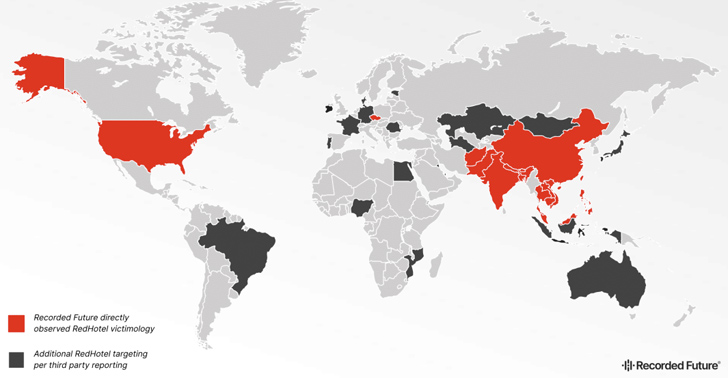
Hackers connected with China’s Ministry of Condition Security (MSS) have been connected to attacks in 17 distinct international locations in Asia, Europe, and North America from 2021 to 2023.
Cybersecurity agency Recorded Future attributed the intrusion established to a nation-condition team it tracks beneath the title RedHotel (formerly Danger Exercise Group-22 or TAG-222), which overlaps with a cluster of exercise broadly monitored as Aquatic Panda, Bronze University, Charcoal Hurricane, Earth Lusca, and Purple Scylla (or Crimson Dev 10).
Energetic because 2019, some of the popular sectors focused by the prolific actor encompass academia, aerospace, govt, media, telecommunications, and investigate. A the vast majority of the victims for the duration of the time period had been federal government organizations.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“RedHotel has a dual mission of intelligence gathering and financial espionage,” the cybersecurity business said, contacting out its persistence, operational depth, and international access. “It targets both of those govt entities for conventional intelligence and companies concerned in COVID-19 analysis and technology R&D.”

Development Micro, in early January 2022, described the adversary as a “extremely-expert and hazardous menace actor mostly inspired by cyberespionage and economical obtain.”
The team has given that been linked to exploitation of Log4Shell flaws as well as attacks aimed at telecommunications, academia, study and growth, and authorities companies in Nepal, the Philippines, Taiwan, and Hong Kong to deploy backdoors for extended-term accessibility.
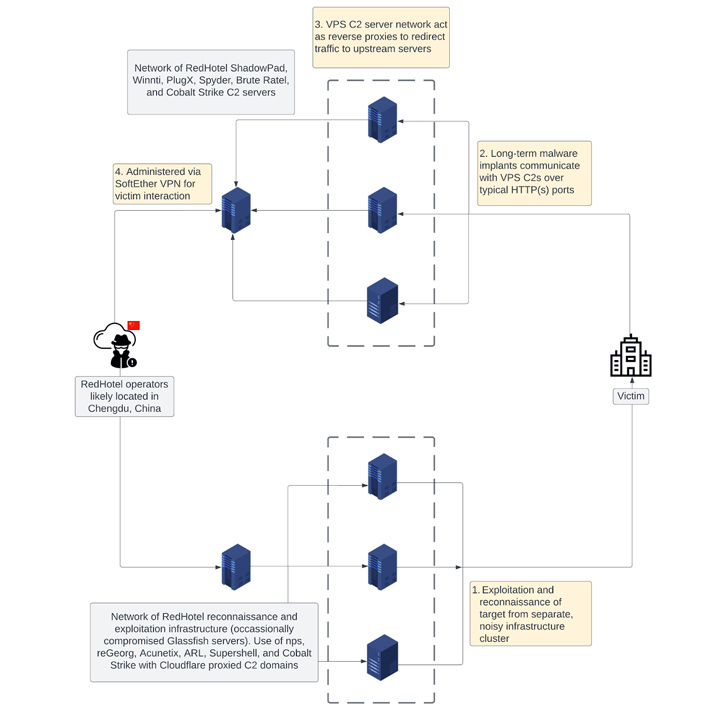
Attack chains mounted by RedHotel have weaponized public-dealing with purposes for first obtain, adopted by utilizing a blend of offensive security applications like Cobalt Strike and Brute Ratel C4 (BRc4) and bespoke malware people these types of as FunnySwitch, ShadowPad, Spyder, and Winnti.
A noteworthy part of the actor’s modus operandi is the use of a multi-tiered infrastructure, each individual concentrating on original reconnaissance and long-term network entry by using command-and-manage servers. It predominantly makes use of NameCheap for area registration.

In a single late 2022 marketing campaign, RedHotel is explained to have leveraged a stolen code signing certification belonging to a Taiwanese gaming firm to indication a DLL file accountable for loading BRc4. The post-exploitation toolkit, for its section, is configured to talk with abused compromised Vietnamese government infrastructure.
“RedHotel has exemplified a relentless scope and scale of wider PRC point out-sponsored cyber-espionage exercise by maintaining a higher operational tempo and focusing on general public and private sector corporations globally,” Recorded Potential explained.
The progress comes as the Washington Write-up noted that Chinese hackers experienced “deep, persistent entry” to labeled protection networks in Japan, prompting the U.S. Countrywide Security Company (NSA), which found out the breach in late 2020, to individually report the make a difference to governing administration officials.
Uncovered this write-up appealing? Observe us on Twitter and LinkedIn to browse more unique articles we article.
Some elements of this report are sourced from:
thehackernews.com

 Continuous Security Validation with Penetration Testing as a Service (PTaaS)
Continuous Security Validation with Penetration Testing as a Service (PTaaS)