A technically sophisticated danger actor regarded as SeaFlower has been targeting Android and iOS users as portion of an in depth campaign that mimics formal cryptocurrency wallet sites intending to distribute backdoored applications that drain victims’ resources.
Explained to be 1st identified in March 2022, the cluster of activity “trace[s] to a robust connection with a Chinese-speaking entity nevertheless to be uncovered,” dependent on the macOS usernames, supply code responses in the backdoor code, and its abuse of Alibaba’s Material Shipping and delivery Network (CDN).


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“As of these days, the key present-day objective of SeaFlower is to modify Web3 wallets with backdoor code that in the end exfiltrates the seed phrase,” Confiant’s Taha Karim mentioned in a technical deep-dive of the marketing campaign.
Targeted applications include Android and iOS versions of Coinbase Wallet, MetaMask, TokenPocket, and imToken.
SeaFlower’s modus operandi involves location up cloned internet sites that act as a conduit to obtain trojanized versions of the wallet apps that are nearly unchanged from their initial counterparts apart from for the addition of new code designed to exfiltrate the seed phrase to a remote domain.
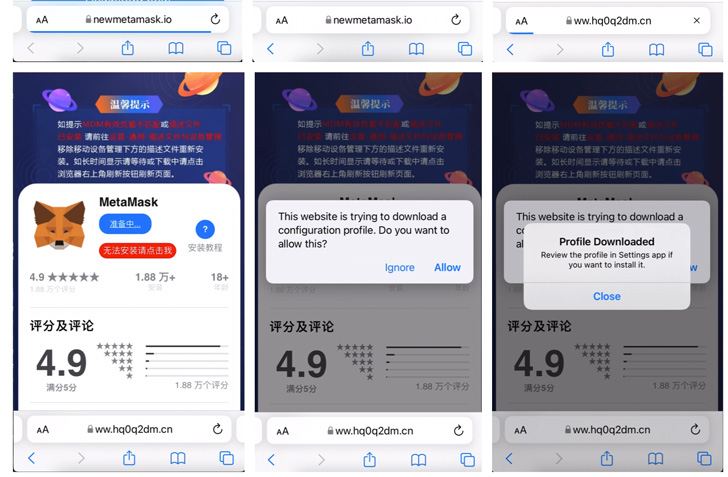
The malicious activity is also engineered to goal iOS consumers by implies of provisioning profiles that help the apps to be sideloaded on to the devices.

As for how users stumble on these websites offering fraudulent wallets, the attack leverages Seo poisoning strategies on Chinese look for engines like Baidu and Sogou so that lookups for conditions these types of as “download MetaMask iOS” are rigged to area the generate-by obtain internet pages on prime of the look for results web page.
If nearly anything, the disclosure at the time once again highlights how danger actors are ever more environment their sights on well-liked Web3 platforms in an try to plunder delicate facts and deceptively transfer virtual money.
Discovered this post intriguing? Stick to THN on Facebook, Twitter and LinkedIn to read much more unique information we post.
Some sections of this article are sourced from:
thehackernews.com

 Chinese ‘Gallium’ Hackers Using New PingPull Malware in Cyberespionage Attacks
Chinese ‘Gallium’ Hackers Using New PingPull Malware in Cyberespionage Attacks