The cryptojacking group regarded as TeamTNT is suspected to be guiding a beforehand undiscovered strain of malware applied to mine Monero cryptocurrency on compromised devices.
That’s according to Cado Security, which identified the sample right after Sysdig specific a refined attack regarded as SCARLETEEL aimed at containerized environments to eventually steal proprietary details and program.
Particularly, the early period of the attack chain included the use of a cryptocurrency miner, which the cloud security business suspected was deployed as a decoy to conceal the detection of data exfiltration.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The artifact – uploaded to VirusTotal late very last month – “bear[s] numerous syntactic and semantic similarities to prior TeamTNT payloads, and incorporates a wallet ID that has previously been attributed to them,” a new examination from Cado Security has discovered.
TeamTNT, active considering that at minimum 2019, has been documented to regularly strike cloud and container environments to deploy cryptocurrency miners. It truly is also known to unleash a crypto mining worm able of stealing AWS qualifications.
While the danger actor willingly shut down their functions in November 2021, cloud security firm Aqua disclosed in September 2022 a refreshing established of attacks mounted by the team targeting misconfigured Docker and Redis situations.
That reported, there are also indications that rival crews these as WatchDog could be mimicking TeamTNT’s practices, tactics, and processes (TTPs) to foil attribution attempts.
One more exercise cluster of take note is Kiss-a-pet dog, which also relies on resources and command-and-command (C2) infrastructure beforehand related with TeamTNT to mine cryptocurrency.
There is no concrete proof to tie the new malware to the SCARLETEEL attack. But Cado Security pointed out that the sample surfaced about the exact time the latter was claimed, raising the likelihood that this could be the “decoy” miner that was mounted.
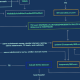
The shell script, for its element, normally takes preparatory methods to reconfigure resource tricky limitations, avert command heritage logging, accept all ingress or egress website traffic, enumerate hardware methods, and even clean up prior compromises in advance of commencing the action.
Like other TeamTNT-joined attacks, the destructive payload also leverages a strategy referred to as dynamic linker hijacking to cloak the miner system through a shared object executable termed libprocesshider that makes use of the LD_PRELOAD environment variable.
Persistence is accomplished by three distinct indicates, 1 of which modifies the .profile file, to make sure that the miner continues to run across process reboots.
WEBINARDiscover the Concealed Risks of Third-Party SaaS Applications
Are you aware of the challenges involved with 3rd-party application obtain to your company’s SaaS apps? Be a part of our webinar to master about the sorts of permissions becoming granted and how to limit risk.
RESERVE YOUR SEAT
The conclusions come as an additional crypto miner team dubbed the 8220 Gang has been observed using a crypter named ScrubCrypt to carry out illicit cryptojacking operations.
What is actually a lot more, mysterious menace actors have been found concentrating on vulnerable Kubernetes container orchestrator infrastructure with uncovered APIs to mine the Dero cryptocurrency, marking a shift from Monero.
Cybersecurity corporation Morphisec, last thirty day period, also get rid of light-weight on an evasive malware campaign that leverages the ProxyShell vulnerabilities in Microsoft Exchange servers to drop a crypto miner pressure codenamed ProxyShellMiner.
“Mining cryptocurrency on an organization’s network can direct to process general performance degradation, enhanced electricity use, equipment overheating, and can cease providers,” the scientists explained. “It lets danger actors entry for even much more nefarious finishes.”
Located this post interesting? Follow us on Twitter and LinkedIn to go through more distinctive content material we submit.
Some areas of this article are sourced from:
thehackernews.com

 NCSC Calms Fears Over ChatGPT Threat
NCSC Calms Fears Over ChatGPT Threat