Risk action clusters affiliated with the Chinese and Russian cybercriminal ecosystems have been observed using a new piece of malware that is made to load Cobalt Strike onto contaminated equipment.
Dubbed SILKLOADER by Finnish cybersecurity corporation WithSecure, the malware leverages DLL aspect-loading procedures to supply industrial adversary simulation application.
The progress will come as enhanced detection abilities in opposition to Cobalt Strike, a legitimate post-exploitation software employed for pink workforce functions, is forcing danger actors to look for alternative solutions or concoct new ways to propagate the framework to evade detection.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The most common of these involve incorporating complexity to the auto-generated beacon or stager payloads through the utilization of packers, crypters, loaders, or very similar strategies,” WithSecure scientists claimed.
SILKLOADER joins other loaders these kinds of as KoboldLoader, MagnetLoader, and LithiumLoader that have been a short while ago learned incorporating Cobalt Strike factors.
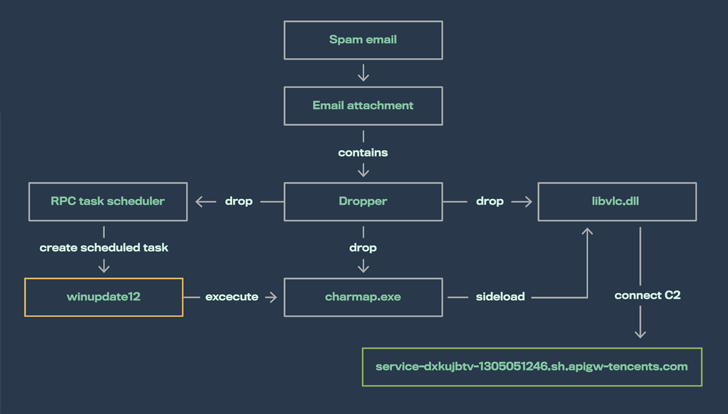
It also shares overlaps with LithiumLoader in that both equally employ the DLL side-loading process to hijack a legitimate software with the objective of functioning a separate, malicious dynamic hyperlink library (DLL).
SILKLOADER achieves this by using specially crafted libvlc.dll data files that are dropped along with a respectable but renamed VLC media participant binary (Charmap.exe).
WithSecure reported it recognized the shellcode loader adhering to an evaluation of “various human-operated intrusions” targeting various entities spanning a wide selection of organizations situated in Brazil, France, and Taiwan in Q4 2022.
Despite the fact that these attacks were being unsuccessful, the activity is suspected to be a direct-up to ransomware deployments, with the practices and tooling “heavily overlapping” with these attributed to the operators of the Enjoy ransomware.
In one particular attack aimed at an unnamed French social welfare business, the menace actor received a foothold into the network by exploiting a compromised Fortinet SSL VPN equipment to phase Cobalt Strike beacons.
“The risk actor maintained a foothold in this business for a number of months,” WithSecure stated. “Throughout this time, they executed discovery and credential stealing routines, adopted by deployment of many Cobalt Strike beacons.”
But when this endeavor unsuccessful, the adversary switched to utilizing SILKLOADER to bypass detection and produce the beacon payload.
Which is not all. A further loader recognized as BAILLOADER, which is also used to distribute Cobalt Strike beacons, has been joined to attacks involving Quantum ransomware, GootLoader, and the IcedID trojan in new months.
BAILLOADER, for its part, is reported to show similarities with a crypter codenamed Tron that has been place to use by diverse adversaries to distribute Emotet, TrickBot, BazarLoader, IcedID, Conti ransomware, and Cobalt Strike.
This has presented rise to the risk that disparate menace actors share Cobalt Strike beacons, crypters, and infrastructure provided by 3rd-party affiliates to company a number of intrusions making use of different ways.
In other text, SILKLOADER is very likely being made available as an off-the-shelf loader by way of a Packer-as-a-Provider system to Russian-dependent menace actors.
“This loader is currently being delivered both right to ransomware groups or potentially by means of teams presenting Cobalt Strike/Infrastructure-as-a-Service to dependable affiliate marketers,” WithSecure said.
WEBINARDiscover the Hidden Hazards of Third-Party SaaS Apps
Are you informed of the threats connected with 3rd-party application obtain to your firm’s SaaS applications? Join our webinar to understand about the types of permissions staying granted and how to reduce risk.
RESERVE YOUR SEAT
“Most of these affiliates surface to have been element of or have experienced shut operating interactions with the Conti group, its associates, and offspring just after its alleged shutdown.”
SILKLOADER samples analyzed by the business demonstrate that early variations of the malware date back to the begin of 2022, with the loader exclusively set to use in distinct attacks targeting victims in China and Hong Kong.
The change from East Asian targets to other international locations this sort of as Brazil and France is believed to have occurred close to July 2022, just after which all SILKLOADER-associated incidents have been attributed to Russian cybercriminal actors.
This has further supplied way to a speculation that “SILKLOADER was at first written by risk actors acting inside the Chinese cybercriminal ecosystem” and that the “loader was applied by the threat actors within this nexus at the very least as early as May possibly 2022 till July 2022.”
“The builder or resource code was later acquired by a risk actor in just the Russian cybercriminal ecosystem in between July 2022 and September 2022,” WithSecure said, incorporating, “the authentic Chinese writer offered the loader to a Russian threat actor once they no lengthier experienced any use for it.”
Both SILKLOADER and BAILLOADER are just the most up-to-date illustrations of threat actors refining and retooling their techniques to keep ahead of the detection curve.
“As the cybercriminal ecosystem gets to be far more and much more modularized by way of services choices, it is no longer feasible to attribute attacks to risk teams only by
linking them to precise elements within just their attacks,” WithSecure scientists concluded.
Identified this post exciting? Stick to us on Twitter and LinkedIn to examine a lot more distinctive material we write-up.
Some parts of this report are sourced from:
thehackernews.com

 Cryptojacking Group TeamTNT Suspected of Using Decoy Miner to Conceal Data Exfiltration
Cryptojacking Group TeamTNT Suspected of Using Decoy Miner to Conceal Data Exfiltration