The zero-working day exploitation of a now-patched medium-security flaw in the Fortinet FortiOS operating process has been connected to a suspected Chinese hacking team.
Threat intelligence business Mandiant, which made the attribution, said the action cluster is aspect of a broader campaign intended to deploy backdoors on to Fortinet and VMware options and preserve persistent access to sufferer environments.
The Google-owned threat intelligence and incident reaction organization is monitoring the destructive operation underneath its uncategorized moniker UNC3886, a China-nexus danger actor.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“UNC3886 is an superior cyber espionage group with special capabilities in how they run on-network as properly as the instruments they make use of in their campaigns,” Mandiant scientists stated in a technological examination.
“UNC3886 has been noticed targeting firewall and virtualization systems which deficiency EDR assistance. Their ability to manipulate firewall firmware and exploit a zero-working day suggests they have curated a deeper-level of knowing of these kinds of systems.”
It’s worthy of noting that the adversary was formerly tied to a different intrusion set focusing on VMware ESXi and Linux vCenter servers as part of a hyperjacking marketing campaign designed to fall backdoors this sort of as VIRTUALPITA and VIRTUALPIE.
The most up-to-date disclosure from Mandiant arrives as Fortinet discovered that federal government entities and significant corporations were being victimized by an unknown danger actor by leveraging a zero-working day bug in Fortinet FortiOS software program to final result in facts loss and OS and file corruption.
The vulnerability, tracked as CVE-2022-41328 (CVSS rating: 6.5), fears a path traversal bug in FortiOS that could lead to arbitrary code execution. It was patched by Fortinet on March 7, 2023.
In accordance to Mandiant, the attacks mounted by UNC3886 focused Fortinet’s FortiGate, FortiManager, and FortiAnalyzer appliances to deploy two various implants this kind of as THINCRUST and CASTLETAP. This, in change, was made attainable owing to the point that the FortiManager device was uncovered to the internet.
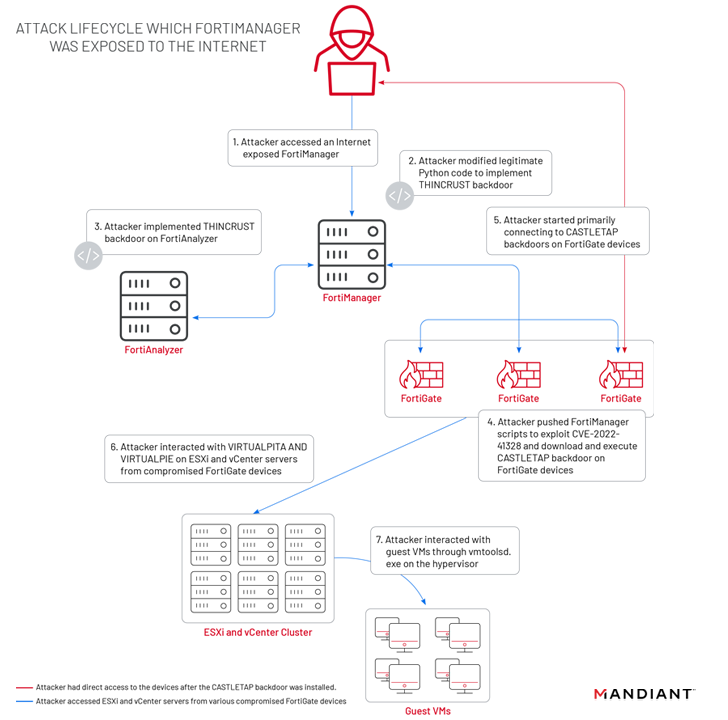
THINCRUST is a Python backdoor able of executing arbitrary instructions as properly as reading through and creating from and to documents on disk.
The persistence afforded by THINCRUST is subsequently leveraged to deliver FortiManager scripts that weaponize the FortiOS route traversal flaw to overwrite respectable documents and modify firmware visuals.
This includes a freshly extra payload known as “/bin/fgfm” (referred to as CASTLETAP) that beacons out to an actor-controlled server so as to acknowledge incoming instructions that allow for it to run commands, fetch payloads, and exfiltrate information from the compromised host.
“As soon as CASTLETAP was deployed to the FortiGate firewalls, the danger actor related to ESXi and vCenter machines,” the researchers spelled out. “The menace actor deployed VIRTUALPITA and VIRTUALPIE to set up persistence, allowing for continued accessibility to the hypervisors and the guest devices.”
