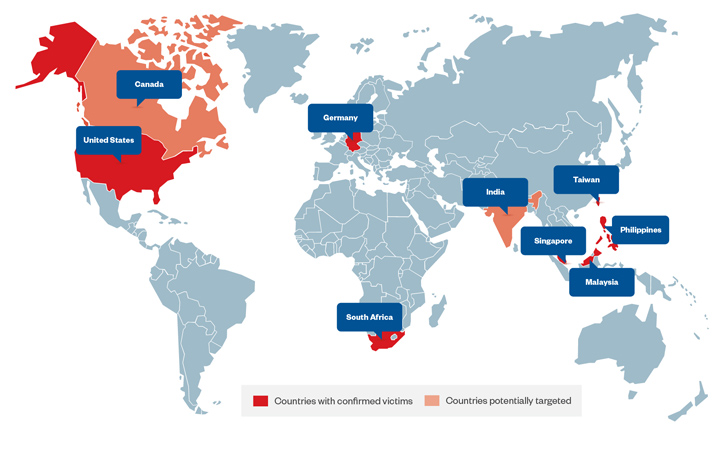
A hacking outfit nicknamed Earth Estries has been attributed to a new, ongoing cyber espionage campaign concentrating on federal government and technology industries centered in the Philippines, Taiwan, Malaysia, South Africa, Germany, and the U.S.
“The risk actors guiding Earth Estries are functioning with significant-amount methods and performing with sophisticated expertise and working experience in cyber espionage and illicit pursuits,” Development Micro researchers Ted Lee, Lenart Bermejo, Hara Hiroaki, Leon M Chang, and Gilbert Sison said.
Active considering the fact that at minimum 2020, Earth Estries is mentioned to share tactical overlaps with a further nation-state team tracked as FamousSparrow, which was very first exposed by ESET in 2021 as exploiting ProxyLogon flaws in Microsoft Trade Server to penetrate hospitality, authorities, engineering, and legal sectors.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

It really is worth pointing out that commonalities have also been unearthed concerning FamousSparrow and UNC4841, a categorized action cluster held liable for the weaponization of a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway (ESG) appliances.
Attack chains documented by Development Micro display that the adversary is leveraging Cobalt Strike to carry out put up-exploitation of compromised environments, adhering to which it moves immediately to deploy supplemental malware and broaden the foothold.
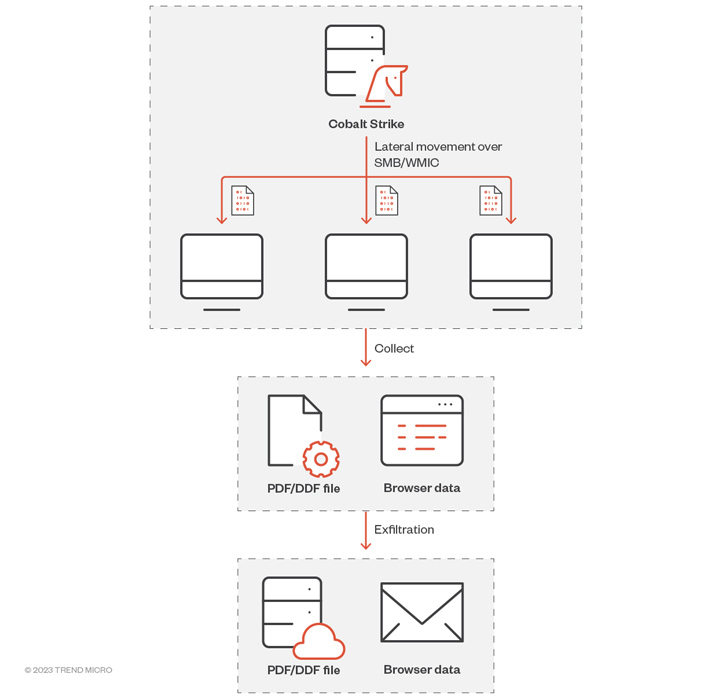
The adversary has been observed employing an arsenal of backdoors and hacking instruments, which includes backdoors, browser information stealers, and port scanners to increase info assortment.
This encompasses Zingdoor, a Go-dependent implant to capture system information, enumerate and deal with data files, and operate arbitrary commands TrillClient, a custom made stealer prepared in Go to siphon details from web browsers and HemiGate, a backdoor that can log keystrokes, consider screenshots, conduct file functions, and watch procedures.

Additional lending legitimacy to the adversary’s espionage motives is its proclivity toward frequently cleaning and redeploying its backdoors on the contaminated host in an try to lessen the risk of publicity and detection.
“Earth Estries relies seriously on DLL aspect-loading to load numerous instruments in just its arsenal,” the researchers reported. “To depart as small footprint as attainable, they use PowerShell downgrade attacks to prevent detection from Windows Antimalware Scan Interface’s (AMSI) logging mechanism.”
Yet another sizeable factor of the modus operandi is the abuse of public products and services these kinds of as Github, Gmail, AnonFiles, and File.io to trade or transfer commands and stolen info. A bulk of the command-and-handle (C2) servers are situated in the U.S., India, Australia, Canada, China, Japan, Finland, South Africa, and the U.K.
“By compromising inside servers and legitimate accounts, the danger actors can perform lateral movement inside of the victim’s network and have out their destructive activities covertly,” the researchers said. “They also use strategies like PowerShell downgrade attacks and novel DLL side-loading combos to evade detection.”
Discovered this post attention-grabbing? Comply with us on Twitter and LinkedIn to read through additional special information we post.
Some sections of this write-up are sourced from:
thehackernews.com

 Hackers Can Exploit Windows Container Isolation Framework to Bypass Endpoint Security
Hackers Can Exploit Windows Container Isolation Framework to Bypass Endpoint Security