A new fileless attack dubbed PyLoose has been observed striking cloud workloads with the objective of delivering a cryptocurrency miner, new findings from Wiz expose.
“The attack is composed of Python code that hundreds an XMRig Miner directly into memory using memfd, a identified Linux fileless strategy,” security scientists Avigayil Mechtinger, Oren Ofer, and Itamar Gilad explained. “This is the initially publicly documented Python-primarily based fileless attack concentrating on cloud workloads in the wild.”
The cloud security agency said it identified practically 200 occasions where by the attack process was utilized for cryptocurrency mining. No other specifics about the risk actor are currently known other than the fact that they have sophisticated abilities.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
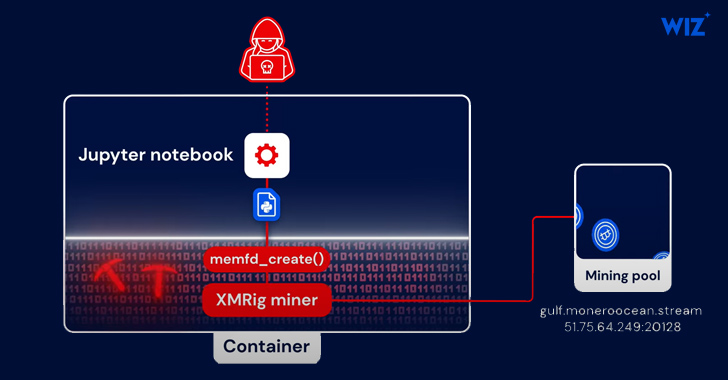
In the an infection chain documented by Wiz, initial access is realized by way of the exploitation of a publicly obtainable Jupyter Notebook company that allowed for the execution of technique instructions applying Python modules.
PyLoose, very first detected on June 22, 2023, is a Python script with just nine strains of code that embeds a compressed and encoded precompiled XMRig miner. The payload is retrieved from paste.c-net[.]org into the Python runtime’s memory by means of an HTTPS GET ask for with no possessing to create the file to disk.
The Python code is built to decode and decompress the XMRig miner and then load it specifically into memory by way of the memfd memory file descriptor, which is used to access memory-resident documents.
Future WEBINARShield Towards Insider Threats: Grasp SaaS Security Posture Administration
Worried about insider threats? We have received you coated! Be a part of this webinar to investigate sensible tactics and the strategies of proactive security with SaaS Security Posture Administration.
Be part of Now
“The attacker went to terrific lengths to be untraceable by utilizing an open up data-sharing services to host the Python payload, adapting the fileless execution system to Python, and compiling an XMRig miner to embed its config to avoid touching the disk or making use of a revealing command line,” the scientists stated.
The enhancement will come as Sysdig thorough a new attack marketing campaign mounted by a danger actor regarded as SCARLETEEL that involves the abuse of AWS infrastructure to steal proprietary information and carry out illicit crypto mining.
Located this posting intriguing? Follow us on Twitter and LinkedIn to browse far more special articles we submit.
Some components of this write-up are sourced from:
thehackernews.com

 Microsoft Releases Patches for 130 Vulnerabilities, Including 6 Under Active Attack
Microsoft Releases Patches for 130 Vulnerabilities, Including 6 Under Active Attack