New conclusions show that destructive actors could leverage a sneaky malware detection evasion strategy and bypass endpoint security answers by manipulating the Windows Container Isolation Framework.
The results were presented by Deep Intuition security researcher Daniel Avinoam at the DEF CON security conference held previously this thirty day period.
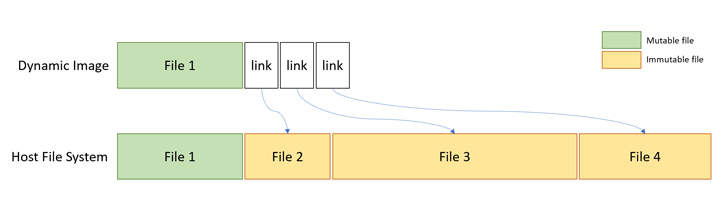
Microsoft’s container architecture (and by extension, Windows Sandbox) uses what is known as a dynamically produced picture to independent the file process from each container to the host and at the exact time steer clear of duplication of system documents.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
It can be practically nothing but an “functioning process picture that has cleanse copies of data files that can adjust, but links to information that simply cannot improve that are in the Windows picture that by now exists on the host,” thus bringing down the overall size for a complete OS.

“The consequence is images that incorporate ‘ghost files,’ which keep no true details but point to a various quantity on the technique,” Avinoam claimed in a report shared with The Hacker News. “It was at this point that the plan struck me — what if we can use this redirection system to obfuscate our file method functions and confuse security products and solutions?”
This is where by the Windows Container Isolation FS (wcifs.sys) minifilter driver comes into participate in. The driver’s main intent is to just take care of the file process separation amongst Windows containers and their host.
In other phrases, the thought is to have the latest approach managing inside a fabricated container and leverage the minifilter driver to manage I/O requests these types of that it can generate, go through, publish, and delete documents on the file process without the need of alerting security software package.
 Source: Microsoft
Source: Microsoft
It’s really worth pointing out at this stage that a minifilter attaches to the file procedure stack indirectly, by registering with the filter manager for the I/O functions that it chooses to filter. Every single minifilter is allotted a Microsoft-assigned “integer” altitude worth based on filter demands and load get team.
The wcifs driver has an altitude array of 180000-189999 (especially 189900), when antivirus filters, which include individuals from third-events, function at an altitude assortment of 320000-329999. As a consequence, different file functions can be done with out receiving their callbacks triggered.

“For the reason that we can override information employing the IO_REPARSE_TAG_WCI_1 reparse tag without the need of the detection of antivirus drivers, their detection algorithm will not obtain the entire photo and therefore will not bring about,” Avinoam described.
That having said, pulling off the attack involves administrative permissions to converse with the wcifs driver and it cannot be made use of to override documents on the host procedure.
The disclosure arrives as the cybersecurity enterprise demonstrated a stealthy procedure known as NoFilter that abuses the Windows Filtering Platform (WFP) to elevate a user’s privileges to that of System and perhaps execute malicious code.
The attacks allow for the use of WFP to duplicate obtain tokens for an additional system, induce an IPSec link and leverage the Print Spooler assistance to insert a Procedure token into the table, and make it feasible to get hold of the token of another user logged into the compromised method for lateral motion.
Found this report interesting? Comply with us on Twitter and LinkedIn to examine more unique content material we put up.
Some components of this posting are sourced from:
thehackernews.com


 MMRat Android Trojan Executes Remote Financial Fraud Through Accessibility Feature
MMRat Android Trojan Executes Remote Financial Fraud Through Accessibility Feature