A country-condition action group originating from China has been joined to cyber attacks on dozens of businesses in Taiwan as section of a suspected espionage marketing campaign.
The Microsoft Danger Intelligence team is monitoring the action under the identify Flax Storm, which is also acknowledged as Ethereal Panda.
“Flax Storm gains and maintains prolonged-time period entry to Taiwanese organizations’ networks with minimum use of malware, relying on equipment constructed into the running system, together with some commonly benign program to quietly stay in these networks,” the enterprise explained.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
It additional explained it has not noticed the team weaponize the accessibility to conduct data-collection and exfiltration. A vast majority of the targets include things like authorities organizations, educational establishments, critical production, and data technology companies in Taiwan.
A smaller quantity of victims have also been detected in Southeast Asia, North The us, and Africa. The group is suspected to have been active since mid-2021.

“Ethereal Panda functions mainly focus on entities in the academic, technology, and telecommunications sectors in Taiwan,” CrowdStrike notes in its description of the hacker crew. “Ethereal Panda depends greatly on SoftEther VPN executables to keep access to target networks, but has also been noticed deploying the GodZilla web shell.”
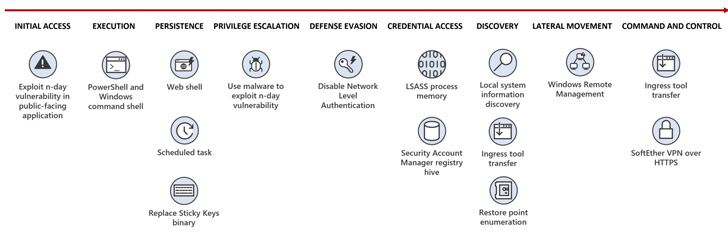
The main concentrate of the actor revolves about persistence, lateral motion, and credential obtain, with the actor employing living-off-the-land (LotL) methods and fingers-on keyboard action to recognize its plans.
The modus operandi is in line with danger actors’ observe of frequently updating their techniques to evade detection, banking on out there applications in the focus on ecosystem to avoid pointless download and creation of custom made parts.
Original obtain is facilitated by suggests of exploiting known vulnerabilities in general public-struggling with servers and deploying web shells like China Chopper, followed by establishing persistent access over Distant Desktop Protocol (RDP), deploy a VPN bridge to connect to a remote server, and harvest credentials utilizing Mimikatz.

A noteworthy aspect of the attacks is the modification of the Sticky Keys conduct to start Job Manager, enabling Flax Typhoon to conduct article-exploitation on the compromised program.
“In conditions exactly where Flax Storm requires to go laterally to entry other techniques on the compromised network, the actor utilizes LOLBins, including Windows Distant Administration (WinRM) and WMIC,” the Windows maker stated.
The advancement will come 3 months after Microsoft exposed yet another China-linked actor named Volt Hurricane (aka Bronze Silhouette or Vanguard Panda), which has been observed exclusively relying on LotL procedures to fly less than the radar and exfiltrate info.
While crossover of techniques and infrastructure amid danger actors working out of China isn’t really abnormal, the conclusions paint the picture of a continuously evolving menace landscape, with adversaries shifting their tradecraft to become far more selective in their observe-on operations.
Discovered this write-up intriguing? Stick to us on Twitter and LinkedIn to examine additional special articles we write-up.
Some sections of this article are sourced from:
thehackernews.com


 Urgent FBI Warning: Barracuda Email Gateways Vulnerable Despite Recent Patches
Urgent FBI Warning: Barracuda Email Gateways Vulnerable Despite Recent Patches