Much more than 50% of the 90,310 hosts have been uncovered exposing a Tinyproxy service on the internet that’s susceptible to a critical unpatched security flaw in the HTTP/HTTPS proxy instrument.
The issue, tracked as CVE-2023-49606, carries a CVSS score of 9.8 out of a maximum of 10, for every Cisco Talos, which explained it as a use-after-no cost bug impacting versions 1.10. and 1.11.1, which is the hottest version.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“A specifically crafted HTTP header can result in reuse of beforehand freed memory, which leads to memory corruption and could lead to distant code execution,” Talos reported in an advisory past 7 days. “An attacker demands to make an unauthenticated HTTP ask for to result in this vulnerability.”

In other phrases, an unauthenticated danger actor could deliver a specifically crafted HTTP Relationship header to induce memory corruption that can consequence in distant code execution.
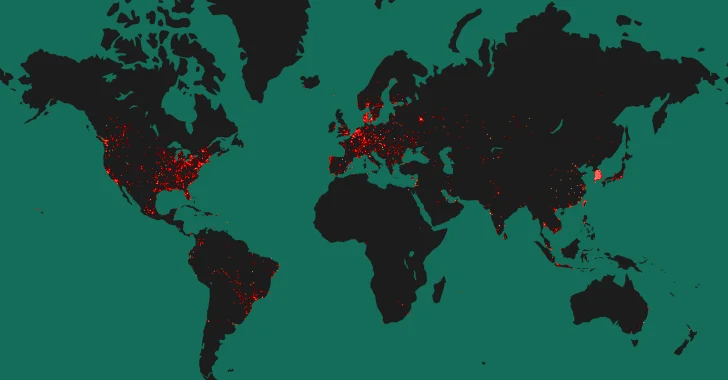
In accordance to info shared by attack surface area management business Censys, of the 90,310 hosts exposing a Tinyproxy support to the general public internet as of May possibly 3, 2024, 52,000 (~57%) of them are managing a vulnerable variation of Tinyproxy.
A vast majority of the publicly-available hosts are situated in the U.S. (32,846), South Korea (18,358), China (7,808), France (5,208), and Germany (3,680).
Talos, which noted the issue to December 22, 2023, has also unveiled a proof-of-concept (PoC) for the flaw, describing how the issue with parsing HTTP Relationship connections could be weaponized to set off a crash and, in some cases, code execution.
The maintainers of Tinyproxy, in a established of commits created over the weekend, named out Talos for sending the report to a possible “out-of-date email tackle,” introducing they had been designed aware by a Debian Tinyproxy package deal maintainer on Might 5, 2024.

“No GitHub issue was filed, and no person talked about a vulnerability on the talked about IRC chat,” rofl0r explained in a dedicate. “If the issue had been described on Github or IRC, the bug would have been preset within a working day.”
End users are suggested to update to the newest variation as and when they come to be obtainable. It truly is also encouraged that the Tinyproxy provider is not uncovered to the public internet.
Discovered this article appealing? Stick to us on Twitter and LinkedIn to read additional exceptional written content we post.
Some sections of this article are sourced from:
thehackernews.com

 China-Linked Hackers Suspected in ArcaneDoor Cyberattacks Targeting Network Devices
China-Linked Hackers Suspected in ArcaneDoor Cyberattacks Targeting Network Devices