The notorious Emotet malware, in its return after a small hiatus, is now currently being dispersed via Microsoft OneNote email attachments in an attempt to bypass macro-based mostly security restrictions and compromise devices.
Emotet, joined to a danger actor tracked as Gold Crestwood, Mummy Spider, or TA542, carries on to be a potent and resilient risk inspite of tries by regulation enforcement to acquire it down.
A derivative of the Cridex banking worm – which was subsequently replaced by Dridex all-around the exact time GameOver Zeus was disrupted in 2014 – Emotet has progressed into a “monetized platform for other threat actors to run malicious strategies on a pay back-per-set up (PPI) design, enabling theft of sensitive data and ransom extortion.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Even though Emotet bacterial infections have acted as a conduit to deliver Cobalt Strike, IcedID, Qakbot, Quantum ransomware, and TrickBot, its return in late 2021 was facilitated by signifies of TrickBot.
“Emotet is recognised for prolonged intervals of inactivity, frequently taking place numerous instances per 12 months, where the botnet maintains a constant-condition but does not produce spam or malware,” Secureworks notes in its profile of the actor.
The dropper malware is generally distributed by spam email messages made up of malicious attachments. But with Microsoft getting techniques to block macros in downloaded Business office data files, OneNote attachments have emerged as an attractive option pathway.
“The OneNote file is simple but yet helpful at social engineering users with a bogus notification stating that the document is guarded,” Malwarebytes disclosed in a new warn. “When instructed to double-click on on the Check out button, victims will inadvertently double-simply click on an embedded script file in its place.”
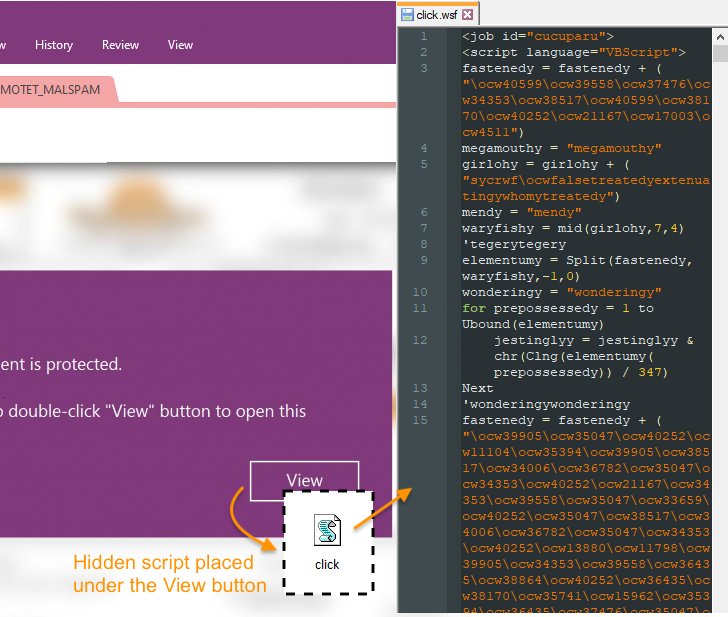
The Windows Script File (WSF) is engineered to retrieve and execute the Emotet binary payload from a remote server. Similar results have been echoed by Cyble, IBM X-Drive, and Palo Alto Networks Unit 42.
That mentioned, Emotet nonetheless carries on to use booby-trapped documents containing macros to produce the destructive payload, using social engineering lures to entice people into enabling macros to activate the attack chain.
WEBINARDiscover the Concealed Potential risks of Third-Party SaaS Applications
Are you mindful of the pitfalls affiliated with third-party app entry to your firm’s SaaS applications? Sign up for our webinar to learn about the sorts of permissions staying granted and how to limit risk.
RESERVE YOUR SEAT
These files have been observed to leverage a method named decompression bomb to conceal a extremely big file (above 550 MB) within just ZIP archive attachments to fly less than the radar, in accordance to a number of experiences from Cyble, Deep Intuition, Hornetsecurity, and Trend Micro.
This is obtained by padding 00-byte at the conclude of the document to artificially inflate the file dimensions so as to exceed the limitations imposed by anti-malware alternatives.
The latest advancement is a signal of the operators’ overall flexibility and agility in switching attachment types for original delivery to evade detection signatures. It also will come amid a spike in danger actors using OneNote paperwork to distribute a large array of malware this kind of as AsyncRAT, Icedid, RedLine Stealer, Qakbot, and XWorm.
In accordance to Trellix, a majority of the malicious OneNote detections in 2023 have been described in the U.S., South Korea, Germany, Saudi Arabia, Poland, India, the U.K., Italy, Japan, and Croatia, with production, significant-tech, telecom, finance, and power emerging as the top targeted sectors.
Identified this report exciting? Observe us on Twitter and LinkedIn to read through extra unique material we write-up.
Some areas of this write-up are sourced from:
thehackernews.com

 Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack