A earlier undocumented Android banking trojan dubbed MMRat has been noticed concentrating on cell users in Southeast Asia because late June 2023 to remotely commandeer the products and carry out money fraud.
“The malware, named after its distinctive bundle name com.mm.person, can seize consumer enter and display screen information, and can also remotely handle sufferer devices by a variety of approaches, enabling its operators to have out lender fraud on the victim’s gadget,” Craze Micro mentioned.
What tends to make MMRat stand aside from other folks of its variety is the use of a personalized command-and-handle (C2) protocol dependent on protocol buffers (aka protobuf) to effectively transfer big volumes of data from compromised handsets, demonstrating the growing sophistication of Android malware.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Doable targets based on the language utilized in the phishing pages include Indonesia, Vietnam, Singapore, and the Philippines.

The entry issue of the attacks is a network of phishing websites that mimic formal application suppliers, although how victims are directed to these one-way links is presently not known. MMRat usually masquerades as an official federal government or a courting app.
The moment installed, the application leans seriously on Android accessibility service and MediaProjection API, the two of which have been leveraged by yet another Android economical trojan identified as SpyNote, to have out its actions. The malware is also able of abusing its accessibility permissions to grant alone other permissions and modify configurations.
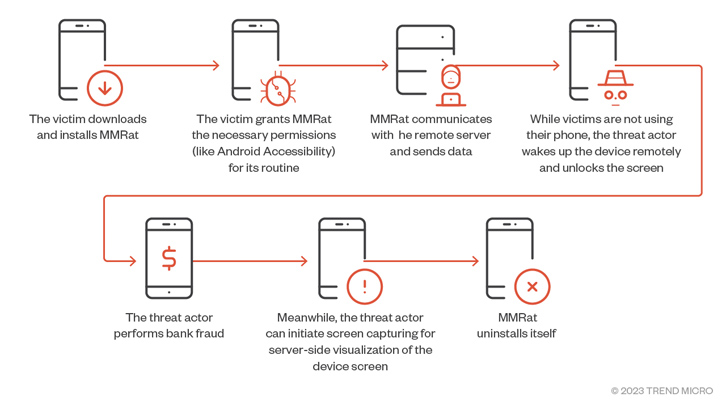
It further more sets up persistence to endure concerning reboots and initiates communications with a remote server to await guidance and exfiltrate the results of the execution of people instructions back to it. The trojan employs various combinations of ports and protocols for functions this kind of as facts exfiltration, online video streaming, and C2 command.
MMRat possesses the means to acquire a broad variety of system knowledge and particular facts, including signal energy, monitor position, and battery stats, put in apps, and contact lists. It is really suspected that the danger actor employs the particulars to have out some kind of victim profiling ahead of transferring to the next stage.
Some of the other capabilities of MMRat encompass recording serious-time monitor written content and capturing the lock display sample so as to enable the threat actor to remotely get entry to the victim’s gadget when it is locked and not actively in use.

“The MMRat malware abuses the Accessibility company to remotely regulate the victim’s product, carrying out actions this sort of as gestures, unlocking screens, and inputting textual content, amid many others,” Pattern Micro mentioned.
“This can be utilised by danger actors — in conjunction with stolen qualifications — to conduct lender fraud.”
The attacks conclusion with MMRat deleting by itself upon receiving the C2 command UNINSTALL_Application, which generally requires position just after a productive fraudulent transaction, successfully eradicating all traces of infection from the device.
To mitigate threats posed by these kinds of potent malware, it can be recommended that customers only download applications from formal sources, scrutinize app evaluations, and verify the permissions an application requests for obtain to just before usage.
Discovered this posting fascinating? Follow us on Twitter and LinkedIn to read through more special articles we publish.
Some parts of this report are sourced from:
thehackernews.com


 China-Linked BadBazaar Android Spyware Targeting Signal and Telegram Users
China-Linked BadBazaar Android Spyware Targeting Signal and Telegram Users