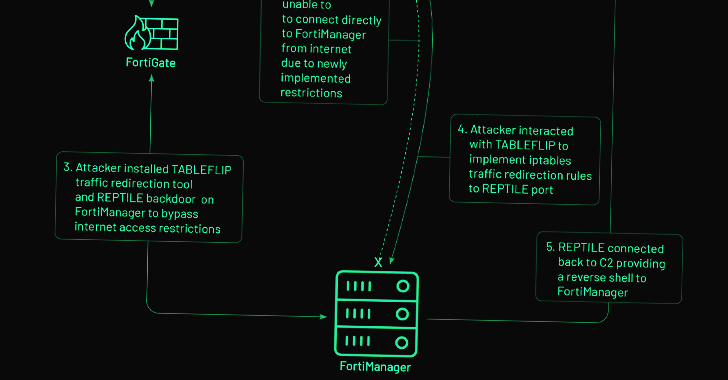
Alternatively, on FortiManager gadgets that put into action internet access limits, the danger actor is mentioned to have pivoted from a FortiGate firewall compromised with CASTLETAP to fall a reverse shell backdoor named REPTILE (“/bin/klogd”) on the network management technique to get back entry.
WEBINARDiscover the Concealed Potential risks of Third-Party SaaS Applications
Are you knowledgeable of the threats involved with 3rd-party app obtain to your firm’s SaaS applications? Be a part of our webinar to master about the sorts of permissions staying granted and how to limit risk.
RESERVE YOUR SEAT
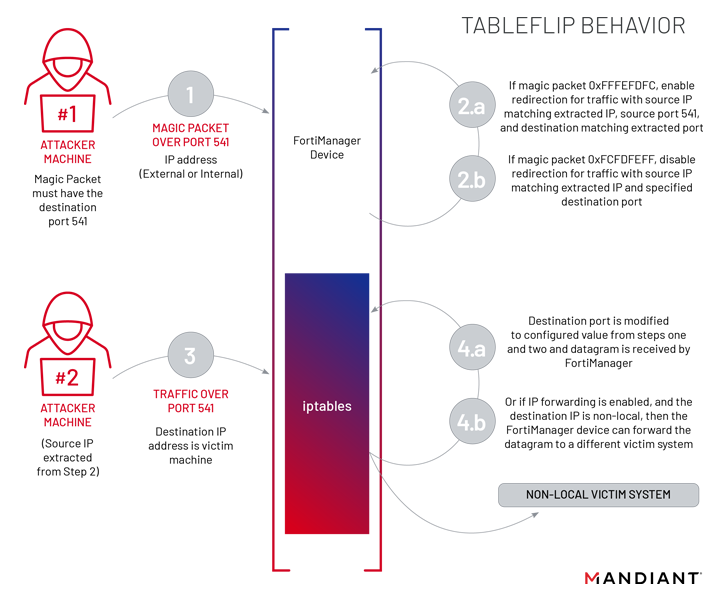
Also utilized by UNC3886 at this phase is a utility dubbed TABLEFLIP, a network traffic redirection software program to connect straight to the FortiManager system regardless of the accessibility-control listing (ACL) rules place in put.
This is much from the very first time Chinese adversarial collectives have specific networking machines to distribute bespoke malware, with current attacks getting advantage of other vulnerabilities in Fortinet and SonicWall equipment.
The revelation also comes as menace actors are building and deploying exploits a lot quicker than ever right before, with as quite a few as 28 vulnerabilities exploited within just 7 days of community disclosure — a 12% increase more than 2021 and an 87% rise in excess of 2020, according to Quick7.
This is also significant, not the very least since China-aligned hacking crews have turn out to be “specifically proficient” at exploiting zero-working day vulnerabilities and deploying customized malware to steal consumer credentials and manage lengthy-time period obtain to focus on networks.
“The exercise […] is additional evidence that advanced cyber espionage threat actors are having advantage of any technology available to persist and traverse a target atmosphere, in particular all those systems that do not support EDR solutions,” Mandiant stated.
Located this write-up interesting? Stick to us on Twitter and LinkedIn to go through far more exclusive written content we post.
Some pieces of this write-up are sourced from:
thehackernews.com

 Pompompurin Unmasked: Infamous BreachForums Mastermind Arrested in New York
Pompompurin Unmasked: Infamous BreachForums Mastermind Arrested in New York