The lately uncovered cyber espionage marketing campaign concentrating on perimeter network units from a number of vendors, together with Cisco, may possibly have been the work of China-joined actors, in accordance to new conclusions from attack surface area management company Censys.
Dubbed ArcaneDoor, the exercise is reported to have commenced all over July 2023, with the initial confirmed attack in opposition to an unnamed sufferer detected in early January 2024.
The qualified attacks, orchestrated by a beforehand undocumented suspected refined point out-sponsored actor tracked as UAT4356 (aka Storm-1849), entailed the deployment of two personalized malware dubbed Line Runner and Line Dancer.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The original accessibility pathway employed to facilitate the intrusions has still to be found, though the adversary has been noticed leveraging two now-patched flaws in Cisco Adaptive Security Appliances (CVE-2024-20353 and CVE-2024-20359) to persist Line Runner.
Telemetry information collected as component of the investigation has unveiled the danger actor’s curiosity in Microsoft Exchange servers and network devices from other vendors, Talos claimed final thirty day period.

Censys, which further more examined the actor-managed IP addresses, stated the attacks level to the potential involvement of a danger actor primarily based in China.
This is centered on the truth that 4 of the five on the internet hosts presenting the SSL certification determined as affiliated with the attackers’ infrastructure are associated with Tencent and ChinaNet autonomous devices (AS).
In addition, amongst the danger actor-managed IP addresses is a Paris-centered host (212.193.2[.]48) with the topic and issuer established as “Gozargah,” which is most likely a reference to a GitHub account that hosts an anti-censorship device named Marzban.
The program, in turn, is “driven” by a further open up-resource undertaking dubbed Xray that has a web site penned in Chinese.
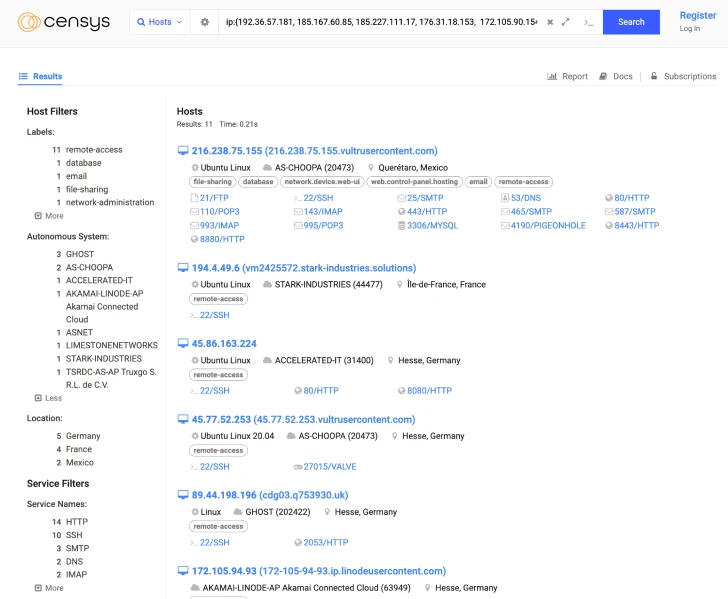
This indicates that “some of these hosts have been jogging expert services affiliated with anti-censorship program probably intended to circumvent The Fantastic Firewall,” and that “a sizeable variety of these hosts are based mostly in outstanding Chinese networks,” suggesting that ArcaneDoor could be the work of a Chinese actor, Censys theorized.
Nation-state actors affiliated with China have increasingly qualified edge appliances in the latest a long time, leveraging zero-working day flaws in Barracuda Networks, Fortinet, Ivanti, and VMware to infiltrate targets of fascination and deploy malware for persistent covert obtain.

The advancement comes as French cybersecurity agency Sekoia explained it successfully sinkholed a command-and-handle (C2) server connected to the PlugX trojan in September 2023 by paying out $7 to receive the IP deal with tied to a variant of the malware with abilities to propagate in a worm-like trend by way of compromised flash drives.
A nearer monitoring of the sinkholed IP handle (45.142.166[.]112) has exposed the worm’s presence in additional than 170 nations around the world spanning 2.49 million one of a kind IP addresses more than a 6-month interval. A the greater part of the bacterial infections have been detected in Nigeria, India, China, Iran, Indonesia, the U.K., Iraq, the U.S., Pakistan, and Ethiopia.
“Lots of nations, excluding India, are contributors in China’s Belt and Road Initiative and have, for most of them, coastlines where by Chinese infrastructure investments are substantial,” Sekoia reported. “A lot of impacted nations around the world are situated in regions of strategic importance for the security of the Belt and Road Initiative.”
“This worm was produced to collect intelligence in various international locations about the strategic and security issues related with the Belt and Road Initiative, typically on its maritime and financial factors.”
Uncovered this article intriguing? Abide by us on Twitter and LinkedIn to study a lot more distinctive content material we article.
Some areas of this article are sourced from:
thehackernews.com


 It Costs How Much?!? The Financial Pitfalls of Cyberattacks on SMBs
It Costs How Much?!? The Financial Pitfalls of Cyberattacks on SMBs