy retail outlet, Samsung Galaxy Shop, and devoted sites representing the destructive applications Sign As well as Messenger and FlyGram,” security researcher Lukáš Štefanko stated in a new report shared with The Hacker Information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Victims have been mostly detected in Germany, Poland, and the U.S., followed by Ukraine, Australia, Brazil, Denmark, Congo-Kinshasa, Hong Kong, Hungary, Lithuania, the Netherlands, Portugal, Singapore, Spain, and Yemen.
BadBazaar was first documented by Lookout in November 2022 as focusing on the Uyghur group in China with seemingly benign Android and iOS applications that, at the time installed, harvests a vast variety of details, such as get in touch with logs, SMS messages, areas, and other people.
The earlier campaign, energetic since at the very least 2018, is also noteworthy for the fact that the rogue Android apps have been under no circumstances revealed to the Enjoy Shop. Equally the apps have since been taken down from google’s application storefront, but they proceed to be readily available on the Samsung Galaxy Shop.

The aspects of the apps are as follows –
- Signal Additionally Messenger (org.thoughtcrime.securesmsplus) – 100+ downloads considering that July 2022, also readily available via signalplus[.]org
- FlyGram (org.telegram.FlyGram) – 5,000+ downloads due to the fact June 2020, also out there by means of flygram[.]org
Over and above these distribution mechanisms, it can be explained that potential victims have also been probably tricked into setting up the applications from a Uyghur Telegram group concentrated on sharing Android apps. The team has above 1,300 members.
The two Signal As well as Messenger and FlyGram are built to accumulate and exfiltrate sensitive consumer info, with every single app focused to also amassing facts from the respective apps they mimic: Sign and Telegram.
This includes the ability to accessibility Sign PIN and Telegram chat backups ought to the target enable a Cloud Sync characteristic from the trojanized app.
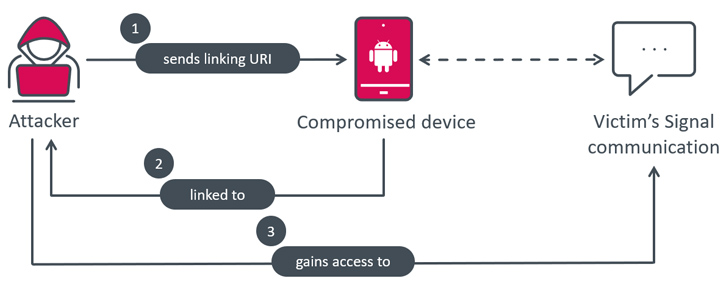
In what’s a novel twist, Signal Plus Messenger signifies the initial documented scenario of surveillance of a victim’s Signal communications by covertly linking the compromised machine to the attacker’s Sign account without the need of demanding any person conversation.
“BadBazaar, the malware liable for the spying, bypasses the typical QR code scan and user simply click process by obtaining the needed URI from its [command-and-control] server, and specifically triggering the important action when the Backlink device button is clicked,” Štefanko discussed.

“This enables the malware to secretly website link the victim’s smartphone to the attacker’s system, enabling them to spy on Sign communications with no the victim’s know-how.”
FlyGram, for its portion, also implements a function identified as SSL pinning to evade analysis by embedding the certification within just the APK file such that only encrypted communication with the predefined certificate is allowed, thus creating it tough to intercept and examine the network traffic involving the app and its server.
An assessment of the app Cloud Sync aspect has more disclosed that each individual person who registers for the assistance is assigned a distinctive ID that is sequentially incremented. It really is estimated that 13,953 end users (which includes ESET) put in FlyGram and activated the Cloud Sync element.
ESET stated it is continuing to observe GREF as a independent cluster regardless of prior open up-source reporting connecting the group to APT15, citing deficiency of definitive evidence.
“BadBazaar’s principal purpose is to exfiltrate device data, the make contact with list, phone logs, and the record of mounted applications, and to perform espionage on Sign messages by secretly linking the victim’s Sign Additionally Messenger app to the attacker’s gadget,” Štefanko said.
Found this posting fascinating? Follow us on Twitter and LinkedIn to read more exclusive articles we article.
Some sections of this report are sourced from:
thehackernews.com


 How to Prevent ChatGPT From Stealing Your Content & Traffic
How to Prevent ChatGPT From Stealing Your Content & Traffic