Cybersecurity scientists have unearthed a novel rootkit signed by Microsoft which is engineered to connect with an actor-managed attack infrastructure.
Development Micro has attributed the activity cluster to the same actor that was previously recognized as powering the FiveSys rootkit, which arrived to light in October 2021.
“This malicious actor originates from China and their principal victims are the gaming sector in China,” Trend Micro’s Mahmoud Zohdy, Sherif Magdy, and Mohamed Fahmy explained. Their malware would seem to have passed as a result of the Windows Hardware Quality Labs (WHQL) method for getting a legitimate signature.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Several variants of the rootkit spanning eight distinct clusters have been identified, with 75 these kinds of motorists signed employing Microsoft’s WHQL program in 2022 and 2023.
Development Micro’s investigation of some of the samples has disclosed the presence of debug messages in the resource code, indicating that the operation is still in the growth and screening stage.
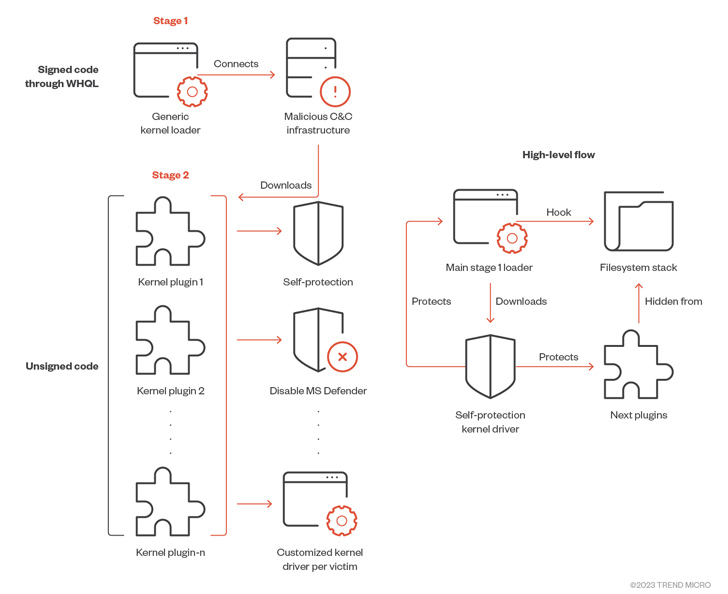
In subsequent actions, the to start with-stage driver disables the Person Account Management (UAC) and Secure Desktop mode by enhancing the registry and initializes Winsock Kernel (WSK) objects for initiating network conversation with the remote server.
It even further periodically polls the server to retrieve additional payloads and load them immediately into memory right after decoding and decrypting the obtained info, successfully operating as a stealthy kernel driver loader that can bypass detections.
“The principal binary functions as a common loader that makes it possible for the attackers to immediately load a next-phase unsigned kernel module,” the scientists explained. “Each and every 2nd-phase plug-in is personalized to the victim machine it can be deployed on, with some that contains even a personalized compiled driver for every device. Each individual plug-in has a certain set of actions to be carried out from the kernel house.”
The plug-ins, for their aspect, come with various abilities to obtain persistence, disarm Microsoft Defender Antivirus, and deploy a proxy on the equipment and redirect web browsing traffic to a remote proxy server.
Substantially like FiveSys, the new rootkit detections have been confined exclusively to China. One particular of the suspected entry details for these infections is explained to be a trojanized Chinese activity, mirroring Cisco Talos’ discovery of a malicious driver known as RedDriver.
The findings dovetail with other experiences from Cisco Talos and Sophos about the use of Microsoft-signed malicious kernel-manner motorists for put up-exploitation routines, with Chinese-speaking threat actors employing open up-supply application preferred in the online video video game cheat enhancement group to bypass restrictions enforced by the tech large.
Future WEBINARShield In opposition to Insider Threats: Master SaaS Security Posture Management
Apprehensive about insider threats? We’ve acquired you protected! Sign up for this webinar to discover practical methods and the tricks of proactive security with SaaS Security Posture Management.
Sign up for Nowadays
As lots of as 133 destructive motorists signed with reputable electronic certificates have been uncovered, 81 of which are able of terminating antivirus solutions on victims’ techniques. The remaining motorists are rootkits designed to covertly monitor delicate knowledge sent about the internet.
The point that these motorists are signed by the Windows Components Compatibility Application (WHCP) indicates that attackers can put in them on breached units with no raising any alerts and move forward to carry out destructive action just about unimpeded.
“For the reason that drivers usually converse with the ‘core’ of the working procedure and load before security program, when they are abused, they can be specially effective at disabling security protections – particularly when signed by a dependable authority,” Christopher Budd, director of danger exploration at Sophos X-Ops, stated.
Microsoft, in response to the disclosures, claimed it has implemented blocking protections and suspended the partners’ seller accounts included in the incident to safeguard customers from potential threats.
If everything, the enhancement paints a image of an evolving attack vector which is staying actively used by adversaries to get hold of privileged accessibility to Windows devices and sidetep detection by security program.
“Destructive actors will keep on to use rootkits to cover malicious code from security tools, impair defenses, and fly under the radar for extensive periods of time,” the scientists stated. “These rootkits will see hefty use from advanced groups that have both of those the techniques to reverse-engineer very low-degree system components and the demanded means to build these applications.”
Found this write-up interesting? Comply with us on Twitter and LinkedIn to read much more special written content we article.
Some components of this write-up are sourced from:
thehackernews.com


 Python-Based PyLoose Fileless Attack Targets Cloud Workloads for Cryptocurrency Mining
Python-Based PyLoose Fileless Attack Targets Cloud Workloads for Cryptocurrency Mining